
Much has already been said about Initial Access Brokers (IABs) so I will limit myself to a brief description and then delve into the main theme of this article.
The theme of Initial Access Brokers was summarized fantastically in the Initial Access Broker Landscape project by Curated Intelligence, reported in this link, which I recommend reading.
What are Initial Access Brokers?
At a high level, IABs are Threat Actors (TAs) who seek to procure access to companies’ networks and sell them to other TAs, which take advantage of these initial accesses to carry out attacks that are more impactful to companies and that can lead to economic benefits (e.g., ransom payment) for TAs.
The initial access that is offered for sale can be of different types. For instance, there’s access to cPanel and other types of control panels. A buyer of this type of access can potentially search web hosting content to find sensitive information or to perform website defacement. Web shell access is another common offering of IABs, as it helps to facilitate quiet access to a compromised server.
Even so, IABs most commonly turn to RDP and VPN technology. Often these are the most convenient means of access to your network. Consider, for example, VPN accesses. Over the years, several serious vulnerabilities have been disclosed on devices from different vendors. IABs could exploit those flaws to gain and later sell network access. As for RDP, TAs could use scanning tools like Shodan, Censys and ZoomEye to look for networks with RDP ports open to the internet. TAs could then brute force the username and password, leveraging stolen login information for a credential stuffing attack.
Another type of access that can be offered for sale is a TeamViewer or AnyDesk session, which has the advantage that it will likely allow the TAs to remain below the threshold of controls performed by endpoint security software or IDS/IPS.
Another type of access that is increasingly exploited is related to infostealer logs, which are purchasable both within specific markets (Russian Market, 2Easy, Waus Query) and in the Telegram channels of individual traffickers.
What is changing in this landscape?
In recent weeks on the well-known ExploitIN, XSS and RAMP forums, in which the IABs are very active and within specific areas of the forums where auctions are taking place for the sale of these initial accesses, we are increasingly seeing large stocks of accesses being offered for sale, rather than individual accesses. The trend of bulk sales is therefore becoming increasingly widespread. Let’s look at some recent examples:
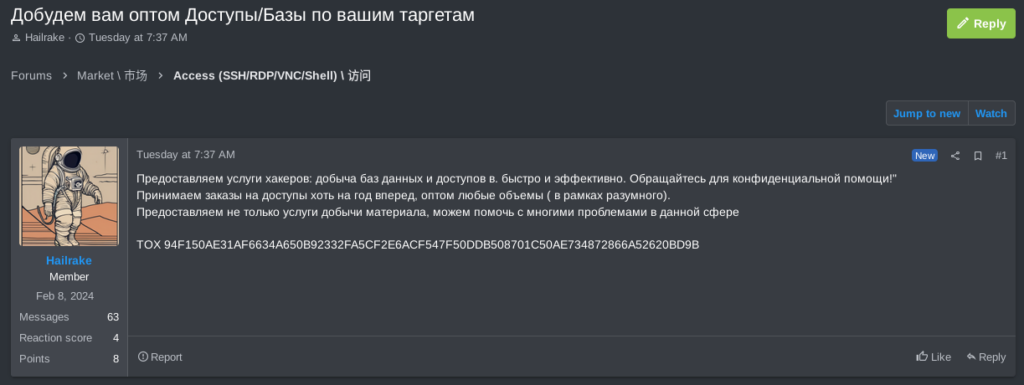
In this post, published on RAMP, TA Hailrake provides, for sale, database extraction and access services of different types, even in large volumes.
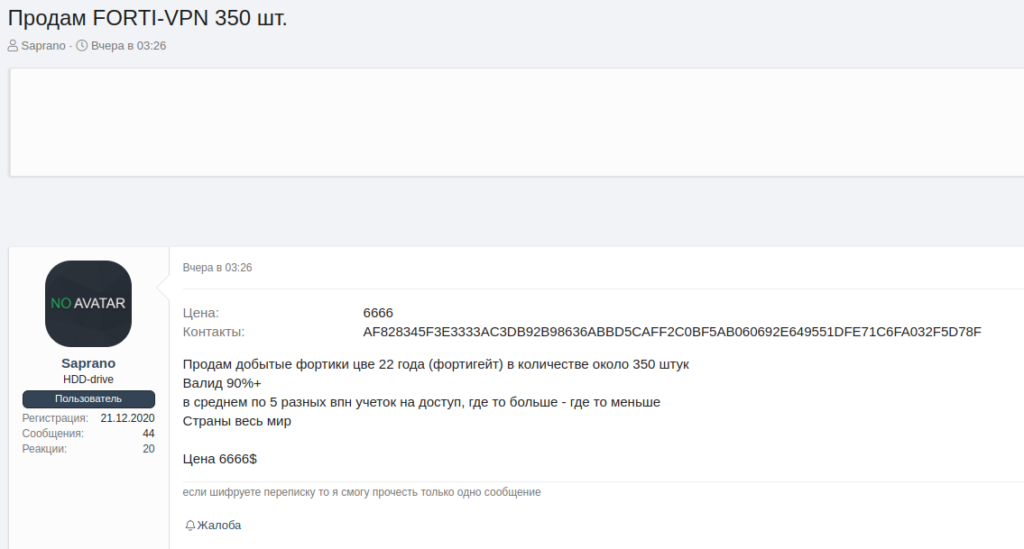
In this post, published on XSS, TA Saprano provides, for sale, a stock of VPN accesses relating to Fortigate devices.

In this post, published on ExploitIN, TA Howell provides, for sale, a stock of accesses relating to 209 different companies, apparently recovered by exploiting the recent vulnerability (https://nvd.nist.gov/vuln/detail/CVE-2024 -27198) disclosed on JetBrains TeamCity.
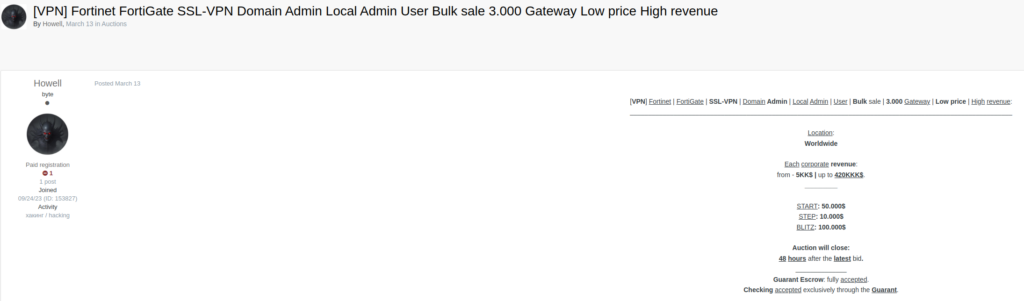
In this post, published on ExploitIN, again by TA Howell, a stock of accesses relating to different companies are provided for sale, apparently recovered by exploiting recent vulnerabilities (a list is available here https://www.fortiguard.com/ psirt) disclosed on the firewalls of the vendor Fortinet.
There would be many other examples to report, relating for example to access to Citrix and SonicWall products.
So what’s happening?
Why, instead of choosing the path that would probably allow them to maximize their profits by selling individual accesses individually, have several TAs in recent weeks been selling entire stocks of accesses? The causes and motivations behind this choice can be different:
1) Initial Access Brokers are developing engineering processes that are increasingly efficient at exploiting critical vulnerabilities.
2) Threat Actors who purchase these accesses make long-term investments. One kind of TA of this type could be, for example, RaaS (Ransomware As A Service) affiliates, who could use these accesses in the weeks or even months following the purchase.
3) Patch Management is not yet well enough developed by companies that they can make all necessary patches in a short amount of time, and therefore TAs know that the accesses they purchase today will most likely be valid even for many weeks, and therefore they can accept the risk of investing the initial sum in the purchase.
4) The fourth possibility is the exact opposite and could be a positive element. What if TAs have realized that vendors are increasingly faster and more efficient at making patches available, and that end companies are increasingly faster and more efficient in applying these patches? Surely if this were the case and I were a TA, my objective would be to maximize my profit by selling all my Access stock as soon as possible, to avoid the risk that it would no longer be valid.







