See What Outsiders See: The External Attack Surface Management Report
Organizations often struggle to understand how they truly appear from the outside. Security teams work hard to protect internal systems, yet the real exposure visible to potential attackers often remains unclear. That’s why we created the External Attack Surface Management (EASM) report. By delivering this report we want to provide a clear overview of the assessment process performed using the SATAYO Threat Intelligence Platform that shows each Business Partner of the Würth Group from an attacker’s perspective, and reports possible attack vectors.
Where visibility ends, risk begins
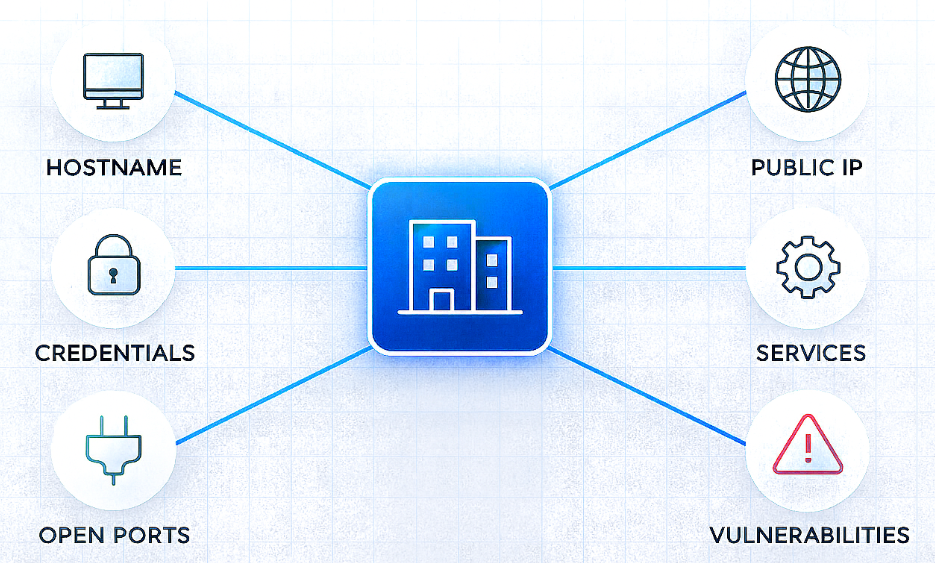
An organization’s external attack surface includes everything that is publicly exposed and accessible from the Internet and therefore visible to threat actors. This covers domains, host names, IP addresses, open ports, exposed files, leaked emails and credentials, sensitive data, vulnerabilities, and more. In short, it’s all the digital entry points an attacker might try to exploit.
The challenge is that the external attack surface constantly changes. New services go online, old systems are left behind, third-party providers can be compromised, and company data or credentials can be leaked without anyone noticing.
Understanding the external attack surface is essential, because you can’t protect what you don’t see. With clear visibility into all public-facing assets, organizations can reduce blind spots, focus on real risks, and improve their overall security.
The EASM report
Our solution to turn visibility into actionable insights is the External Attack Surface Management report created monthly for each Business Partner of the Würth Group and delivered together with the Vulnerability Management reports.
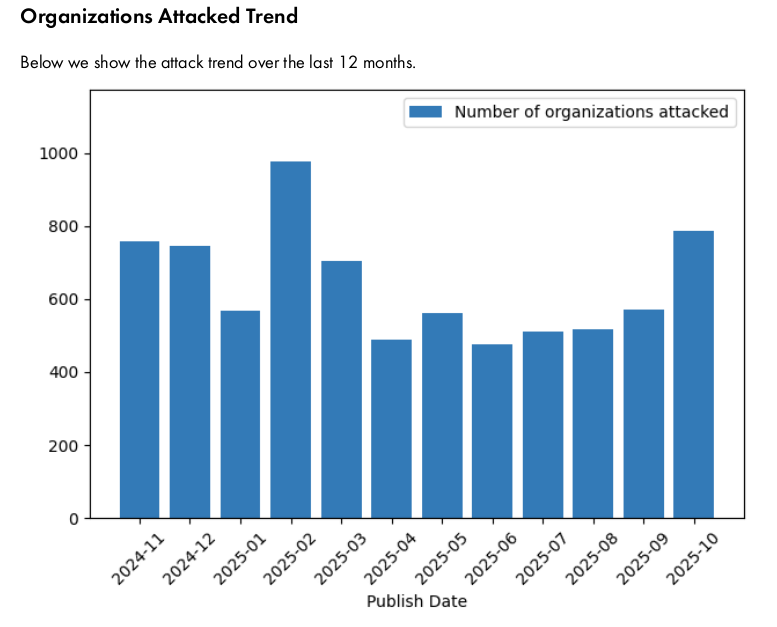
The report opens with a section designed to enhance stakeholders’ awareness of the current cyber-threat landscape. In particular, this section provides trends and insights related to double-extortion ransomware attacks, which have been continuously monitored within SATAYO since 2020.
As an example, we present data on organizations worldwide that have been publicly listed as victims of double-extortion ransomware on various data-leak sites, along with the key trends observed over the past 12 months.
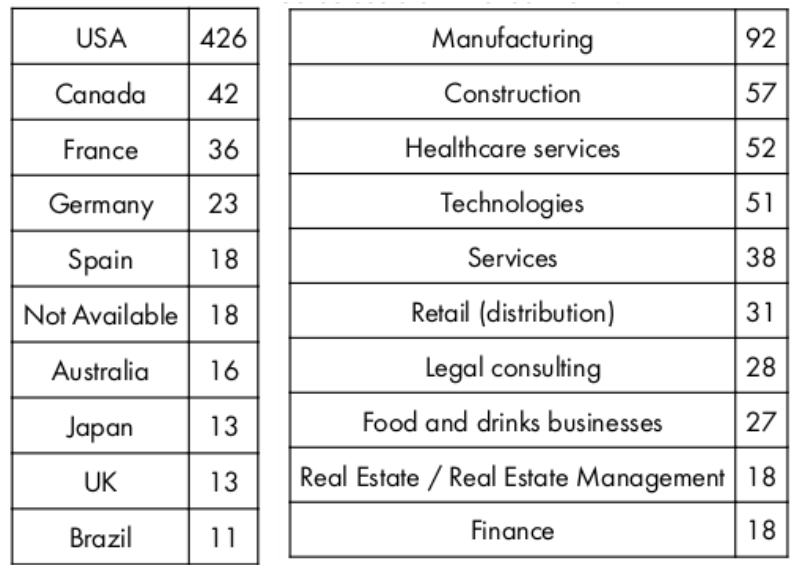
Another example focuses on showing insights about the top 10 most-attacked countries recorded in the last month, along with the 10 most-targeted industry sectors.
Then, the main section of the report focuses on the domains identified for each Business Partner. It provides detailed information showing the specific exposure associated with each domain, showing the Exposure Assessment Index Value (EAIV) calculated by SATAYO based on the evidence and the assets (i.e., host names, email accounts and IP).
This level of visibility supports decisions to ensure that only what is strictly necessary is publicly exposed, fostering a proactive and risk-aware approach.
Clarity today, better decisions tomorrow
The generation and delivery of custom reports provides several key benefits, including proactive risk reduction, enhanced threat-intelligence integration, and increased visibility. They also promote accountability, enabling each Business Partner to understand its own digital exposure and take ownership of remediation efforts.
The attack surface is inherently dynamic: new assets are introduced, acquisitions add complexity, and systems are sometimes retired improperly. Embedding this assessment into a continuous improvement cycle allows the organizations to adapt quickly to change and maintain a robust security posture over time. Clarity today empowers better decisions tomorrow.
These Solutions are Engineered by Humans
Did you learn from this article? Perhaps you’re already familiar with attack surfaces? If you find cybersecurity issues interesting, maybe you could start in a cybersecurity or similar position here at Würth IT Italy.







