Ransomware Double Extortion Attack: 2025 Overview
As 2025 comes to a close, we can make some observations regarding the evolution of the double-extortion ransomware attack landscape.
The data shown is the result of the enrichment performed within SATAYO starting from the data made available by the Ransomfeed project.
The URLs of the Data Leak Sites (DLS) of the various ransomware gangs can be consulted within the deepdarkCTI project.
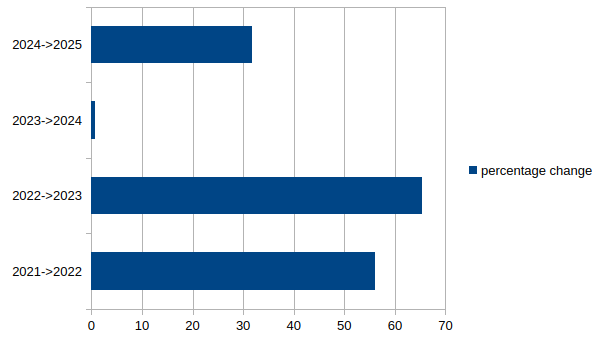
The reported attacks on the DLS of various ransomware gangs in 2025 totaled 7,679, compared to 5,831 in 2024. The increase in reported attacks was therefore 31.69%.

If we look at the percentage increase from 2025 to 2024, we see that the past year was marked by a sharp resurgence in double-extortion attacks. Indeed, if we consider the percentage changes from previous years, we see that while the increase in both 2022 and 2023 was significant, in 2024 we saw a stabilization of the previous year’s numbers.
The distribution of attacks across the months of the year remained fairly uniform, with the exception of February 2025, when there was a surge (311) in attacks reported by the Clop ransomware gang.
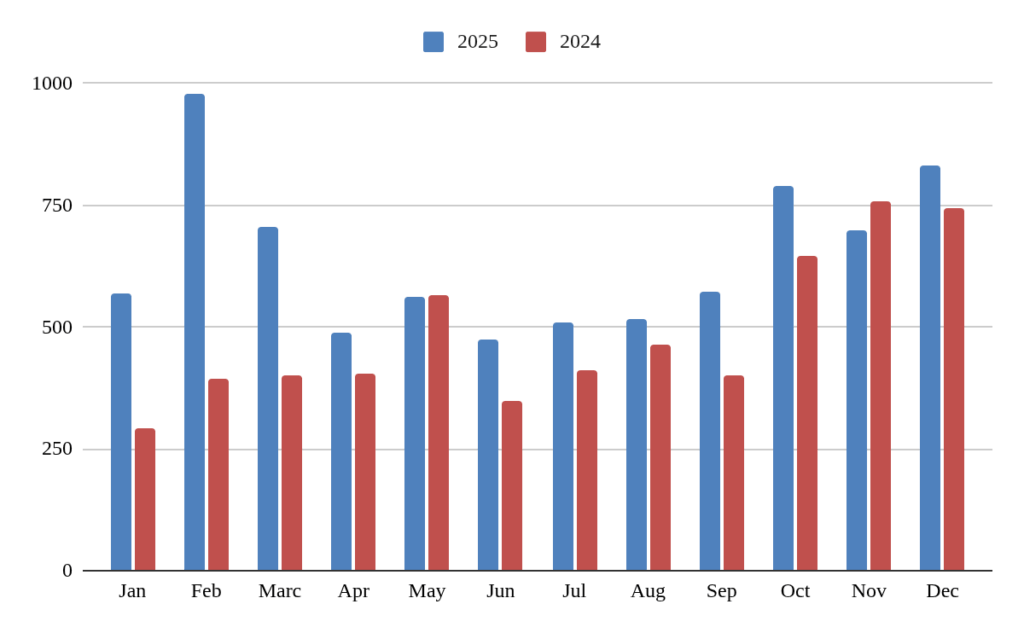
During February 2025, the Clop ransomware group was observed primarily exploiting two vulnerabilities in Cleo file transfer software: CVE-2024-50623 and CVE-2024-55956. The attacks in February 2025 were a continuation of a campaign that commenced in December 2024, targeting critical flaws in Cleo’s LexiCom, VLTransfer, and Harmony software. This tactic of exploiting unpatched vulnerabilities in file transfer software is consistent with Clop’s historical operations, including previous attacks on MOVEit and GoAnywhere.
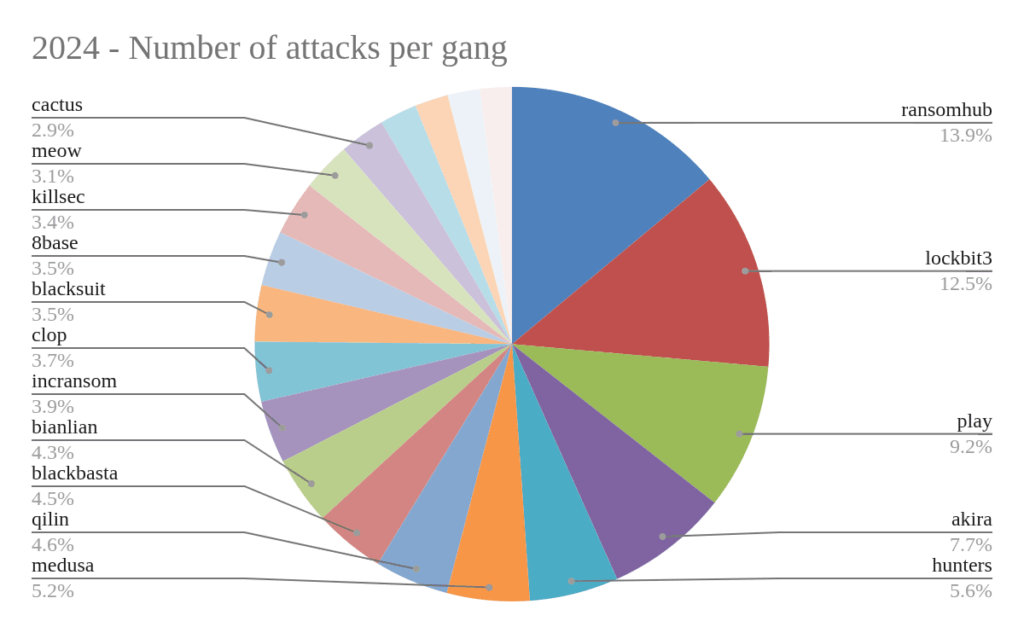
Moving on to analyze the number of attacks declared by individual ransomware gangs (to clarify the situation in the following graphs we have only considered the top 20 gangs by number of declared attacks), we can see that we continue to witness a very fluid situation, where on the one hand, some gangs (Akira, Qilin, Clop) continue to remain leaders, on the other, we can note that there are dozens of other gangs that carry on their activity for only a few months, declaring a small number of attacks.
Here we can see the data for 2024:
And here we can see the data for 2025:

For the first time since we began collecting data on double-extortion ransomware attacks (2020, not including 2019, when we only recorded 33 attacks), the Lockbit gang has dropped out of the top three. This is obviously due to the aftermath of Operation Cronos, which took down much of this gang’s infrastructure in 2024. It’s worth noting, however, that the Lockbit gang has resumed activity in recent months, reporting a total of 92 attacks in 2025.
Active gangs (which have declared at least one attack on their DLS) amounted to 125 in 2025, compared with 103 in 2024.
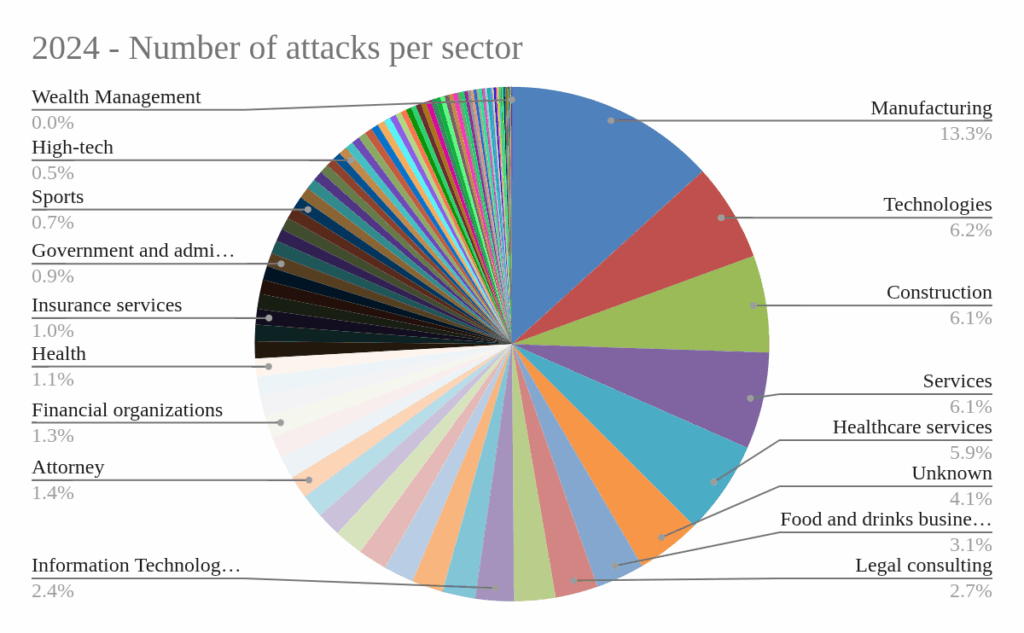
At the sector level, manufacturing, construction and technology remained the hardest hit. Overall volume increased in 2025, but the distribution shifted: some traditionally targeted sectors grew in raw numbers but lost relative share, while several secondary sectors expanded significantly. Manufacturing remains the primary target, but its dominance weakened in percentage terms. Construction, Logistics, Retail, and Services show the most meaningful growth signals.
Here we can see the data for 2024:
And here we can see the data for 2025:

The most notable change was in the Logistics sector, which went from 82 attacks in 2024 to 192 attacks in 2025. This increase brought the sector up to ninth place among the most attacked sectors.
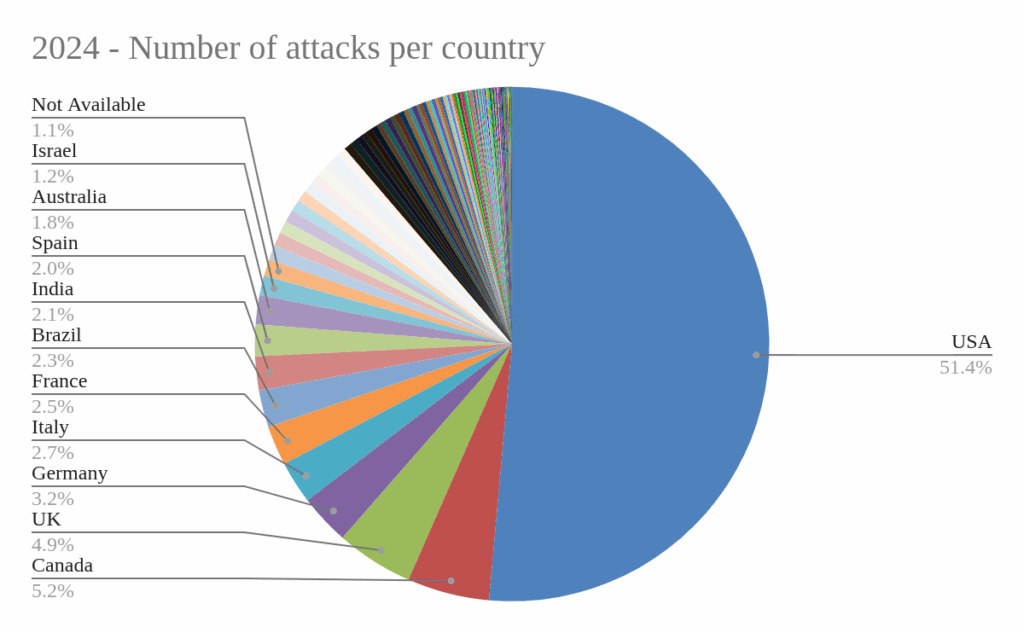
Finally, moving on to the countries most targeted by ransomware gang attacks, the United States continues to top this unflattering ranking in 2025, with more than 50% of reported attacks being suffered by organizations based in that country. The United States is followed by another North American country, Canada, then by several European countries (Germany, the United Kingdom, France, Italy, and Spain). In total, 139 countries experienced at least one reported attack in 2025, compared to 151 in 2024.
Here we can see the data for 2024:
And here we can see the data for 2025:
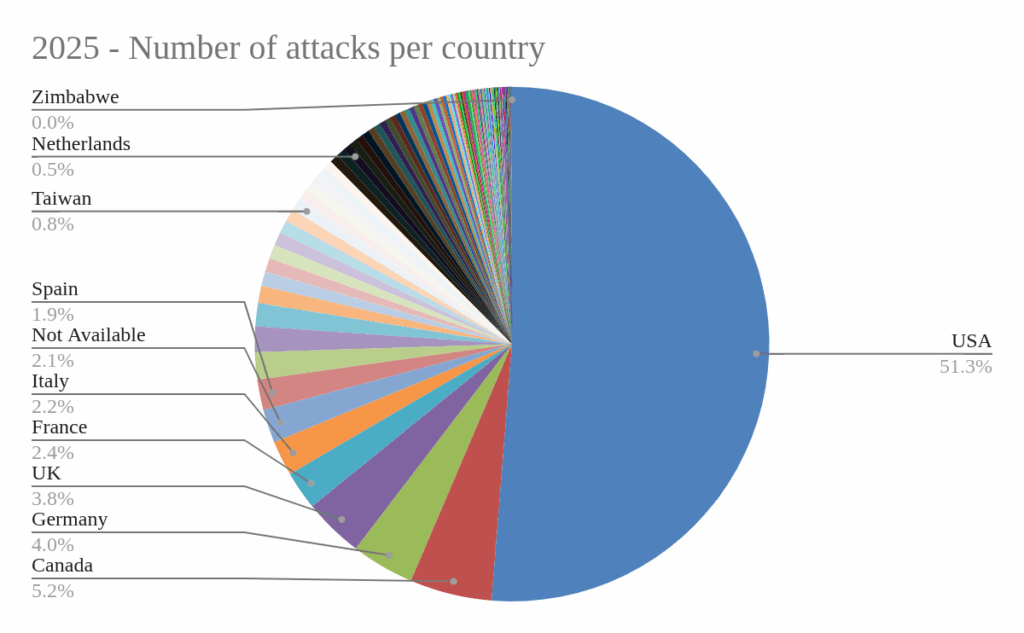
Focusing briefly on the Israeli-Palestinian conflict scenario, we can note that attacks against Israeli organizations have halved in 2025 (37) compared to 2024 (72).
Recommendations
It’s now been six years (since the end of 2019) that we’ve been living with the threat of double-extortion ransomware attacks. More than 25,000 reported attacks have occurred since then.
The attack vectors used by ransomware gangs to carry out these attacks have improved significantly over the years. So even though organizations’ awareness and defensive posture have improved, the threat of double-extortion ransomware attacks continues to loom. Below, we provide some areas for improvement that organizations should consider incorporating into a continuous improvement process.
1. Robust Patch Management and Vulnerability Management
- Promptly Patch and Update: Regularly apply security patches and updates to all operating systems, applications, and firmware. Prioritize patching for internet-facing systems and those identified with critical vulnerabilities, especially RCE flaws.
- Vulnerability Scanning and Penetration Testing: Conduct regular vulnerability assessments and penetration tests to identify and remediate weaknesses in your infrastructure before attackers can exploit them.
- Asset Management: Maintain an accurate inventory of all hardware and software assets to ensure comprehensive coverage in your patching and security efforts.
2. Strengthen Access Controls and Authentication
- Multi-Factor Authentication (MFA): Implement MFA for all remote access services (VPNs, RDP), email, and critical internal systems. This significantly reduces the risk of successful credential stuffing and phishing attacks.
- Principle of Least Privilege: Grant users and systems only the minimum necessary permissions to perform their tasks. Restrict administrative privileges and regularly review access rights.
- Strong Password Policies: Enforce the use of strong, unique passwords and consider password managers for users.
- Disable or Secure RDP: If RDP is necessary, ensure it is secured with strong passwords, MFA, and network-level authentication. Limit direct internet exposure of RDP ports.
3. Network Segmentation and Isolation
- Segment Networks: Divide your network into smaller, isolated segments. This limits an attacker’s ability to move laterally and encrypt critical systems if one segment is compromised.
- Isolate Critical Data and Systems: Place sensitive data and critical business systems on highly restricted network segments, with stringent access controls and monitoring.
4. Data Backup and Recovery
- Regular, Immutable Backups: Implement a robust backup strategy that includes regular backups of all critical data. Store backups offline or in immutable storage to prevent them from being encrypted or deleted by ransomware.
- Test Recovery Plans: Regularly test your data recovery procedures to ensure that you can quickly restore operations after a ransomware attack. This includes testing the integrity of backups and the speed of restoration.
- “3-2-1 Rule”: Follow the 3-2-1 backup rule: at least three copies of your data, stored on two different media, with one copy offsite.
5. Employee Training and Awareness
- Security Awareness Training: Conduct regular security awareness training for all employees, focusing on recognizing and reporting phishing attempts, social engineering tactics, and suspicious emails or links.
- Simulated Phishing Attacks: Perform simulated phishing exercises to test employee vigilance and reinforce training.
6. Endpoint Detection and Response (EDR) and Antivirus
- Advanced Endpoint Protection: Deploy next-generation antivirus (NGAV) and EDR solutions on all endpoints. These tools can detect and respond to malicious activity, including ransomware, in real-time.
- Behavioral Monitoring: Configure EDR solutions to monitor for suspicious behaviors indicative of ransomware, such as mass file encryption, unauthorized process execution, or unusual network connections.
7. Incident Response Plan
- Develop and Test an Incident Response Plan: Create a comprehensive incident response plan specifically for ransomware attacks. This plan should outline roles, responsibilities, communication strategies, and technical steps for containment, eradication, and recovery.
- Tabletop Exercises: Conduct regular tabletop exercises to test the effectiveness of your incident response plan and identify areas for improvement.
8. Email and Web Security
- Email Filtering: Implement robust email filtering solutions to block malicious attachments, phishing links, and spam.
- Web Content Filtering: Use web content filtering to prevent access to known malicious websites, and to block downloads from untrusted sources.
By proactively implementing these recommendations, organizations can significantly enhance their resilience against ransomware attacks and mitigate the risks associated with evolving threat actor tactics.







