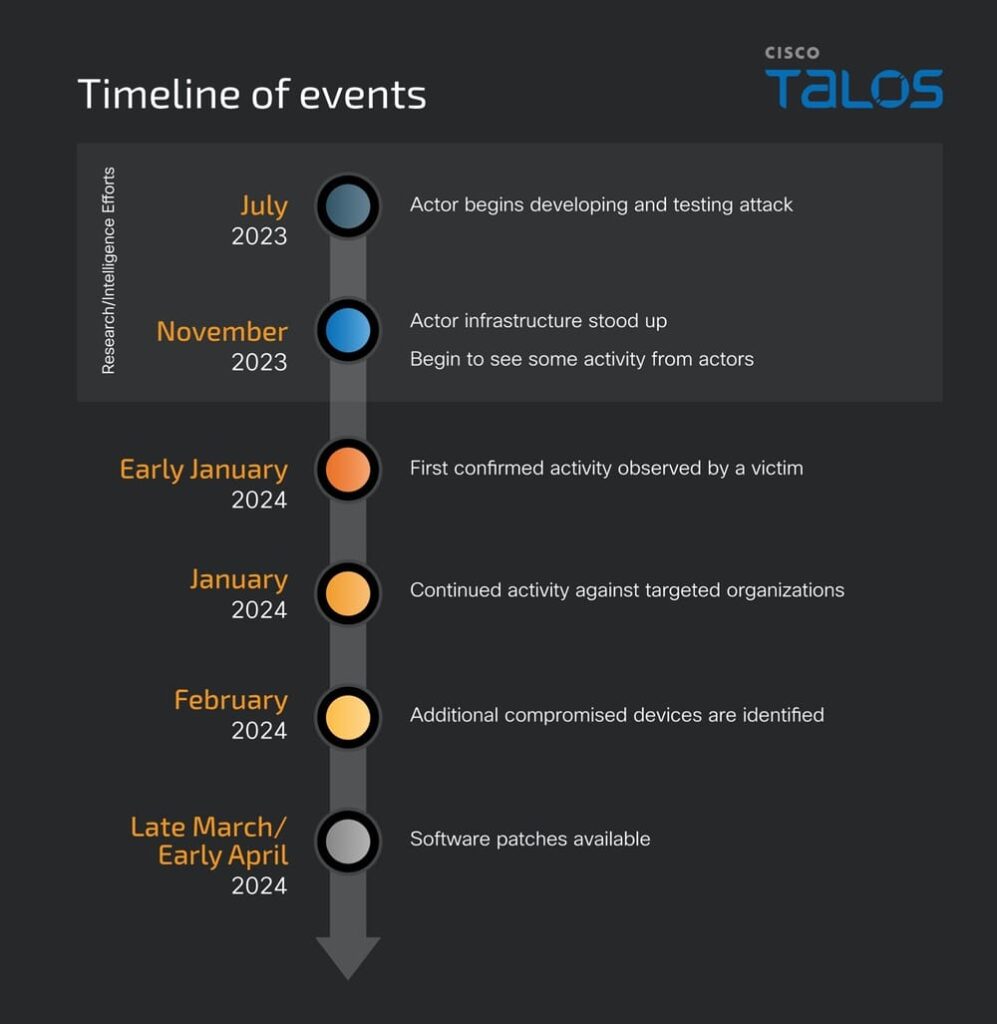
Cisco Talos identified a previously unknown state-sponsored actor behind ArcaneDoor, a sophisticated cyber espionage campaign targeting the perimeter network devices of several vendors. This actor is now tracked as UAT4356 by Talos and STORM-1849 by the Microsoft Threat Intelligence Center.
The initial attack vector is still unknown, but the attacker exploited two previously unknown vulnerabilities. An official fix is now available for both.
| CVE Number | CVSS | EPSS |
| CVE-2024-20353 | 8.6 (High) | 0.23% (Low) |
| CVE-2024-20359 | 6.0 (Medium) | 0.14% (Low) |
The threat actor deployed two backdoors as components of this campaign, dubbed “Line Dancer” and “Line Runner.” They were used to conduct malicious actions on-target, which included configuration modification, reconnaissance, network traffic capture/exfiltration and potentially lateral movement. Line Dancer is a memory-resident shellcode interpreter that enables adversaries to upload and execute arbitrary shellcode payloads. Line Runner was used to maintain persistence on the compromised device and used to retrieve information staged through the use of Line Dancer.
Cisco Talos listed the infrastructure controlled by UAT4356 in its blog post. The following IP addresses were used by the actor. Some of these IPs are part of publicly known anonymization infrastructure that is not directly controlled by the attackers.
IOC List: Actor-Controlled Infrastructure
192.36.57[.]181
185.167.60[.]85
185.227.111[.]17
176.31.18[.]153
172.105.90[.]154
185.244.210[.]120
45.86.163[.]224
172.105.94[.]93
213.156.138[.]77
89.44.198[.]189
45.77.52[.]253
103.114.200[.]230
212.193.2[.]48
51.15.145[.]37
89.44.198[.]196
131.196.252[.]148
213.156.138[.]78
121.227.168[.]69
213.156.138[.]68
194.4.49[.]6
185.244.210[.]65
216.238.75[.]155
IOC List: Multi-Tenant Infrastructure
5.183.95[.]95
45.63.119[.]131
45.76.118[.]87
45.77.54[.]14
45.86.163[.]244
45.128.134[.]189
89.44.198[.]16
96.44.159[.]46
103.20.222[.]218
103.27.132[.]69
103.51.140[.]101
103.119.3[.]230
103.125.218[.]198
104.156.232[.]22
107.148.19[.]88
107.172.16[.]208
107.173.140[.]111
121.37.174[.]139
139.162.135[.]12
149.28.166[.]244
152.70.83[.]47
154.22.235[.]13
154.22.235[.]17
154.39.142[.]47
172.233.245[.]241
185.123.101[.]250
192.210.137[.]35
194.32.78[.]183
205.234.232[.]196
207.148.74[.]250
216.155.157[.]136
216.238.66[.]251
216.238.71[.]49
216.238.72[.]201
216.238.74[.]95
216.238.81[.]149
216.238.85[.]220
216.238.86[.]24







