Purple Teaming is a MUST, not a PLUS

In modern security programs the silos between offensive and defensive teams is no longer sustainable: attackers iterate faster, tooling evolves daily, and detection gaps are exploited in minutes, not months.
In this environment purple teaming is not an optional maturity enhancement, but it becomes a foundational requirement for organizations that take risk management seriously.
Purple teaming is the structured collaboration between red teams and blue teams with the explicit goal of improving detection, response, and resilience.
Unlike traditional adversarial exercises, purple teaming focuses on continuous feedback, shared objectives, and measurable defensive improvement.
At its core, purple teaming is an operational workflow where:
- Offensive techniques are mapped to specific detection hypotheses
- Attacks are executed transparently or semi transparently
- Telemetry is reviewed in near real time
- Detection logic is tuned during or immediately after execution
- Defensive coverage is measured against known attacker behaviors
Technical Value to Red Teams
For red teamers, purple teaming significantly increases the quality and impact of offensive operations.
- You gain visibility into what actually triggers alerts
- You understand which techniques are noisy versus invisible
- You can refine tradecraft based on real defensive telemetry
- You help prioritize detection gaps that matter, not theoretical ones
Most importantly, your work directly improves the organization’s security posture, rather than ending as a static report.
Technical Value to Blue Teams
For blue teams, purple teaming accelerates detection maturity in ways no vendor product can.
- Detection rules are validated against real attacker behavior
- False positives are reduced using known benign and malicious activity
- Logging gaps are identified and fixed with clear justification
- Response playbooks are exercised under realistic conditions
Instead of guessing what attackers might do, blue teams respond to what attackers are actually doing.
How to Start a Purple Teaming Program
To start a Purple Team program, it’s first necessary to understand the organization’s security maturity, objectives, and operational context. This ensures the engagement is aligned with existing processes and delivers measurable improvements.
Based on this assessment, different scenarios can be addressed:
When a SOC service is already in place, the Purple Team integrates with existing SOC operations to validate and improve detection and response capabilities, refine use cases, and test incident handling through coordinated attack simulations.
For organizations using a third-party SOC, the engagement focuses on defining clear communication and collaboration with the external provider, ensuring effective detection, escalation, and response during simulated attacks.
For customers without a SOC but with an internal Blue Team, the Purple Team concentrates on strengthening defensive capabilities by identifying visibility gaps, improving monitoring, and supporting the development of detection and response processes.
In all cases, a successful Purple Team engagement relies on clear objectives, close collaboration, and continuous feedback.
How a Purple Team Engagement Is Structured
A purple team engagement follows a structured and repeatable workflow designed to maximize collaboration between offensive and defensive teams while producing measurable defensive improvements.
Although the exact implementation may vary depending on the engagement model, the core phases remain consistent across different organizational contexts.
Phase 1: Kickoff and Alignment
The engagement begins with a kickoff meeting involving all relevant stakeholders, typically including the Red Team, Threat Intelligence, Blue Team, and, where applicable, an internal or third-party SOC.
The objectives of this phase are to:
- Align on the scope of the engagement and assets in scope
- Define the threat scenarios and attacker profiles to be simulated
- Clarify roles, responsibilities, and communication channels
- Agree on rules of engagement, transparency level, and safety constraints
- Establish success criteria and metrics for defensive validation
This phase ensures that all teams share a common understanding of goals and constraints before any technical activity begins.
Phase 2: Threat Intelligence–Driven Scenario Design
Based on the agreed-upon objectives, the Threat Intelligence Team provides context on relevant threat actors, campaigns, and commonly observed Tactics, Techniques, and Procedures (TTPs).
These inputs are used by the Red Team to design adversary simulation scenarios that reflect realistic attacker behavior rather than theoretical attack paths.
Each scenario is mapped to specific detection hypotheses, typically aligned with frameworks such as MITRE ATT&CK, allowing defensive coverage to be assessed in a structured and repeatable manner.
Phase 3: Controlled Execution of Adversary Simulations
The Red Team executes the defined scenarios in a controlled manner, following the agreed-upon rules of engagement.
Depending on the engagement model, the Blue Team or SOC may be fully aware, partially aware, or unaware of the simulations.
During execution:
- Attacker actions are documented and timestamped
- Defensive telemetry is observed in near real time
- Alerts, detections, and response actions are collected as evidence
Phase 4: Detection Review and Tuning
Following execution, Red and Blue teams collaboratively review the collected telemetry and detection outcomes.
This phase focuses on understanding which attacker techniques were detected, which were missed, and why.
Typical activities include:
- Analysis of logs and alerts related to executed techniques
- Identification of false positives and false negatives
- Tuning existing detection rules
- Creating new detection logic where gaps are identified
- Validating improvements through targeted re-testing
This iterative feedback loop is one of the key differentiators of purple teaming compared to traditional offensive exercises.
Phase 5: Debriefing and Knowledge Transfer
The engagement concludes with a structured debriefing session involving all stakeholders.
Results are reviewed against the initial objectives, and findings are translated into concrete improvement actions.
This phase typically includes:
- Review of detection coverage and response effectiveness
- Discussion of root causes for missed or delayed detections
- Prioritization of remediation activities
- Knowledge transfer between offensive and defensive teams
The debriefing ensures that technical findings are converted into actionable outcomes that can be tracked and implemented over time.
Below is an example of selected sections from a report produced by the Red Team following the adversary simulation phase of the engagement.
The document is shared with the other involved teams and used as a reference to support the debriefing session and subsequent analysis:
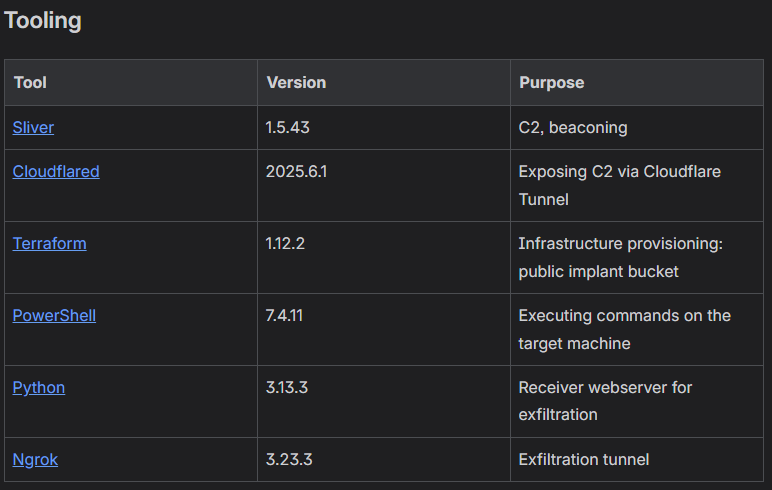
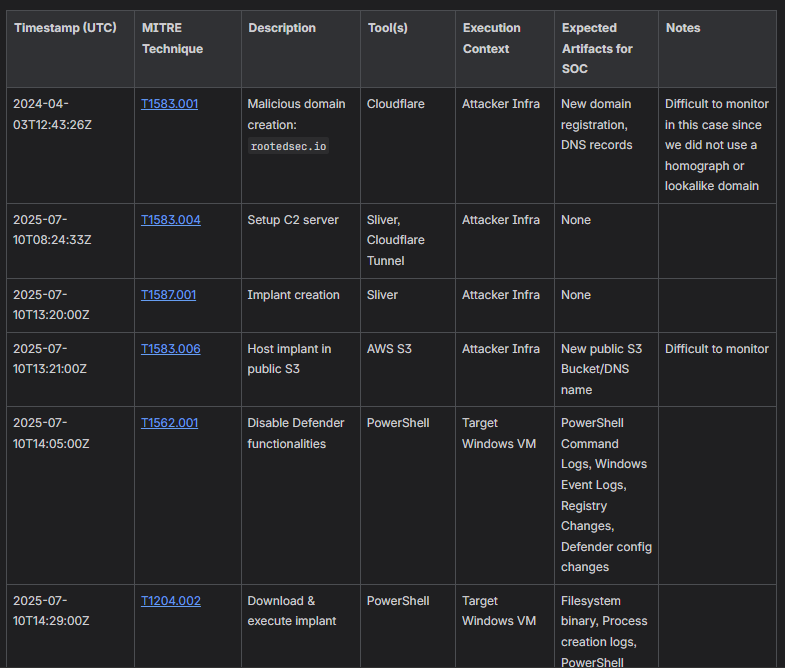
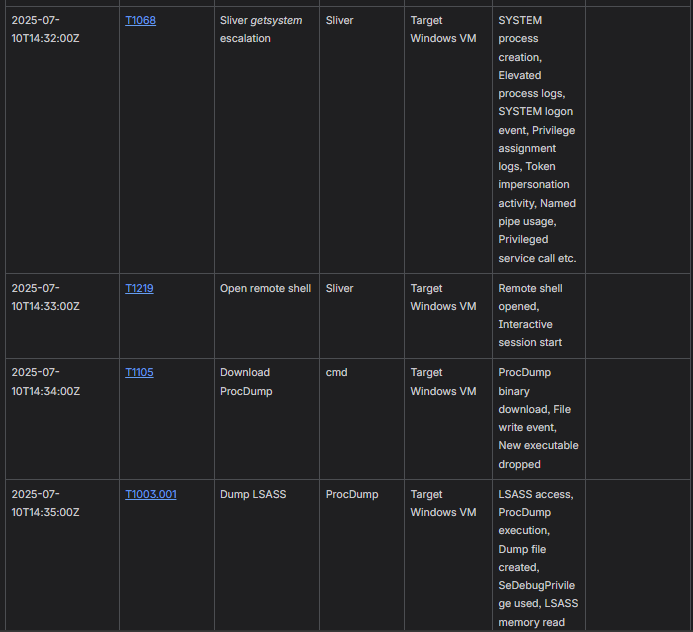
The Advantage of an Attacker-Centric SOC
The advantage of working in a well-structured attacker-centric SOC, such as the one in Würth IT Italy, lies in being able to carry out activities under optimal conditions, with professionals trained in both offense and defense.
For us, these activities serve as opportunities for research and development, allowing us to conduct deep dives into topics that we might not otherwise have the time or opportunity to explore.
They enable us to stay at the forefront of innovation in both offensive and defensive techniques, as well as to develop custom tooling tailored to our needs.
It’s precisely through these purple teaming activities that we developed and open-sourced Magnet, a Rust-based application that helps automate the testing of detection rules:
Conclusion
Purple teaming is not a luxury reserved for mature organizations.
In a threat landscape defined by speed and adaptation, organizations that fail to align offense and defense will always lag behind attackers: purple teaming closes that gap by turning adversary simulation into actionable defensive improvement.
It is not a plus. It is a must.







