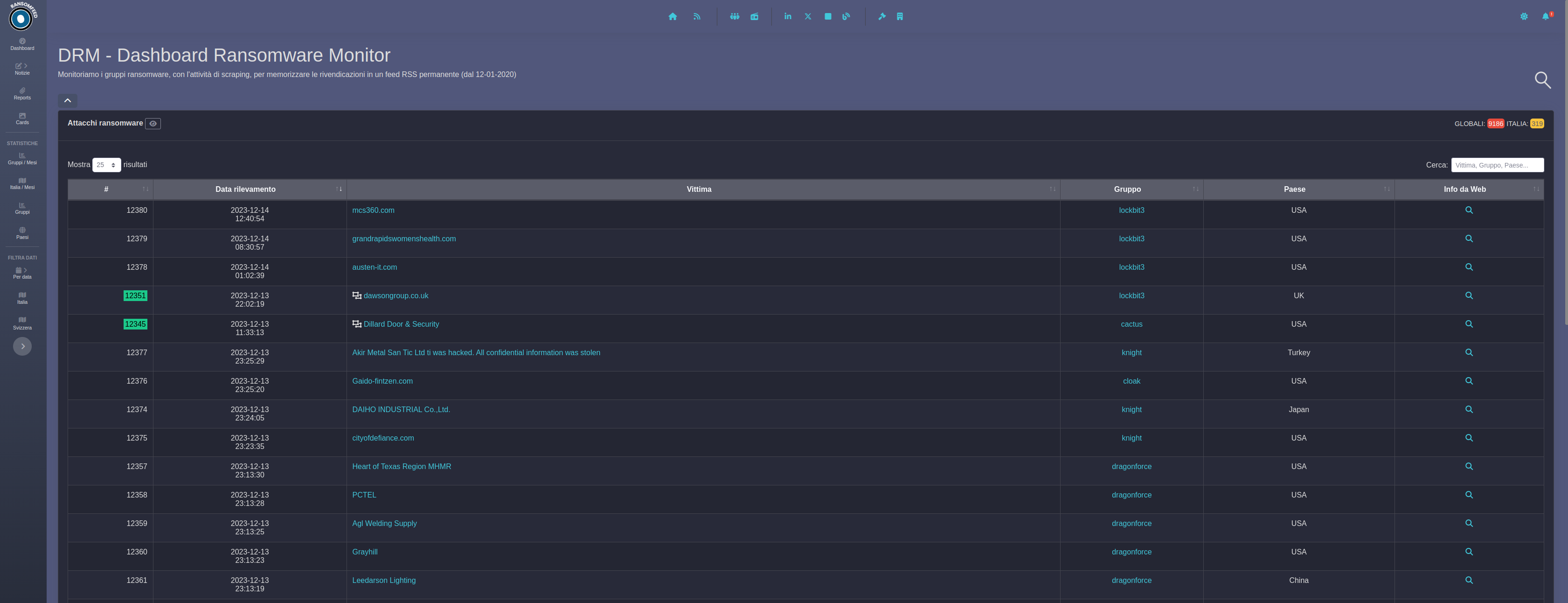
SOC News | Mar 21 – IABs and Bulk Sales
Much has already been said about Initial Access Brokers (IABs) so I will limit myself to a brief description and then delve into the main theme of this article. The theme of Initial Access Brokers was summarized fantastically in the Initial Access Broker Landscape project by Curated Intelligence, reported in this link, which I recommend…
Read More