Setting up a Vulnerability Enrichment Process: Prioritizing Risks Effectively
In the context of vulnerability management, it’s common to be faced with a long list of findings after each scan, often too many to tackle all at once.
But how do you decide where to focus your efforts and resources?
Which vulnerabilities are truly critical, the ones that could actually compromise your organization’s security?
The Challenge of Traditional Vulnerability Management
Automatic scanning tools detect vulnerabilities along with contextual information.
However, this alone is not enough to support informed and effective prioritization. As a result, security teams often find themselves overwhelmed by an endless list of issues, unsure where to focus their remediation efforts.
Enriching vulnerability data with broader contextual information, including company-specific insights, enables more targeted response and optimized allocation of security resources.
The Enrichment Process: Adding Insights
Enriching the vulnerability data with insights about the company or the affected hosts provides a concrete understanding of where action is needed. Let’s walk through the key elements:
- Public Exposure: Knowledge of the public exposure of affected hosts represents an additional layer of assessment. A vulnerable system, even if isolated from the external network, may have much less risk than one directly exposed on the Internet. Integration with asset discovery data, firewalls, and monitoring systems allows assessment of the true attack surface.
- Threat Intelligence and Exploits available: Knowledge of public exploits and PoCs (Proofs of Concept) publicly available on the Deep and Dark Web, along with how much a vulnerability is mentioned or talked in Threat Intelligence channels, increases the risk associated with a vulnerability. The enrichment of this information makes it possible to assess the ease with which an attacker could exploit a specific vulnerability.
- Dynamic Risk Assessment (KEV, EPSS): These represent metrics that vary over time. The KEV (Known Exploited Vulnerabilities) catalog, maintained by CISA, identifies vulnerabilities already being actively exploited by attackers in the real world, providing insights based on real-world threats. EPSS (Exploit Prediction Scoring System) provides an estimate of the likelihood that a vulnerability will be exploited in the future, helping to predict attack trends and anticipate mitigation.
What We’re Working On
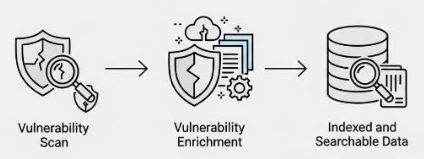
This is basically what we’re doing in the Würth Group, starting from detections generated by daily vulnerability scanning activities. After the scans end, the resulting data is indexed in an Elastic instance providing a place that’s easily searchable for the data of interest.
Upon a detection, an enrichment process we’ve developed follows the steps described in order to add context to the huge amount of data obtained and indexed. This process runs periodically (more often during the day) in order to cover each record from the continuous scans.
As the main source of enrichment we use mainly SATAYO, our internally developed CTI platform where the information reported is already integrated, updated and easily available. For public exposure instead, mappings start from files containing NAT information.
Finally, based on these results a Remediation Priority Index is calculated to truly assess the criticality of a given vulnerability and/or host.
Now the question becomes how to use this data to improve decision making about which vulnerabilities to remediate?
The enrichment data is pushed to Elastic fields created ad-hoc for this purpose, and at the vulnerability to which they refer. In this way, data can be used retrospectively, for creating reports with statistical and aggregated data, or for producing a general overview of the situation given a host or company.
Benefits of Vulnerability Enrichment and Final Considerations
It’s straightforward to talk about the benefits, since it’s clear how enrichment creates order within the mess and the infinite vulnerabilities arising from automatic vulnerability scans.
Many companies simply assess vulnerabilities based solely on the severity assigned by CVSS (Common Vulnerability Scoring System). However, not all vulnerabilities with high scores pose an immediate risk, especially when the hosts involved are not directly exposed to the public on the Internet and thus the vulnerability is directly exploitable.
To conclude, vulnerability enrichment can bring to your company:
- Effective prioritization: Focusing efforts on those vulnerabilities most relevant to your specific circumstances
- Real risk reduction: Acting first on active threats and critical systems
- Better resource allocation: Optimizing the security team’s time and budget
- Strategic decision support: Providing accurate, updated data that helps determine patching roadmaps and mitigations
Indexing enrichment data with their respective vulnerabilities provides a rich source of data for more optimized information search, and a source for building dashboards or reports to share with those directly involved in the process, letting you improve and speed up the decision making and mitigation process.
These Solutions are Engineered by Humans
Did you learn from this article? Perhaps you’re already familiar with some of the techniques above? If you find cybersecurity issues interesting, maybe you could start in a cybersecurity or similar position here at Würth Phoenix.







