During WP-CTF 2023 hosted at Würth Phoenix headquarters, a fresh set of CTF challenges were unveiled. These challenges spanned various fields, including OSINT, Digital Forensics, and Blockchain investigations. In this article, I’m going to delve into the solutions for some challenges presented by the Würth-Phoenix security team.
THE FIRST CHALLENGE
The first challenge, titled “There are a TON of clues” exposed a description that pointed to a first asset “wuerth-phoenix.ton”.
"The news is spreading like wildfire in the dark world of cybersecurity experts. A new menacing actor is emerging, leaving its mark on the domain registration landscape. It is the domain name "wuerth-phoenix.ton" that is triggering alarm bells among cybersecurity specialists. As of now, analysts have been unable to open the site, adding to the mystery and concern surrounding this enigmatic domain."
To successfully tackle this challenge, it was essential for each participant to grasp the concept behind TON (The Open Network). By recognizing that ‘.ton’ is a Top-Level Domain associated with WEB3, they were equipped to search for and find a solution to the challenge.
Starting with a simple Google search like “How to open ton sites,” participants found the first clue. The first SERP (Search Engine Result Page) result will point to this useful resource published in the docs of The Open Network project. The documentation exposes 3 solutions, where the most reliable one is TON Util – Proxy.

Ton Utils proxy creates a proxy able to resolve TON address via ADNL – UDP. Following the steps published in the README of this GitHub repository and running the tool on a local machine, participants were able to reach and analyze the first clue related to wuerth-phoenix.ton.
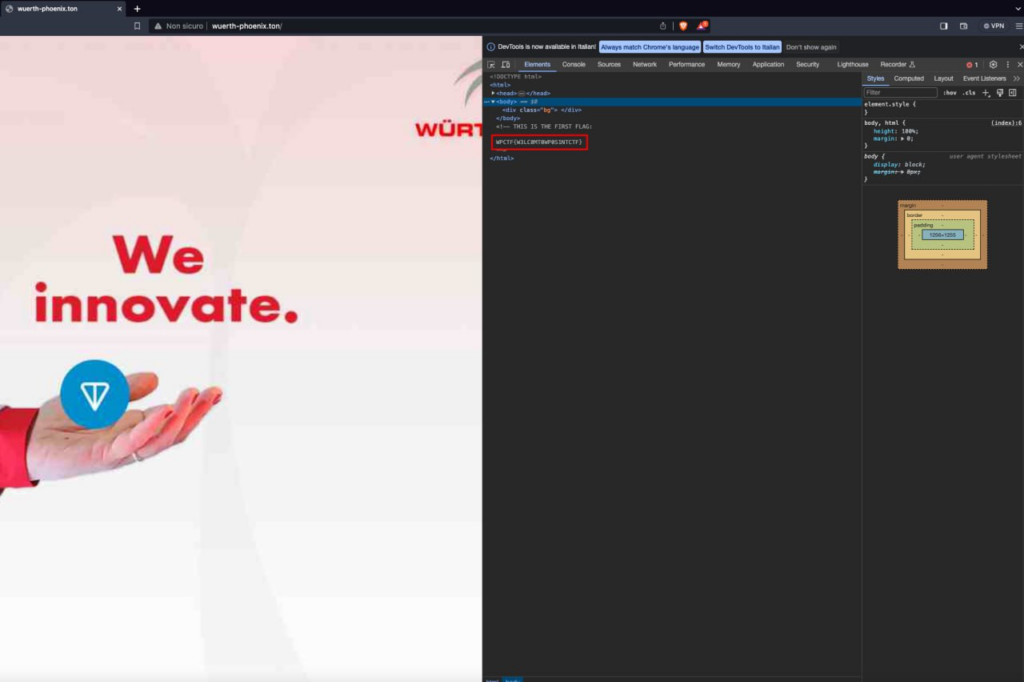
The domain points to a landing page that exposes a background image. In the body of the HTML page, there is a comment containing the first flag: WPCTF{W3LC0MT0WP0S1NTCTF}
SECOND CHALLENGE
The second challenge, titled “Details matter…” pointed participants towards exploring and understanding what a TON domain is. The description of the challenge contained these details.
"Authorities are advising cybersecurity experts to pivot on the domain while emphasizing the importance of scrutinizing every field, attribute, and available meticulously. It's these often-overlooked details that may hide crucial information, unraveling the secrets held by this elusive figure. Remember, the flag should be in the form WPCTF{STRING}."
The key word pivoting of the statement helped participants to realize how to solve the challenge. From “The Open Network” documentation, TON addresses are implemented as NFTs, and like them they can be traded, sold or explored using suitable marketplaces or blockchain explorers.
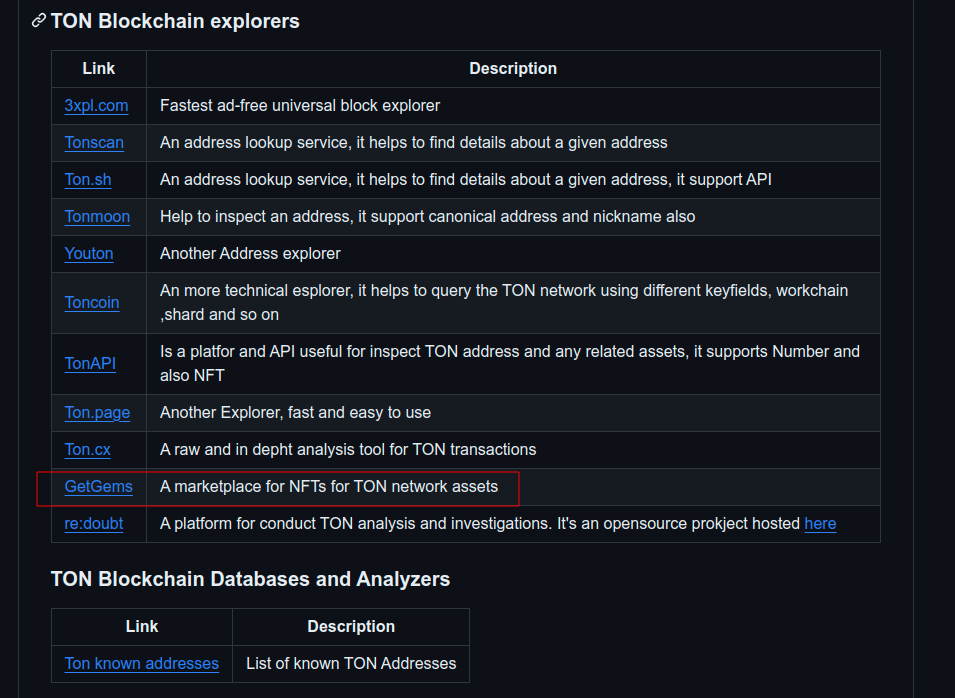
In this GitHub repository, there are different resources for exploring and analyzing the TON ecosystem.
To resolve this challenge, attendees needed to utilize an NFT marketplace such as GetGems. By searching for “wuerth-phoenix.ton[3]” within GetGems, they could retrieve the address of the digital asset. This allowed them to uncover its details and find the owner’s address.
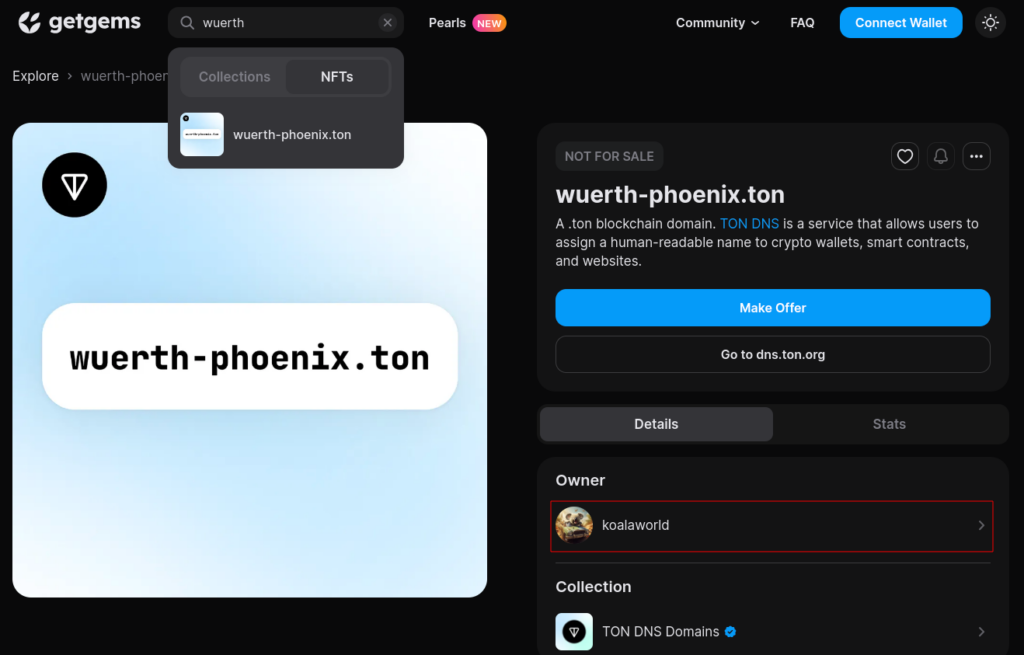
The address of the owner EQBjT1fSX2GRwqmze1IskYyOHwKoPJV6tT6-RCm7on-ZldVO [1] points to a personal page called “koalaworld”. Exploring their related assets, CTF players were able to find 2 other related NFTs:
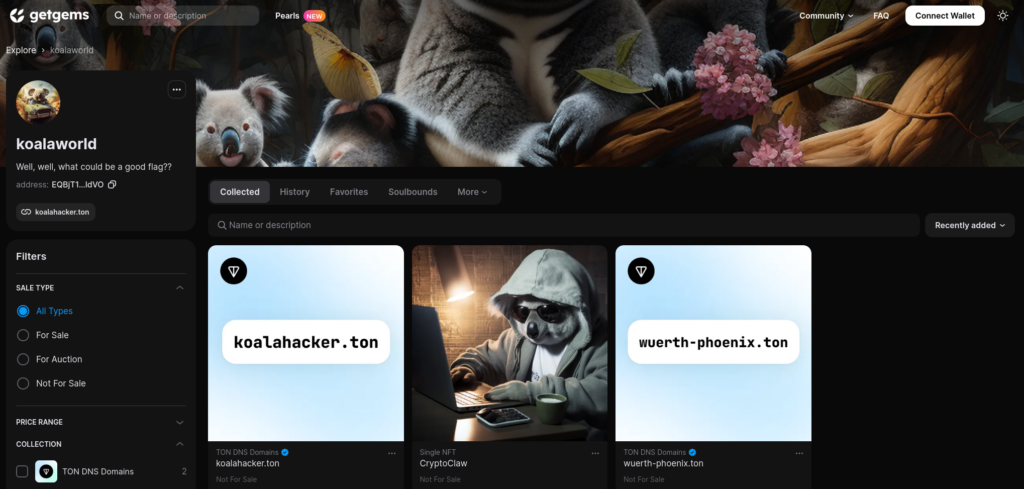
Analyzing the details of the first NFT containing an image (EQDMWPwgGinmgH-PNtNhw1hYoDezudrHIixPJm6x6wxphrjz[2]), it was possible to find pieces of the second flag.
The NFT exposes 6 attributes that when composed and properly formatted create the string WPCTF{Th1sisnt0nly4NFT} which is the second flag.
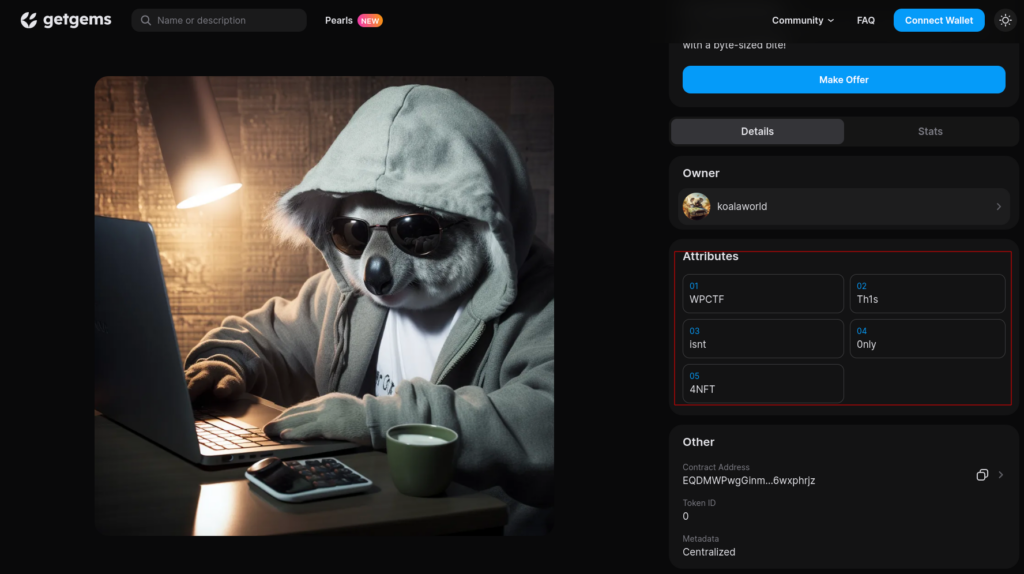
Th1sisnt0nly4NFT (This isn’t only a NFT) can be considered a hidden clue for the third flag.
THIRD CHALLENGE
To address the third flag “What could there be behind a painting?“, it’s essential to understand what NFTs (Non-Fungible Tokens) are and how these digital assets function. NFTs are unique digital tokens that represent ownership or authenticity of digital items. The description of the third task explains:
"Authorities are advising cybersecurity experts to pivot on the domain, intensifying their efforts to decipher the hidden messages concealed by this elusive figure, where images may hold more than what meets the eye. Remember, the flag should be in the form WPCTF{STRING}".
The text clearly points to a some kind of steganography technique. To solve the challenge, participants need to understand what the image source is and what kind of technique was applied.
The first thought could lead to analyzing the image published on the Getgems platform; this image is in .webp format.
The definition of this format syas: "WebP is a modern image format that provides superior lossless and lossy compression for images on the web. Using WebP, webmasters and web developers can create smaller, richer images that make the web faster. WebP lossless images are 26% smaller in size compared to PNGs.“.
This format, with its good compression/quality ratio is used to provide images on the web, but it’s not well suited to steganography.
By investigating the details of NFTs more closely, participants could realize that the image presented by GetGems was a modified version of the original used during the NFT’s minting process. To retrieve the hidden message they needed to examine the NFT’s metadata and retrieve the source image that was utilized in the minting of the blockchain asset.
To retrieve this information, the attendees of the CTF needed to explore the blockchain and find the metadata of the NFT. The repository mentioned earlier includes various blockchain explorers, such as Tonscan. Using Tonscan, analysts can retrieve the raw content of the NFT, in this case, analyzing the address EQDMWPwgGinmgH-PNtNhw1hYoDezudrHIixPJm6x6wxphrjz[2], the participants were able to spot the metadata of the asset and retrieve the address of the original image.
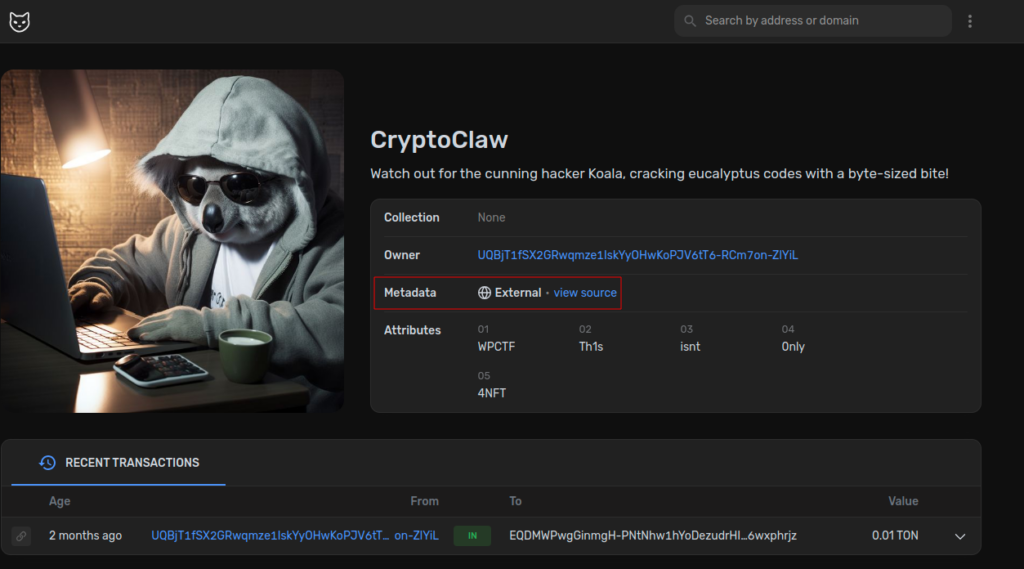
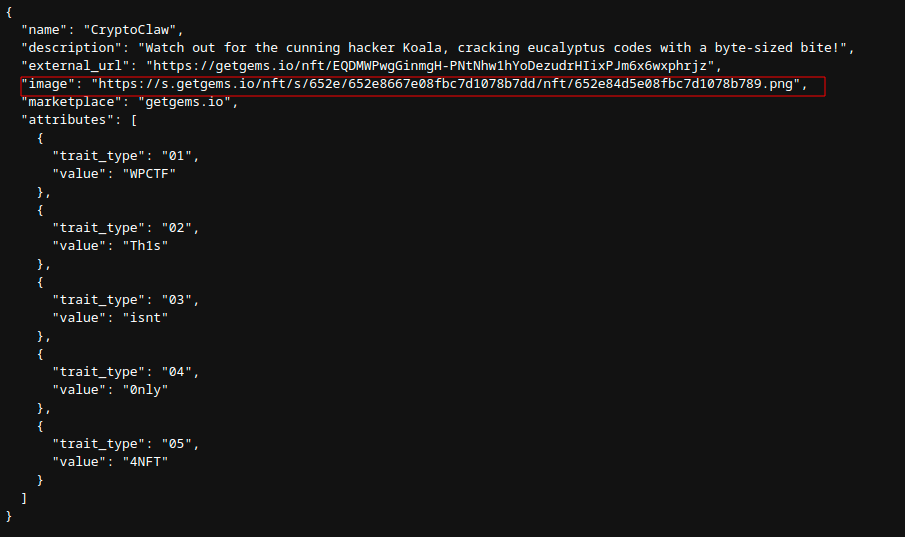
This is the URL related to the PNG image first used for minting the NFT.
After retrieving the image, the next critical step for participants was to identify the specific algorithm used to conceal the message within the artifact. By employing a simple Google search with terms like ‘steganography png,’ they were able to locate a Github repository. This repository offered both offline and online versions of a tool designed to embed text within a PNG file.
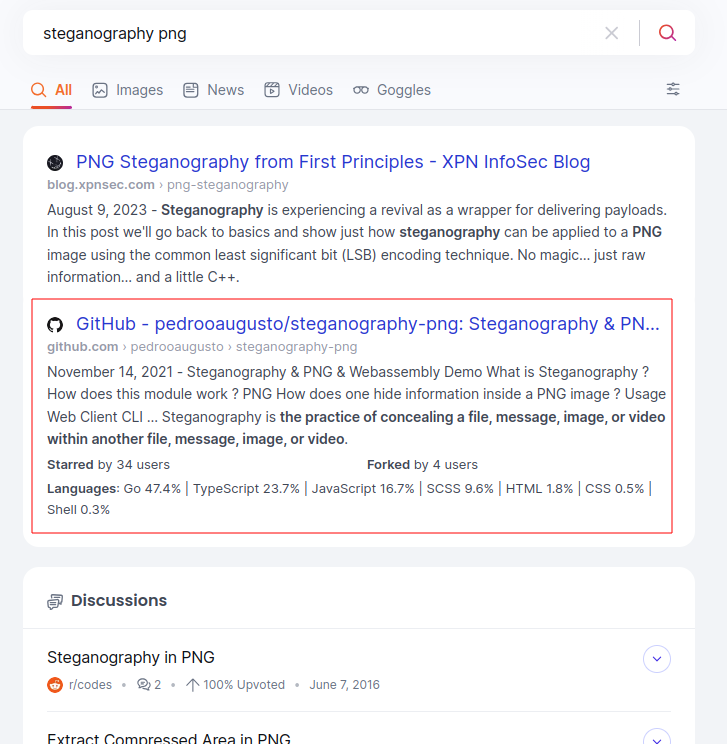
Using the WebAssembly version of the tool and uploading the previously identified PNG, the participants were able to find the third flag.
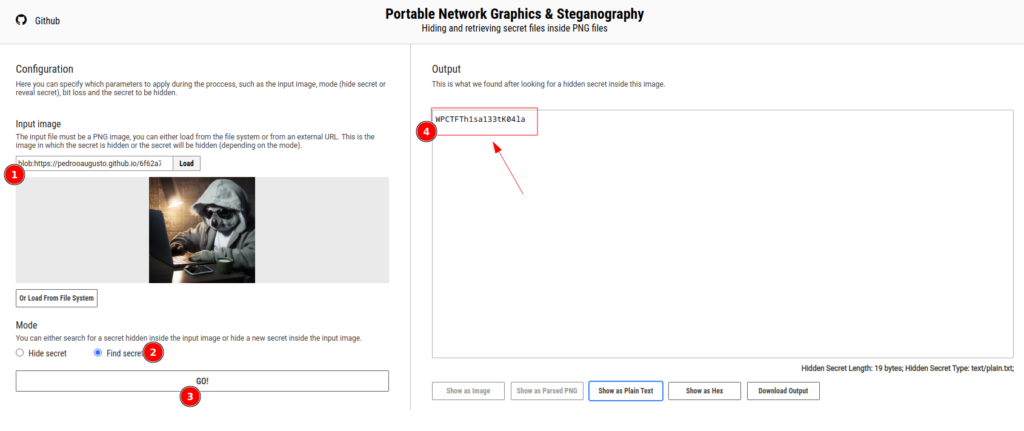
As before, formatting the string as a given pattern, it was possible to recreate the string suitable for the third flag submission WPCTF{Th1sa133tK04la}.
FOURTH CHALLENGE
The fourth challenge titled “Well, it seems good.” had this description: "Authorities are advising cybersecurity experts to pivot on the domain, intensifying their efforts to unravel the secrets held by this elusive figure. Try to find another possible alternative identity used by the threat actor and what kind of pasta he likes."
In this challenge, analysts were pointed to explore the last domain related to the address EQBjT1fSX2GRwqmze1IskYyOHwKoPJV6tT6-RCm7on-ZldVO[1]. Within the list of their domains was the domain “koalahacker.ton”[4].
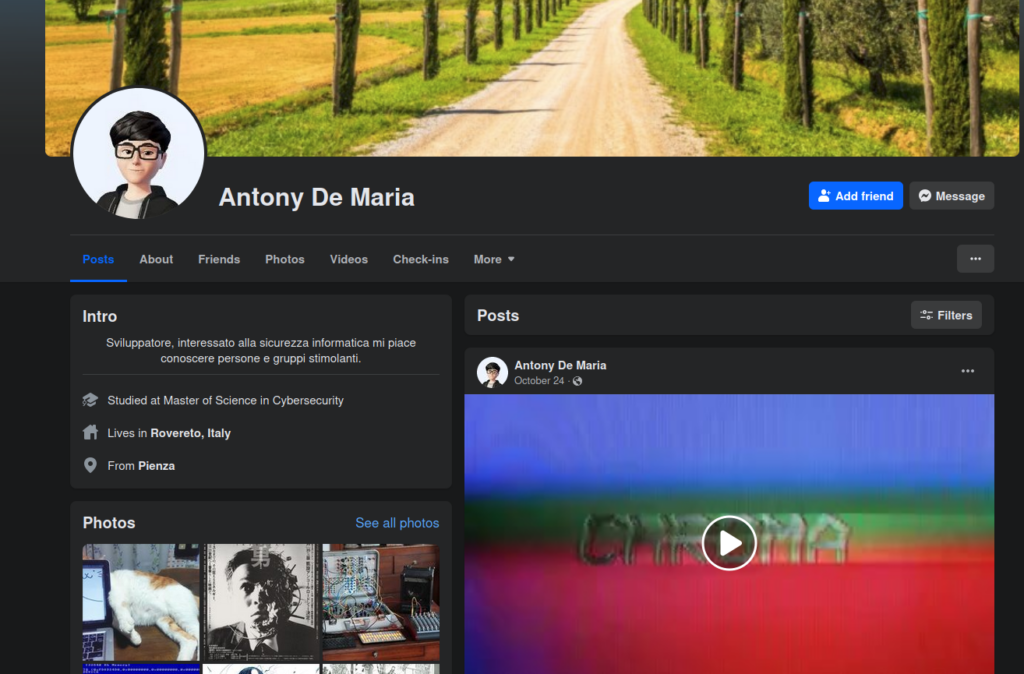
This domain points to a personal blog of a software developer named Antony de Maria, which appears to be used as a portfolio. The page contains various social network addresses. Inspecting the whole site, the players were able to discover that the site uses a cookie for storing some information in base64 encoding format.
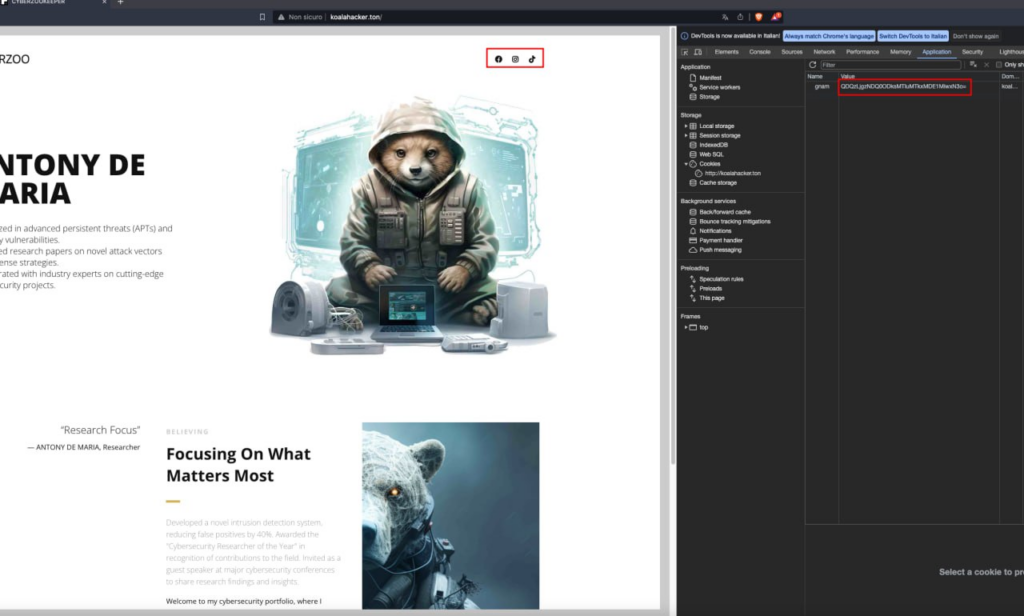
One of the clues presented in the task description was to identify the kind of pasta the target liked. The cookie set by the website was named “gnam”, a key name which (in Italian) brings to mind food or the action of eating.
Analyzing the content of the base64 string value associated with “gnam” let attendees spot some coordinates @43.8344489,12.1910152,17z.
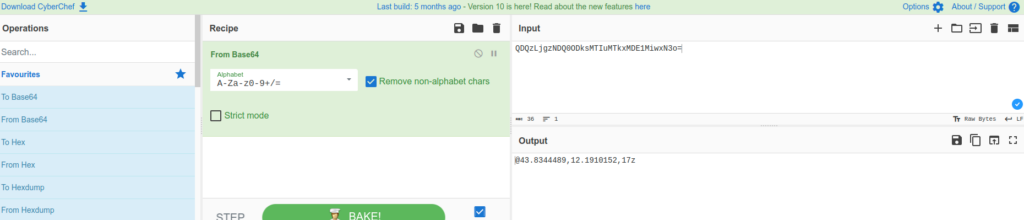
Exploring the coordinates on Google map, they were able to identify a real world location near a Restaurant in the middle of Italy.
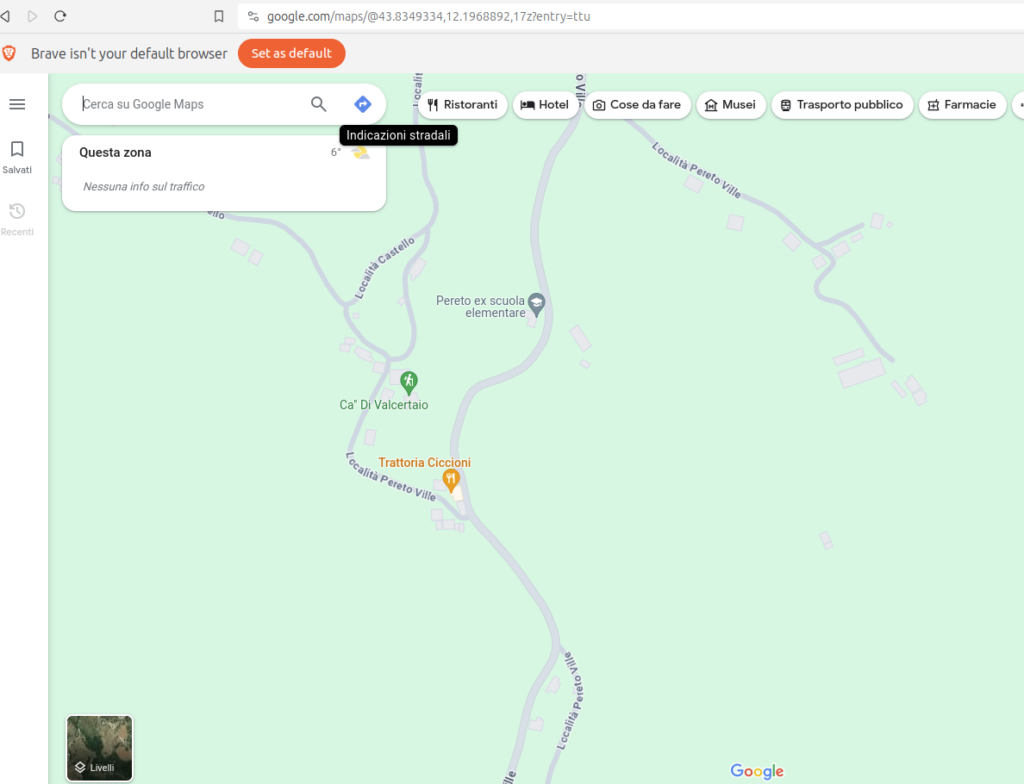
The restaurant Trattoria Ciccioni has several reviews. Exploring them in chronological order let attendees find a picture[5] taken in the restaurant exposing a dish of pasta alongside a smartphone displaying a string which matches the pattern of the CTF flags.
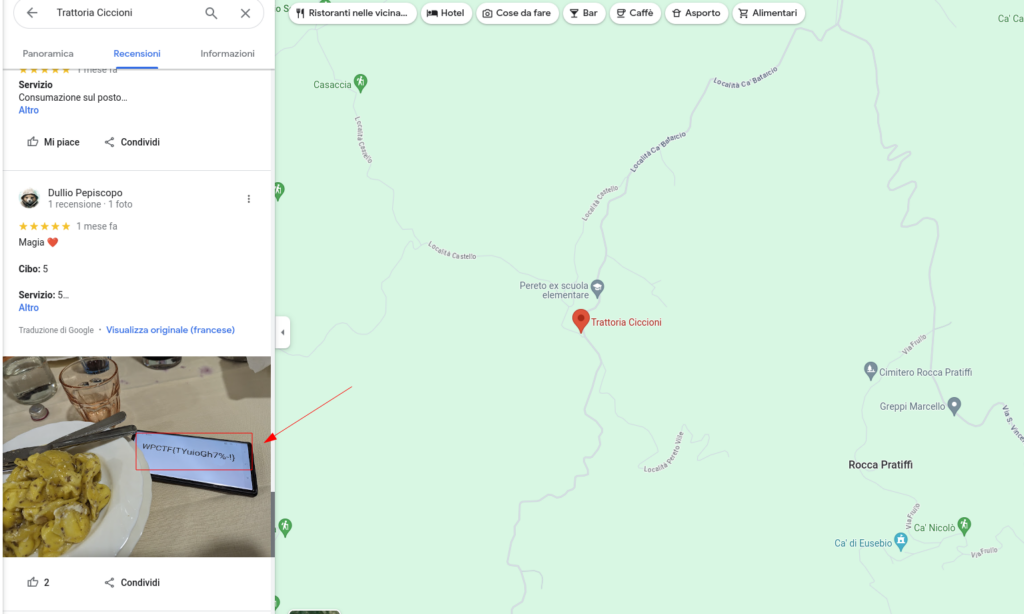
The fourth flag was WPCTF{TYuioGh7%-!}.
FIFTH CHALLENGE
The description of the fifth challenge titled “Where does this noise come from?” stated this text: "With the threat actor's identity in hand, the focus shifted to gathering further insights into their intentions and methods. Authorities were meticulously monitoring the threat actor's social media channels, hoping to uncover valuable clues and additional connections. This delicate phase of the investigation required precision and discretion, as the threat actor might be aware of the increased scrutiny.".
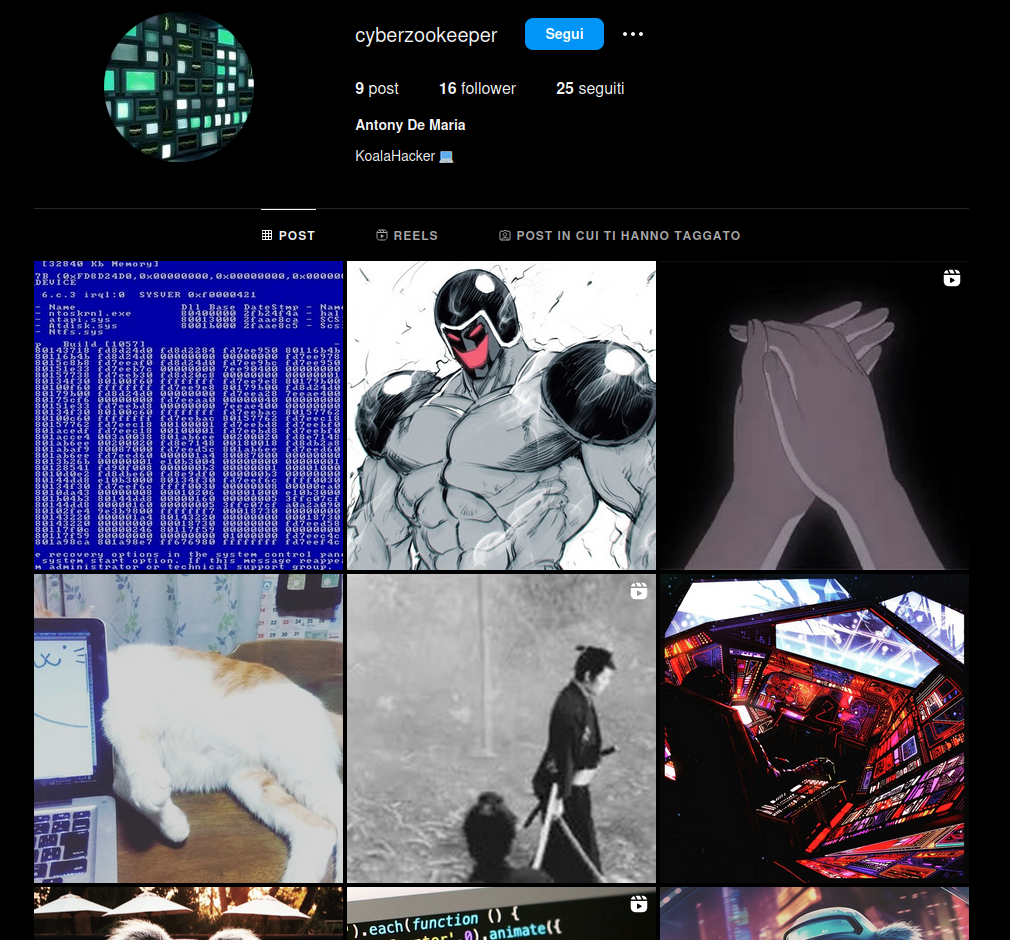
The provided text contains clues about the directions which have to be followed in order to complete the task: the next challenge can be solved by analyzing social media profiles of the identified persona. In their personal blog (koalahacker.ton) there were different links pointing to the Instagram, TikTok and Facebook social platforms. All of them referred to Antony De Maria, Koalahacker and Cyberzookeeper, the names and keywords used in his personal blog.
The Facebook profile at https://www.facebook.com/profile.php?id=61552426503428
The Instagram profile at https://www.instagram.com/cyberzookeeper/
The TikTok profile at https://www.tiktok.com/@antonydemaria
In analyzing the title of the challenge, “Where does this noise come from?”, attendees were guided to understand that the solution should be related to a sound. This implies that the challenge involves identifying or interpreting a specific noise or audio element, requiring attendees to apply their knowledge or skills in audio analysis.
Each social network profile displayed various images and videos. However, only one video included sound. By analyzing this specific video, participants were able to learn how to extract pertinent information from the media provided.
There was a very useful tool called Instalooter that could download images and videos from an Instagram profile, but unfortunately, it’s no longer operational. The most quick and effective method to download the video was directly from TikTok or using the lite version of Facebook https://mbasic.facebook.com/. On this version of the Facebook platform, the video can be directly downloaded using “save link as” from the browser.
After downloading the video, participants needed to extract the audio in MP3 format. Utilizing tools such as ffmpeg, they were able to isolate the audio track for further analysis.
ffmpeg -i VIDEOFILE -acodec libmp3lame -metadata TITLE="OUTPUT" OUTPUT.mp3
The audio track contains a DTMF tone track. From its definition: Dual tone multi-frequency (DTMF) is the sounds or tones generated by a telephone when the numbers are pressed. These tones are transmitted with the voice channel. DTMF is used to control automated equipment and signal user intent, such as the number they wish to dial. Each key has two tones at specific frequencies.
This detail let participants understand how to decode the message behind the sound. Using online tools like DTMF DECODER attendees were capable of retrieving the corresponding numbers.
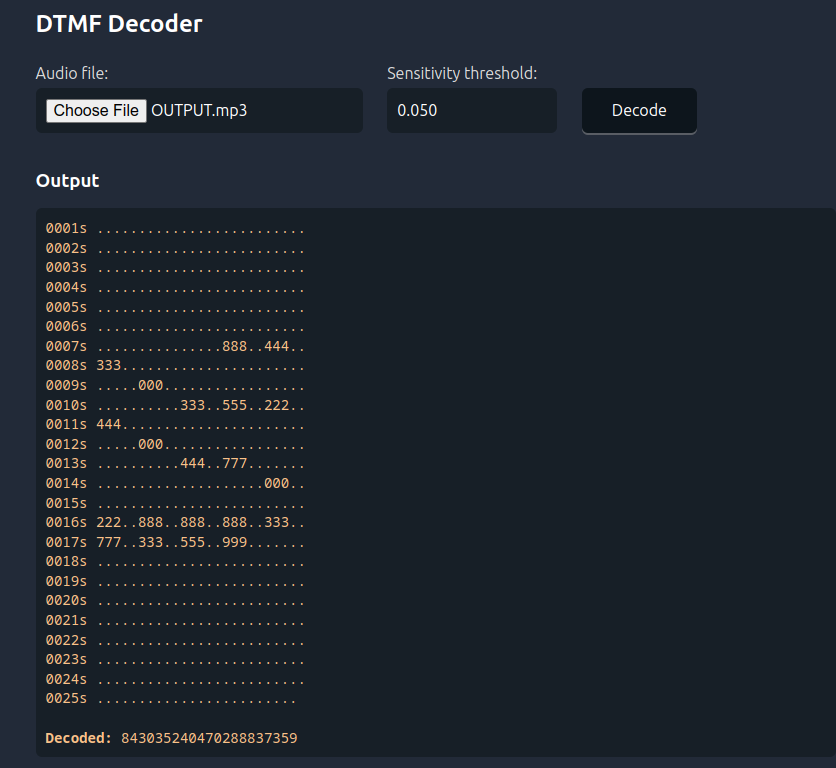
The processing of the sound generates the numbered sequence of 843035240470288837359. Listening to the audio track and matching the timing of the keystroke helped participants realize that the sound was generated during the composition of a message via old T9 dictionaries.
To decipher the flag, attendees were required to use a tool similar to T9 Decipher, which is designed for decoding strings from a T9 text messaging system.
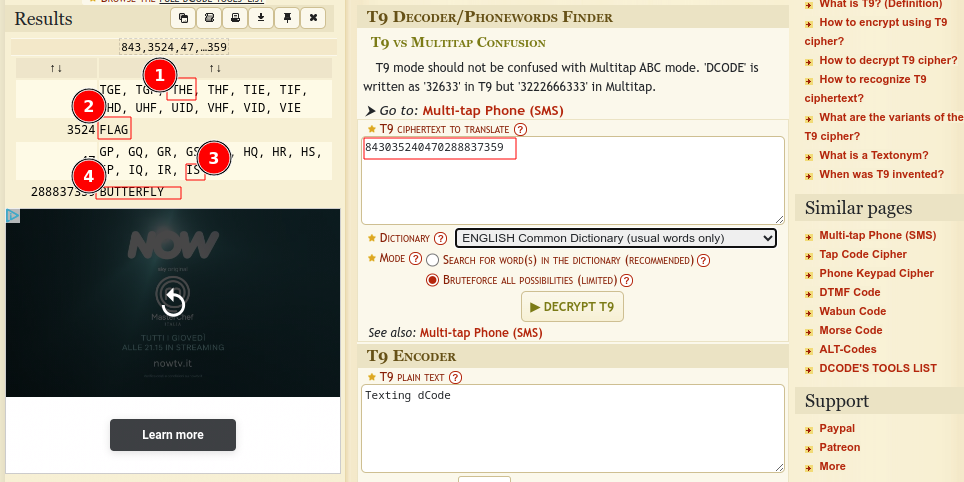
By selecting the common English dictionary in the decoding tool, participants were able to extract the phrase “THE FLAG IS BUTTERFLY.” Following the format specified in the challenge description, they then formatted this phrase into the final submission: WPCTF{BUTTERFLY}.
This concludes our exploration of the OSINT/DFIR challenges at WP-CTF 2023. The event offered a diverse array of challenges and tasks. If you’re intrigued by how CTFs operate or want to participate in future events, feel free to contact us or join our upcoming contests.
Meanwhile, to give you a glimpse of the event, feel free to watch this brief video showcasing some highlights.
REFERENCES
[1] https://tonscan.org/address/EQBjT1fSX2GRwqmze1IskYyOHwKoPJV6tT6-RCm7on-ZldVO
[2] https://tonscan.org/address/EQDMWPwgGinmgH-PNtNhw1hYoDezudrHIixPJm6x6wxphrjz
[3] https://tonscan.org/address/EQC3BkhOiHXNoXHUg9YjsYFCzit3KS-RInL4rjoiEA_WmU4K
[4] https://tonscan.org/address/EQDoQCtDyGD5xbk_446phub47NwnZZ2Sf8LNkg6LpHt_DLjW
[5] https://maps.app.goo.gl/zUKhFb4h8hDECPib7






