NetEye – Icinga2 Execute Command API
In the last few weeks, we collaborated with the Icinga2 developers to create a new powerful API, called “Execute Command“.
The main purpose of this new API is to execute specific commands on a node by sending the request to the parent node. This is useful when the user cannot reach the desired node (an agent) from its network but can go through the parent node (a satellite or the master). This scenario is possible by taking advantage of the secure Icinga2 infrastructure already in place.
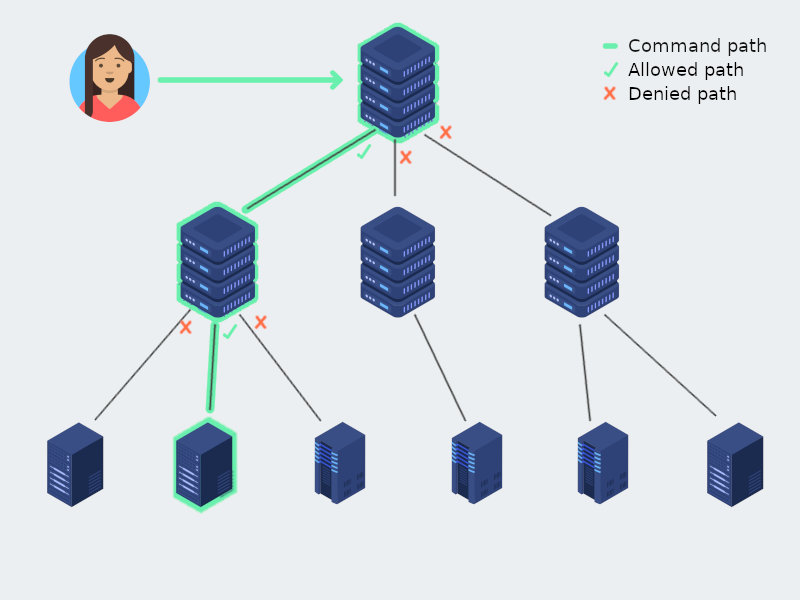
How It Works
The user, via the API, sends a request to the master saying that he wants to execute a specific command on the agent. The master at this point, after validating the request, forwards it to the satellites. When a satellite receives the execution request, it checks if the agent is part of its zone and forwards the request to the agent, otherwise it ignores the request. In the end, the agent receives the execution request, executes the command and sends back the result. Finally, the user is able to check the status of the execution and to retrieve the result.
Of course, it’s also possible to send an “execute command” request to a satellite or directly to an agent, as long as it is reachable.
Macro Override
Another point of strength is the ability to override all the command’s macros directly from the request. This feature allows us to test the desired command with different variable values and see what happens in each case.
An additional use of this feature is to create a custom check command that executes any shell commands, accepting them from the macros. Remember though that with great power comes great responsibility: in fact, this last example is an edge case and from a security point of view, it must be treated with special caution.
Next Steps
This was really a great collaboration between the two teams, resulting in the creation of the following pull requests:
- https://github.com/Icinga/icinga2/issues/8034
- https://github.com/Icinga/icinga2/pull/8040
- https://github.com/Icinga/icinga2/pull/8064
- https://github.com/Icinga/icinga2/pull/8107
- https://github.com/Icinga/icinga2/pull/8193
and soon as they are approved and merged, the new API will be available in Icinga2. As for NetEye, the API will already be available on NetEye 4.14 since we have built our own version of Icinga2.







