In December 2021 Microsoft revealed two vulnerabilities concerning an Active Directory Domain Services privilege elevation, classified as CVE-2021-42278 and CVE-2021-42287. By combining the two exploits in the so-called noPac attack, a malicious actor could perform a privilege escalation by impersonating the Domain Administrator after starting out as a standard user. This would lead to a complete domain compromise. The vulnerability critically impacts any systems that have Microsoft Windows Active Directory installed.
CVE-2021-42278 is a Security Account Manager (SAM) spoofing security bypass vulnerability, while CVE-2021-42287 is a privilege escalation vulnerability associated with the Kerberos Privilege Attribute Certificate (PAC) in Active Directory Domain Services. The following paragraphs elaborate on the two vulnerabilities to better understand the noPac attack.
CVE-2021-42278
Microsoft disclosed this vulnerability on November 9th, 2021, and it results from the invalid formatting of a computer name. In Active Directory environments, computer account names should always end with the “$” symbol. Users can see and manually edit these names in the attribute “sAMAccountName” using the ADSI Edit tool as the figure below shows. For privacy reasons we have withheld some information.
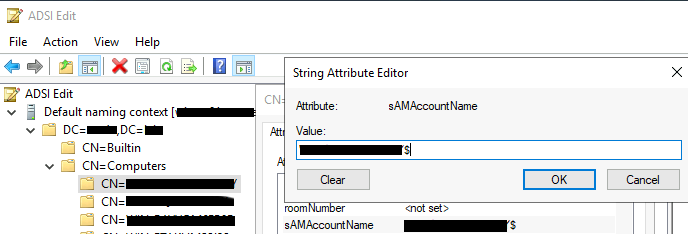
An adversary may rename this value to a Domain Controller account omitting the “$” symbol at the end, which is a key step in the exploitation chain of the noPac vulnerability.
CVE-2021-42287
Microsoft disclosed this vulnerability on the same day as the previous one. However, this one lies in the Kerberos Key Distribution Center (KDC) that is responsible for the processing of Kerberos ticket requests. It consists of a security bypass vulnerability that affects the Kerberos PAC and allows potential attackers to impersonate Domain Controllers. A compromised domain user account could cause the creation of a service access token with higher privileges by querying the Ticket Granting Server (TGS).
The Kerberos PAC is an extension to Kerberos tickets that contains useful information about a user’s privileges. A Domain Controller adds the Kerberos PAC to tickets when a user authenticates within an Active Directory Domain. When users use their Kerberos tickets to authenticate to other systems, the PAC can be read and used to determine their level of privileges without querying the Domain Controller for that information.
How the Attack Works
The exploit of the noPac flaw was first discovered by a GitHub user named Ridter and then confirmed by multiple researchers.
The noPac attack is performed by chain exploiting the two vulnerabilities. The first one allows an attacker to obtain a compromised domain user account, while the second one makes use of privilege escalation associated with the Kerberos PAC within Active Directory Domain Services. Moreover, in order to carry out the attack, a pair of valid credentials is needed.
By default, every authenticated user can add up to ten computers to the Domain. The following steps explain how to perform this attack.
- Create a new account in Active Directory with a random name and then rename it to one of the Domain Controllers without the trailing “$” symbol.
- Request a Kerberos ticket for the created account. Once the ticket is granted, change the name of the account created back to its original name (i.e., the random name chosen in the first step).
- Use the ticket to request an access token from the TGS for a specific service. Because of the absence of an account with that name, the TGS chooses the closest match and appends a “$” symbol. In this way, access to the service is granted with Domain Controller privileges.
Example of a Successful Exploit Attempt
We tried out this attack during a VAPT (Vulnerability Assessment Penetration Test) activity on a customer’s network perimeter. We employed the noPac.py Python tool which is available for free from GitHub.
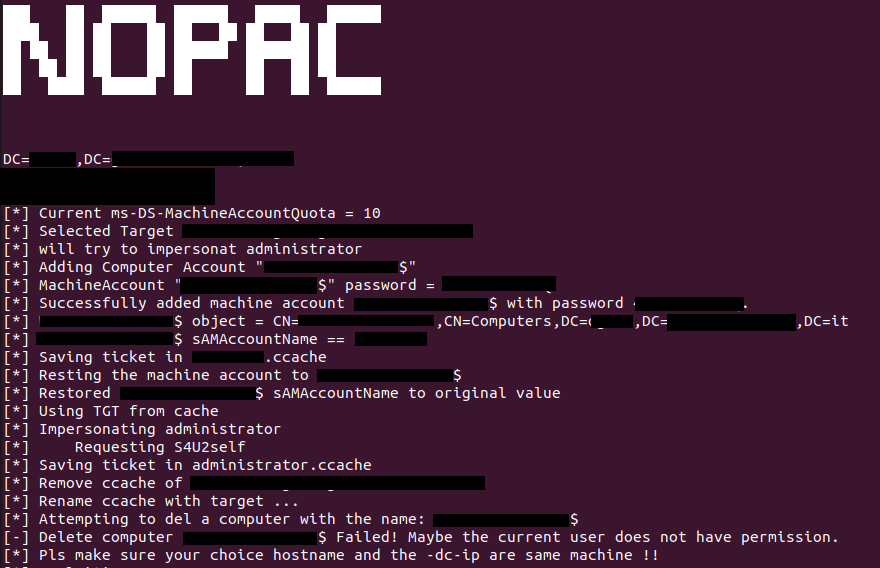
Following the documentation provided, we were able both to impersonate the administrator by getting a Kerberos ticket with administrator privileges (Figure 1), and enter into a semi-interactive shell of the target Active Directory (Figure 2). For privacy reasons we have withheld some information.

Conclusion
The noPac attack is a low-level exploit that can in a few seconds compromise the entire Active Directory environment of a company. In order to mitigate this risk, organizations should apply the latest patches provided by Microsoft to Domain Controllers. Although patching a Domain Controller is not trivial, if even a single one of them remains unpatched, the whole Domain is still vulnerable.
These Solutions are Engineered by Humans
Did you learn from this article? Perhaps you’re already familiar with some of the techniques above? If you find security issues interesting, maybe you could start in a cybersecurity or similar position here at Würth Phoenix.







