How to Fix Transformation Problems After Upgrading to Elasticsearch 9.0
With the upgrade to NetEye 4.44, we’ve added a lot of new features (https://www.neteye-blog.com/2025/10/neteye-4-44-release-notes/) and, from my point of view, one of the most relevant is the introduction of Elastic Stack 9.
This Elasticsearch major release (https://www.elastic.co/guide/en/elastic-stack/9.0/elastic-stack-release-notes.html) includes some new functionalities such as: ESQL Lookup Joins , LogsDB Index Mode Optimizations, etc.
During various migrations we faced some issues linked to transformations linked to integrations. Indeed, after the systems began running on Elasticsearch 9, some errors like the following arose within NetEye:
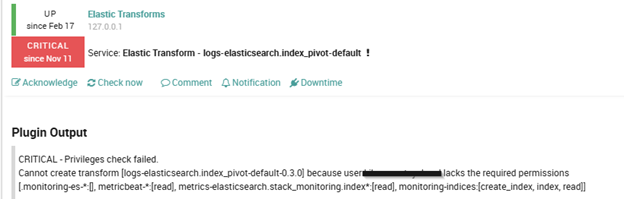
These problems looked like they were linked to missing permissions for a specific user, but after some investigation we found out that the user in question was directly managed by Elastic. So, updating/fixing these permissions should be managed by the ELK stack.
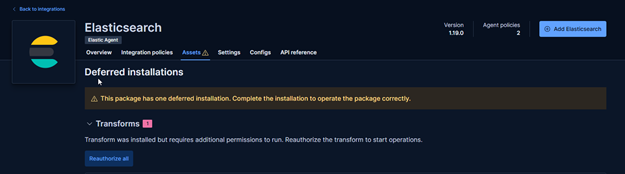
So, following the broken Transformation, i.e. logs-elasticsearch.index_pivot-default, we found that the Health status was not OK, and then also that the installed integration was in “Warning”.

The integration had a Warning message like the one in this picture, and under Transform you can find a “Reauthorize all” button that managed all required permissions for the internal user.
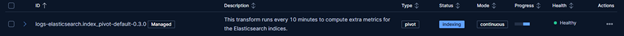
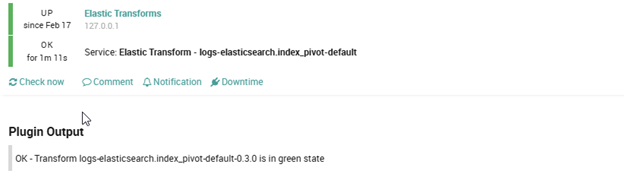
Clicking on it will fix the broken transformation, and data will be correctly transformed by Elasticsearch. The status will be Healthy again and also the NetEye Check will be in an “OK” Status again:
So, if you’re upgrading your NetEye to the latest version with ELK Stack 9, remember to have a look at your Transformation, and if you see problems like these, follow this short tutorial in order to fix them.
These Solutions are Engineered by Humans
Did you find this article interesting? Does it match your skill set? Our customers often present us with problems that need customized solutions. In fact, we’re currently hiring for roles just like this and others here at Würth IT Italy.






