Around this time last year, I wrote a blog post about improving cybersecurity with Elastic Defend. Now, one year later, we’ve gained a lot of practical experience with it, which I’d like to share.
Elastic Defend is an EDR (Endpoint Detection and Response). Unlike a traditional antivirus solution that relies on signature patterns that need to be updated regularly, Elastic Defend works based on rules.
These rules are integrated both in the Elastic Defend agent, which runs on the clients, and as detection rules that operate on the central system to identify alerts. This has the great advantage that attacks can be detected through correlations of events.
In other words, alerts are triggered as soon as events generated by malware programs occur – for example, when malware is copied to the system, or when it starts executing actions, and so on.
The client uses YARA rules to detect malware (https://github.com/elastic/protections-artifacts). The client updates these rules from the internet, or you can specify custom URLs from which the client can download updates. This is a frequently asked question, as not all clients are allowed internet access.
In the following image, you can see the settings in the Defend integration, where the URL can be defined:
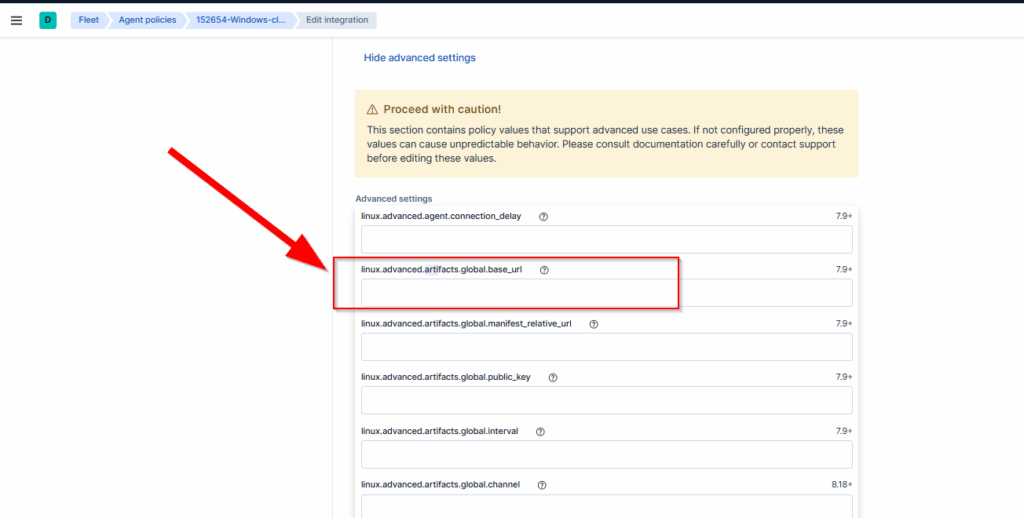
If the download of YARA rules on the client doesn’t work, you’ll see it in the client logs within Fleet Management.
We recommend creating a detection rule in Kibana so that you are notified in time if such a situation occurs. Unfortunately, the current Elastic version does not yet include such a rule by default.
Among the detection rules, there is one called “Endpoint Security (Elastic Defend)” which you need to activate:
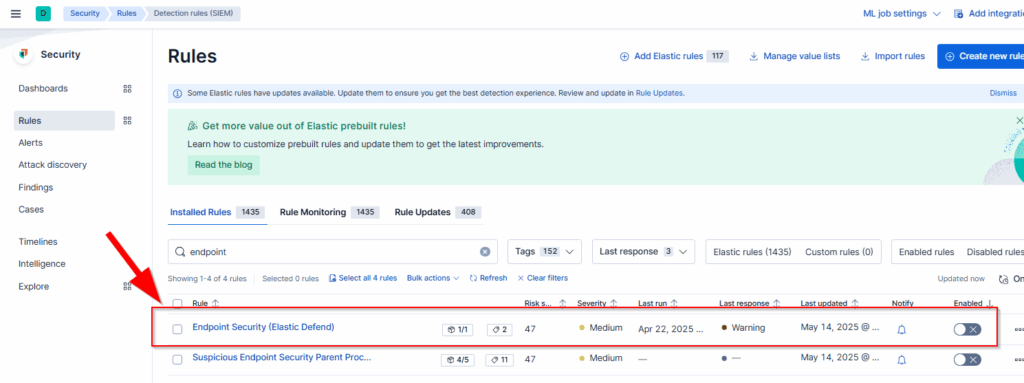
This rule triggers alerts from Elastic Defend and displays them in the Alerts overview under Kibana → Security.
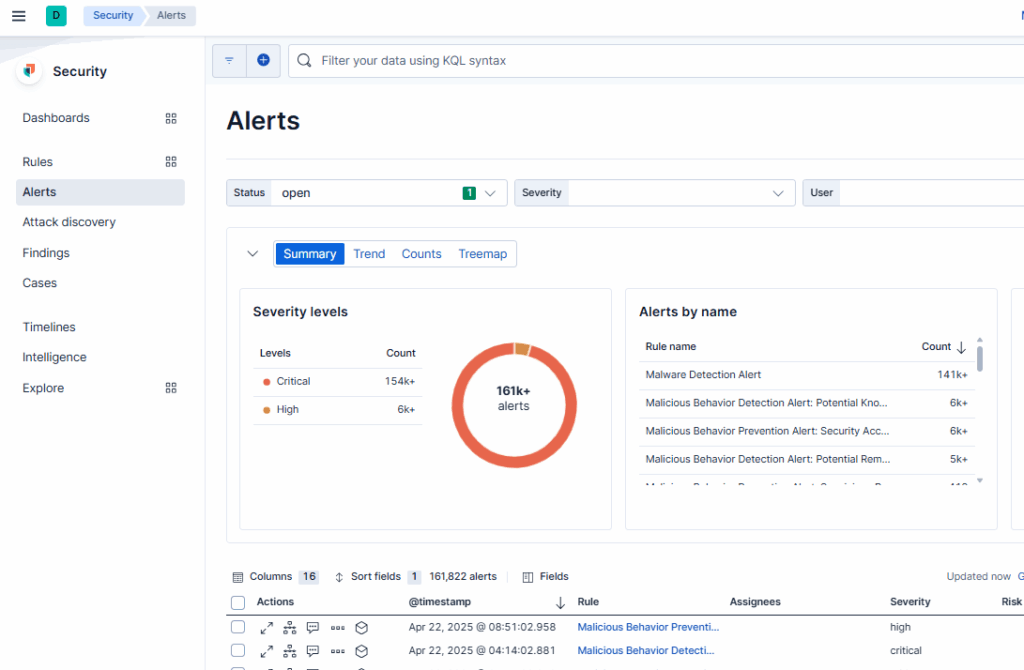
If you want to trigger additional or specific actions based on these alerts, you’ll need to create your own rules that perform the desired actions (e.g., send an email, create a Jira ticket, etc.).
With Elastic Defend, you can maintain blocklists, isolate clients, and terminate processes. Of course, you can also whitelist specific events and applications.
Naturally, Elastic Defend includes detections for all well-known types of malware – ransomware, memory threat protection, malicious behavior protection, and more.
In conclusion, I can report that we have already replaced one or two antivirus solutions with Elastic Defend. I wish you a lot of success and enjoyment in integrating and configuring Elastic Defend!
These Solutions are Engineered by Humans
Are you passionate about performance metrics or other modern IT challenges? Do you have the experience to drive solutions like the one above? Our customers often present us with problems that need customized solutions. In fact, we’re currently hiring for roles just like this as well as other roles here at Würth Did you find this article interesting? Does it match your skill set? Our customers often present us with problems that need customized solutions. In fact, we’re currently hiring for roles just like this and others here at Würth IT Italy..







