In this article we will see together how to perform an analysis of a site present on the Dark Web and more precisely of a site present within the Tor network. Our point of reference will be the site of the Avos ransomware gang, which has just started its cyber criminal activity a few weeks ago.
What is the url of the Avos website?
The site can be reached at the address https://avos2fuj6olp6x36.onion and to access the site you need to use the Tor browser.
Installing the Tor browser
To install the Tor browser you can go to https://www.torproject.org/download/ and download for the package for your operating system. If you are using a Linux Debian or derived distribution, you can use the following commands:
sudo add-apt-repository ppa:micahflee/ppa
sudo apt update
sudo apt install torbrowser-launcher
When finished, you can run the Tor browser and access the Avos website url.
Now that we can access the Tor network, we might ask ourselves how we can deeply analyze a site with an onion extension, for example to verify the ports and services exposed by it or to identify the technologies used.
The answer lies in the use of any tools that are classically used to analyze websites outside the Tor network, redirecting their traffic within the channel managed by the previously installed Tor service.
To achieve this we can use a tool called socat.
What is socat?
The socat utility is a relay for bidirectional data transfers between two independent data channels.
There are many different types of channels that socat can connect, including:
- Files
- Pipes
- Devices (serial line, pseudo-terminal…)
- Sockets (UNIX, IP4, IP6 – raw, UDP, TCP)
- SSL sockets
- Proxy CONNECT connections
- File descriptors
- Programs
- Combinations of two or more of these
We can then install the tool:
sudo apt install socat
We can then activate a communication channel, which will connect the Tor service with a socket to which we will connect to carry out our analysis activities.
socat TCP4-LISTEN:8080,reuseaddr,fork SOCKS4A:127.0.0.1:avos2fuj6olp6x36.onion:80,socksport=9050
In this specific case, the communication channel will be listened to on port 8080 and will connect us to the onion site of the Avos group through port 9050 (where the Tor service, by default, listens).
Let’s analyze the surface!
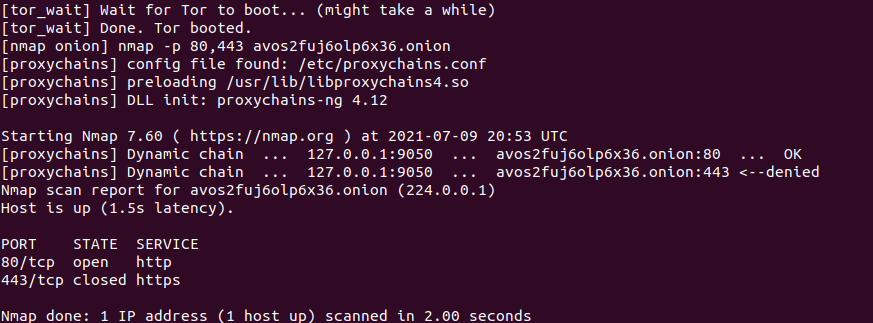
It can be interesting to understand which ports an onion site is exposed. To find out this information, we can use a tool, docker-onion-nmap, that Miles Richardson has been making available to the community for some years now. The convenience of this tool is that it is made available in the form of a Docker image. The tool integrates uses several tools, such as nmap, proxychains, nc and tor to achieve its goal.
To perform the scan, we simply need to run the following command:
sudo docker run --rm -it milesrichardson/onion-nmap -p 80,443 avos2fuj6olp6x36.onion
The command output will look like this:
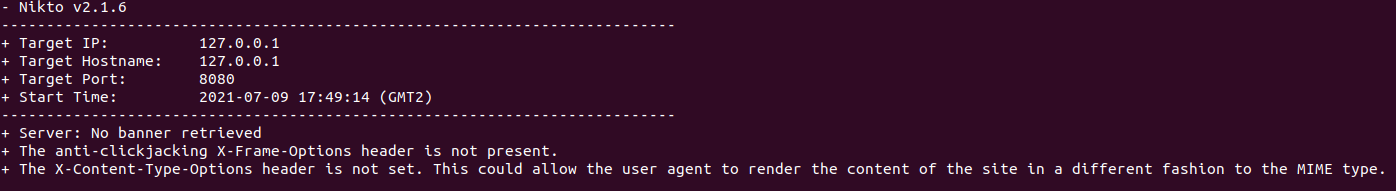
We can now therefore use a tool such as nikto to carry out an audit of the Avos group’s web server. The scan will be directed to the communication channel that we have just established with the socat command.
Nikto is able, where possible, to retrieve the banner displayed by the web server, some interesting paths that may be displayed, the content of the robots.txt file and many other information that may be useful during the analysis activities.
We can install it on our system using the following command:
git clone https://github.com/sullo/nikto
We then run nikto on our target:
cd nikto-master/program
nikto -h 127.0.0.1:8080
The command output will look like this:
Another tool that we can use, to better check the paths exposed by the web server, is DIRB.
DIRB is a Web Content Scanner. It looks for existing (and/or hidden) Web Objects. It basically works by launching a dictionary based attack against a web server and analyzing the responses. . DIRB comes with a set of preconfigured attack wordlists for easy usage but you can use your custom wordlists.
We can install it on our system using the following command:
sudo apt install dirb
We then run nikto on our target:
dirb http://127.0.0.1:8080 /usr/share/dirb/wordlists/common.txt
The command output will look like this:
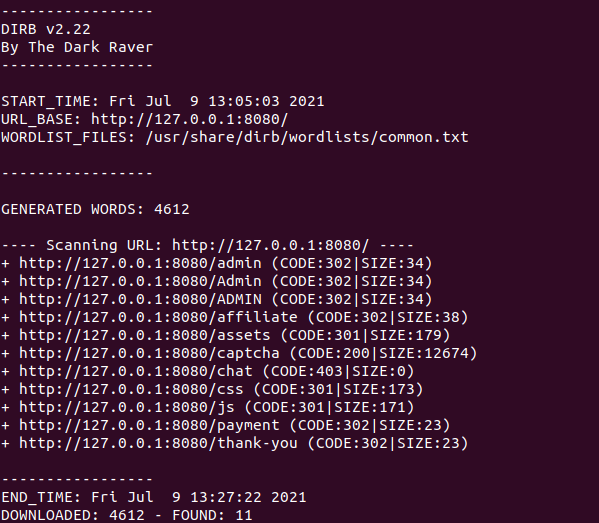
As we can see, DIR allowed us to discover several interesting paths, including a site administration interface and a page that allows affiliates to interact with the ransomware gang.
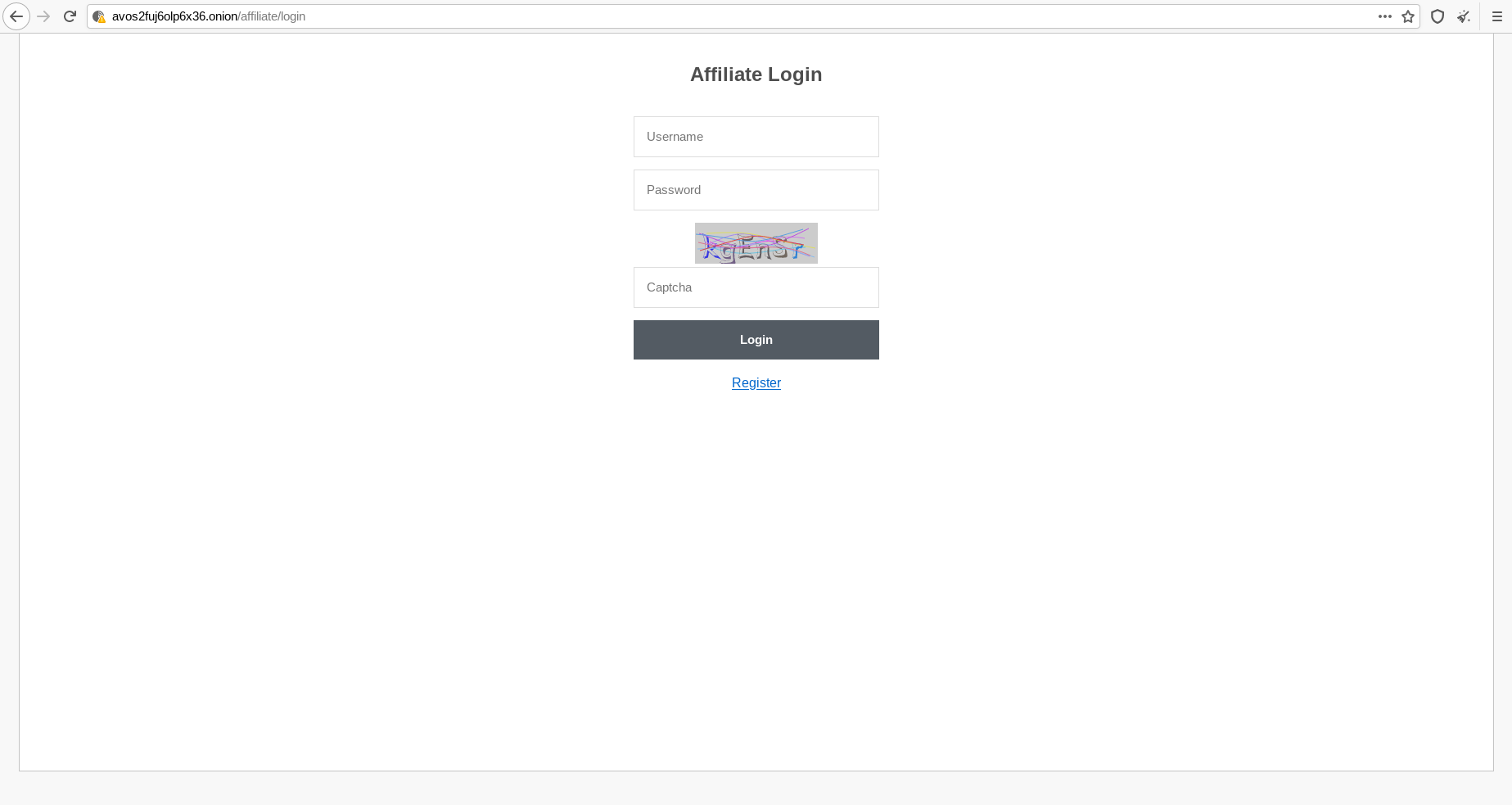
The analysis of a dark web site can also concern further activities, such as verifying the paths of visible elements within the site structure, such as images, captchas, favicons, code.
These elements can very often lead to the correlation of cybercriminal groups with other affiliated groups.







