Microsoft Icinga2 Agent Deployment Automation with Tornado and NATS
As a NetEye user I might want to install a Remote Host Agent that belongs to a Zone that can’t communicate directly with the Master. So to be able to do this, we decided to use Tornado and NATS. Linking with Patrick’s article in this article I’ll explain how to configure them.
What we want to do is collect events from an Agent on a Satellite with a Tornado Webhook Collector, and then send them to the Tornado Engine running on the Master machine that will generate an event to create the Host Object of that Agent on Director, while the Powershell Script will do the other tasks (certificate generation, satellite selection, etc.) The communication must go through a secured NATS connection for a multi-tenancy architecture.
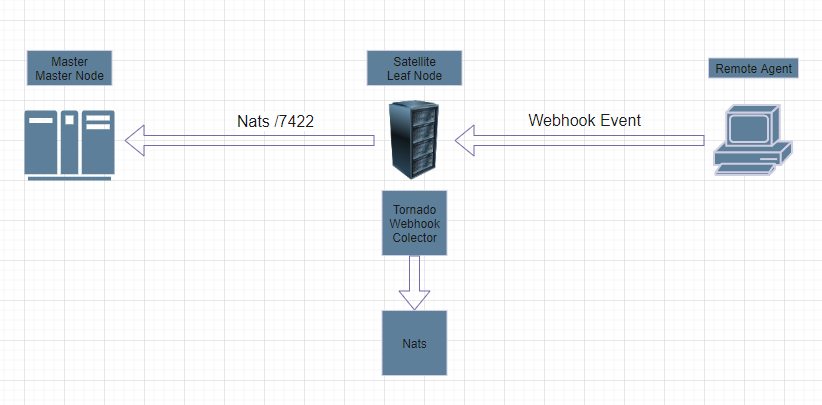
The architecture we see in this picture is very simple. During installation through a Powershell Script, the Agent will generate an Event to the Satellite, which will then be filtered and forwarded to the Master Node through NATS. All events that come from the Agent (as a Tornado Event) will be moved to the Master through a reverse rule proxy set in the HTTPD Service, while a proxy rule will transform HTTPS Tornado (433) requests to HTTP on the local Satellite (8080).
##tornado-webhook-collector.conf##
SSLProxyEngine on
ProxyPass /tornado/webhook/ http://httpd.neteyelocal:8080/
ProxyPassReverse /tornado/webhook/ http://httpd.neteyelocal:8080/##neteye-zones-proxy.conf##
ProxyRequests Off
ProxyPreserveHost On
SSLProxyEngine On
SSLProxyVerify none
SSLProxyCheckPeerExpire off
SSLProxyCheckPeerCN off
SSLProxyCheckPeerName off
ProxyPass /neteye/director https://pbzneteye4.wp.lan/neteye/director
ProxyPassReverse /neteye/director https://pbzneteye4.wp.lan/neteye/director
ProxyPass /neteyeshare https://pbzneteye4.wp.lan/neteyeshare
ProxyPassReverse /neteyeshare https://pbzneteye4.wp.lan/neteyeshare
<Proxy *>
allow from all
</Proxy>
Once the event from the Agent arrives at the Master, Tornado works as the Satellite filtering and processing the Event.
##Tornado Webhook Filter (the same on Master and Satellite)##
{
"id": "hsg",
"token": "icinga",
"collector_config": {
"event_type": "hsg",
"payload": {
"data": "${@}"
}
}
}
The NetEye 4 Tornado event processing engine comes with a series of collectors able to “listen” for incoming events. Those events are then processed by the Tornado engine.
Filter:
{
"type": "AND",
"operators": [
{
"type": "equals",
"first": "${event.type}",
"second": "hsg"
}
]
}Ruleset:
{
"type": "AND",
"operators": [
{
"type": "regex",
"regex": ".*generic-agent.*",
"target": "${event.payload.data.host_template}"
}
]
}[
{
"id": "director",
"payload": {
"action_name": "create_host",
"action_payload": {
"address": "${event.payload.data.host_address}",
"display_name": "${event.payload.data.display_name}",
"imports": "${event.payload.data.host_template}",
"object_name": "${event.payload.data.host_name}",
"object_type": "object",
"vars": {
"created_by": "tornado"
}
},
"icinga2_live_creation": false
}
}
]Finally the result is both a Host Object and a Service Object running directly in NetEye.