Meet the SOC Weekly Reports, a New Way to Inform Customers
One of the most comprehensive services offered by Wuerth-Phoenix’s Cyber Security team is the Security Operation Center (SOC). An SOC is capable of monitoring an IT environment, scanning all messages sent within the internal network, and all operations performed on corporate devices. Through the use of detection rules, the SOC is able to identify anomalies and malicious behavior and raise alerts, which are then checked and analyzed by the team of SOC analysts. The rules are optimized and properly tuned according to the technologies of the end client being monitored.
The SOC analyst’s job is to investigate the alerts generated by the rules and inform the client if something requires his or her attention. In case of critical events they contribute along with the customer to solving the problem as soon as possible and mitigating any damage. To provide the best protection, an SOC must be active 24/7 and keep up with the TTPs (Tactics Techniques Procedures) of threat actors.
SOC monthly reports
To keep the customer informed of SOC activities, Wuerth Phoenix produces and delivers various reports on a monthly basis, such as:
- Monthly SOC reports
- Monthly SOC ADS reports
- Monthly VA reports
These reports contain information on the status of the monitored company over the past month, with all operations performed by SOC analysts, such as alerts and tickets handled. Not only that, there is also information about cybercriminal activities, ransomware attacks, security bulletins, newly discovered vulnerabilities, and more. We monitor the activity of system administrators too, with the number of logins, logouts and failed logins and the machines used by administrators. A monthly Vulnerability Assessment is also performed, and details of all vulnerabilities identified on the client’s public perimeter are documented.
SOC weekly reports
Currently we have introduced a new, simpler, weekly report, with some details about malicious IP addresses contacted by internal IPs. This may be only the first in a series of documents reported weekly, in order to detail to our customers our continuous protective activities on their behalf.
Compared to the monthly reports, the structure of this one is rather simple, as shown in this example:
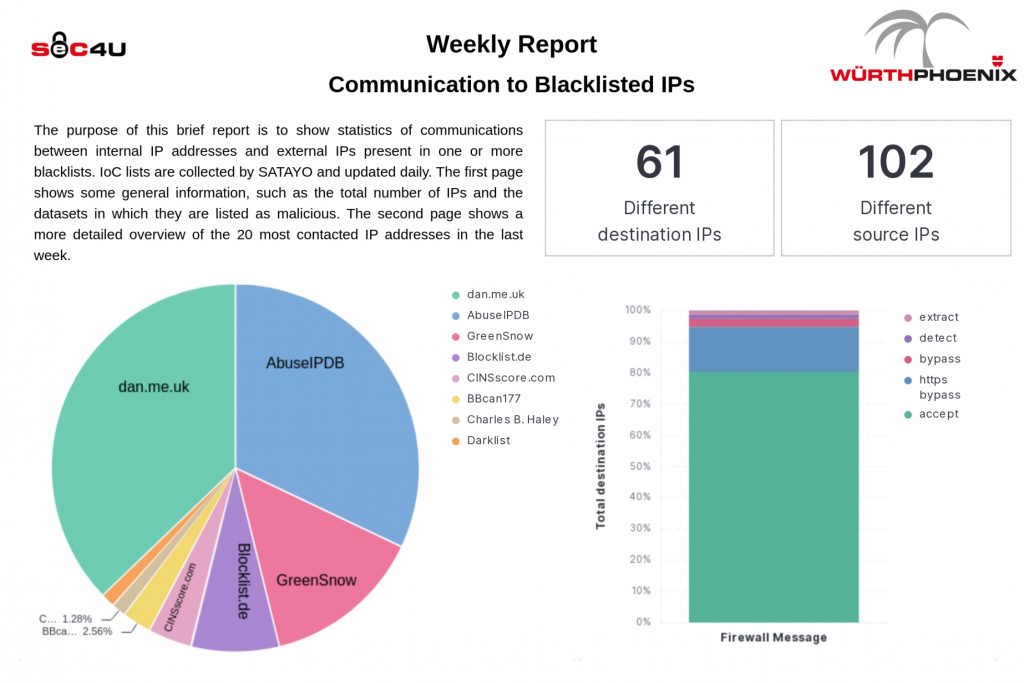
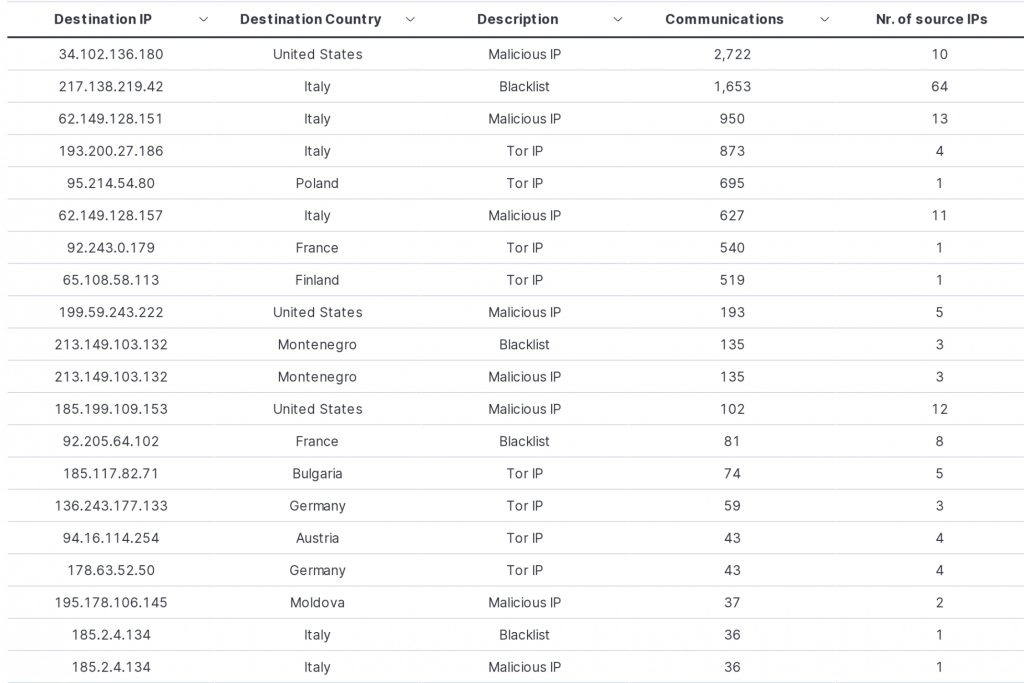
As you can see in the example above, the number is quite high, but that shouldn’t scare us! It often happens that these IPs belongs to hosting companies that host multiple domains under the same address. So, if one of its websites misbehaves, the IP ends up on a blacklist and the other legitimate websites on that same hosting company are also marked as “bad“. This is one of the reasons why an analysis is always necessary. SOC analysts won’t open a ticket for a customer if the contacted domain is legitimate, even if it’s on a blacklist.
In addition, we can notice that half of the IPs are classified as TOR IPs. Thus, they are present in the list because they were used as exit nodes for Tor communications, not necessarily for attacks conducted against other targets.
Small reports like the one shown here are easy to read, quick to understand, and can give us an overview of the situation. A more detailed analysis is always recommended to further and better investigate the scope of the communications.
These Solutions are Engineered by Humans
Did you learn from this article? Perhaps you’re already familiar with some of the techniques above? If you find security issues interesting, maybe you could start in a cybersecurity or similar position here at Würth Phoenix.







