Cyber Threat Intelligence: Enrichment with SATAYO IoC
One of the important elements of Cyber Threat Intelligence activity is the verification of IoCs (Indicators of Compromise) that can identify threats that can create an impact on your organization.
In parallel to our OSINT and Cyber Threat Intelligence SATAYO platform we have implemented the SATAYO IoC database which currently has about 900,000 elements.
Among these are:
- IP addresses
- Domains
- URLs
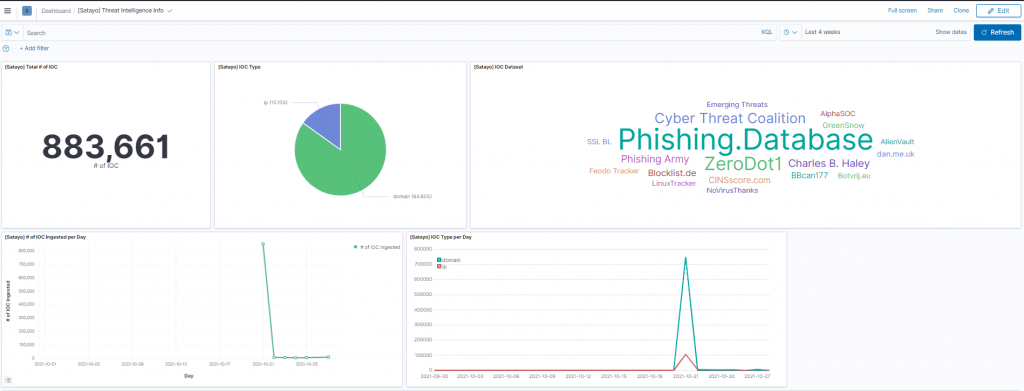
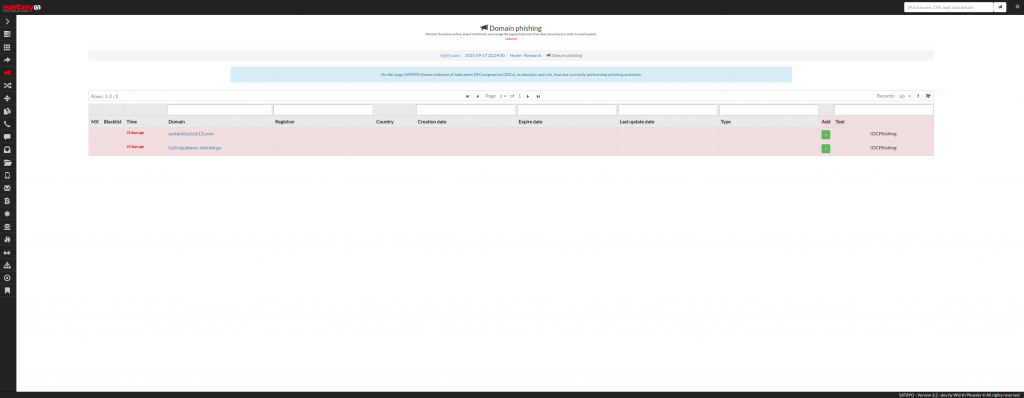
Using keywords connected to the organizations whose exposure we monitor and which we periodically update, we are therefore able to find any evidence, as in the case highlighted below, relating to 2 phishing domains:
In recent weeks we have worked a lot on the possibilities of integrating SATAYO IoC within NetEye SIEM and we are very proud to be able to show the results we’ve achieved.
First of all, a phase of daily reconstruction of the IoCs was implemented within SATAYO, which retrieves the various sources and creates a JSON file containing them.

An “Indicator Match” type detection rule was then created in NetEye SIEM, in which the source.ip and destination.ip fields were mapped.
Then there is a phase of ingestion of the records within an index.
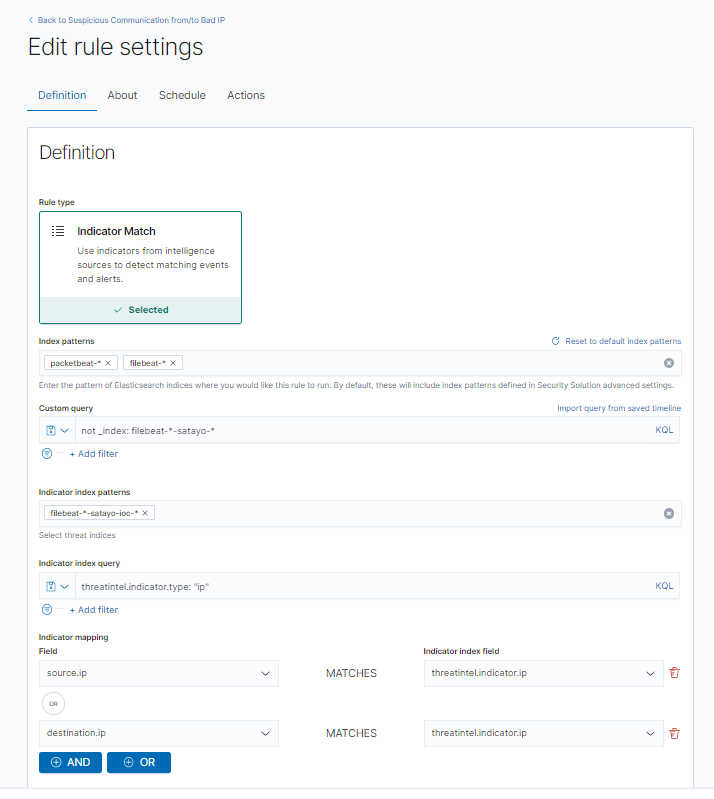
Finally, the various characteristics of the detection rule have been defined and a schedule (every 10 minutes) configured for the execution of the detection rule itself.
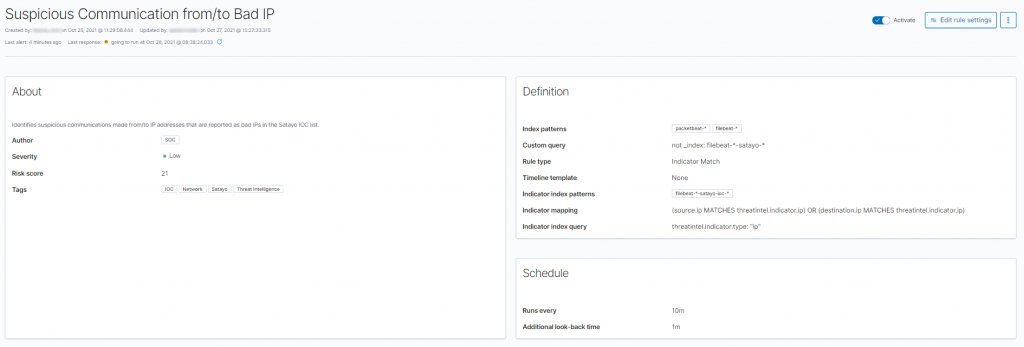
The execution of the detection rule therefore allows us to quickly identify the presence of connections with IP addresses present in the SATAYO IoC database.
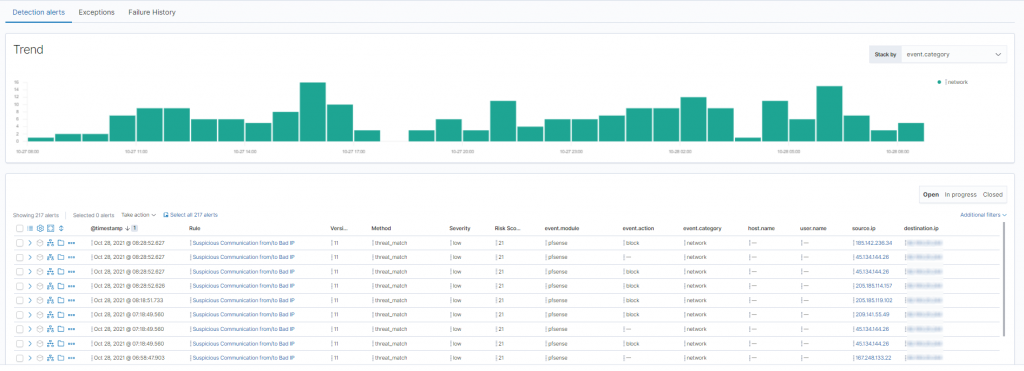
The Indicators of Compromise is just one of the integrations between SATAYO and NetEye that we have achieved to date. The implementation of the API (Application Programming Interface) within SATAYO has made it possible to also provide within NetEye SIEM all the different pieces of evidence collected by our OSINT and Cyber Threat Intelligence platform.
In our next posts we’ll show you these integrations, which allow the Cyber Security Analysts of the SOC (Security Operation Center) to obtain unprecedented visibility.






