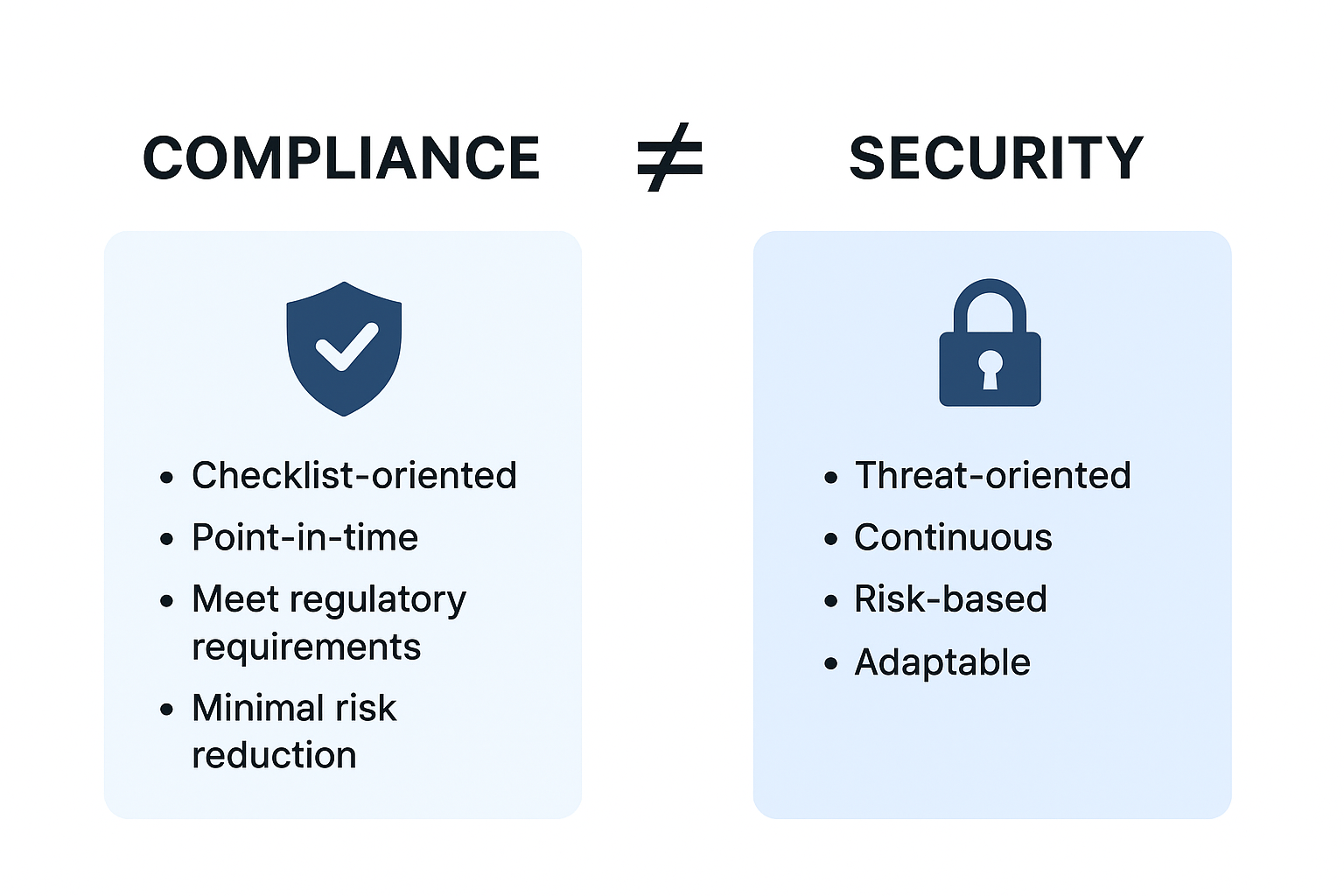
When organizations think about cybersecurity, the conversation often starts with compliance. ISO 27001, PCI-DSS, HIPAA, GDPR, NIS2… frameworks and regulations designed to protect sensitive data and establish minimum standards for risk management. Achieving compliance is often seen as the ultimate milestone: once the certificate is obtained or the audit is passed, the company is considered “secure.”
But here’s the uncomfortable truth: compliance does not equal security. Passing an audit means you have proven that, at a given moment in time, you can demonstrate the existence of certain policies, controls, and procedures. It doesn’t necessarily mean that those controls are effective against real-world threats, nor that your organization is resilient against modern adversaries.
In short: compliance is a starting point, not a finish line.
The limits of compliance-driven security

Compliance frameworks are essential. They provide structure, accountability, and benchmarks that align organizations to recognized security baselines. However, when compliance becomes the only driver of a security program, several limitations emerge:
- Point-in-time validation
Audits and certifications are typically annual or biannual. Threat actors, however, operate 24/7. A server patched only during “audit season” may remain vulnerable for months in between. - Checklists over context
Many controls are interpreted as “checkbox exercises”. For instance, a requirement to “maintain access control” may be satisfied by having a password policy on paper, even if users continue to reuse weak passwords. - Compliance blind spots
Compliance frameworks are not exhaustive. They focus on common denominators but often lag behind new attack techniques. For example, while an audit may check whether antivirus software is installed, it might not properly assess the organization’s ability to detect and respond to living-off-the-land attacks or advanced lateral movement. - False sense of security
A fully compliant organization may mistakenly believe it is fully protected. This mindset leads to complacency, the most dangerous vulnerability of all.
Security-driven approach: Shifting the paradigm

A true security strategy is threat-driven, not compliance-driven. Instead of asking, “What do we need to pass the audit?” the right question is, “How might an attacker breach us today?”
This shift requires:
- Threat modeling: Mapping assets, identifying likely adversaries, and analyzing attack vectors that go beyond compliance checklists
- Real risk exposure analysis: Understanding where vulnerabilities meet business-critical assets, and prioritizing based on impact
- Continuous validation: Security controls must be tested regularly through penetration testing, red teaming, and purple teaming exercises, not just reviewed during audits
Attackers don’t care whether you are ISO-certified. They care about exploitable misconfigurations, weak identity management, or unmonitored endpoints. Compliance may stop a regulator, but it won’t stop ransomware.
Case study 1: Compliant but compromised

A financial services firm successfully passed multiple compliance audits, including PCI-DSS. Documentation was pristine, and their policies were well-structured. However, during a red team engagement, attackers gained initial access through a phishing campaign targeting employees. The email mimicked an internal HR communication and redirected victims to a fake single sign-on (SSO) portal that captured corporate credentials.
Using these stolen credentials, the red team leveraged MFA fatigue attacks to bypass multi-factor authentication and obtained access to the internal VPN. Once inside, network segmentation gaps allowed lateral movement toward critical systems. Through PsExec and WMI, attackers enumerated hosts, harvested cached credentials using Mimikatz, and escalated privileges up to domain administrator within days.
The compliance framework had never required the company to simulate phishing attacks, test the resilience of MFA, or perform adversary emulation. Logging existed, but SIEM correlation rules were incomplete, and alerts went unnoticed due to lack of 24/7 monitoring. As a result, despite being “compliant”, the company was breached in less than a week, proving that paper-based controls cannot substitute for real-world readiness.
Case study 2: A security-first mindset

In contrast, a technology startup without formal certification implemented continuous monitoring, internal threat hunting, and regular purple team exercises. Their SOC operated a centralized SIEM and EDR stack, with detection rules mapped to MITRE ATT&CK techniques. Routine internal drills simulated phishing, privilege escalation, and data exfiltration scenarios.
When attackers attempted to exploit a misconfigured AWS S3 bucket via public access, GuardDuty alerts flagged unusual outbound traffic from a compromised API key. Automated SOAR playbooks immediately revoked the credentials and quarantined the affected container instance. Meanwhile, the incident response team validated the event through CloudTrail and VPC Flow Logs, confirming the containment.
Because of this culture of constant validation, the intrusion was neutralized before any sensitive data was accessed. The company used the incident as a learning opportunity, updating IAM policies and expanding anomaly detection rules. Though not yet “compliant” with any major standard, the startup had built true operational resilience, turning compliance from a goal into a natural byproduct of a robust security-first mindset.
Turning compliance into real security
Compliance should not be dismissed. Instead, it should be integrated into a broader, threat-driven security program. Here’s how organizations can bridge the gap:
- Continuous security testing
Move beyond static audits. Perform penetration tests, red teaming, and adversary emulation (e.g., based on MITRE ATT&CK) to validate controls against real-world TTPs. - Automation and continuous monitoring
Implement SIEM, SOAR, and EDR solutions to detect and respond to threats in real time, rather than relying on manual checks during audits. - Human factor focus
Most frameworks include vague requirements for training. Replace generic awareness sessions with practical simulations: phishing exercises, social engineering tests, and incident response drills. - Embed security into DevOps
Compliance frameworks often cannot keep up with the pace of modern development. By integrating security scanning, threat modeling, and secure coding practices into CI/CD pipelines, organizations prevent vulnerabilities before they reach production. - Risk-based prioritization
Not all compliance requirements carry the same operational weight. Organizations should map compliance controls to actual risk scenarios, ensuring that investment aligns with business-critical exposures.
Conclusion
Compliance frameworks are valuable, but they are not enough. They provide a baseline, not a guarantee. A certificate proves you met yesterday’s standards, it doesn’t prove you can survive today’s attack.
Security requires a mindset: continuous learning, testing, and adaptation. Compliance is like a seat belt: it reduces risk, but it doesn’t drive the car for you. A true security program combines compliance with a proactive, threat-driven approach, ensuring not just audit readiness, but resilience against real adversaries.
In cybersecurity, passing the test is not the goal. Surviving the attack is.
These Solutions are Engineered by Humans
Did you learn from this article? Perhaps you’re already familiar with some of the techniques above? If you find cybersecurity issues interesting, maybe you could start in a cybersecurity or similar position here at Würth IT Italy.







