Red_Team_Script, a Powerful Script for Red Team Activities

Cybersecurity is a discipline that deals with protecting computer systems and digital data from attacks and security breaches. With the increasing use of technology and dependence on computer systems in everyday life, cybersecurity is becoming increasingly important.
But what are the risks for those who don’t know how to protect themselves?
Online security risks can include:
- Viruses
- Malware
- Phishing
- Theft of personal data
- Hacker attacks
These risks can have serious consequences not just for individuals, such as identity theft or damage to their devices, but also for companies and organizations – for which cybersecurity is an even bigger concern. They have responsibilities to their customers, employees, and partners to protect their data and systems, and must therefore take appropriate security measures such as IT security audits of their infrastructure through vulnerability assessment and penetration testing activities.
To protect oneself and one’s online activities, it’s important to adopt appropriate security practices such as using strong and unique passwords, activating two-factor authentication, installing up-to-date security software, and being aware of online threats.
Here at Würth Phoenix, I carry out penetration testing and vulnerability analysis. Over the years, together with the Cybersecurity team, we have developed a script to manage and partially automate some of the most significant processes and tests used in Vulnerability Assessment and Penetration Testing (VAPT).
The script in question is called Red_Team_Script and looks like this:
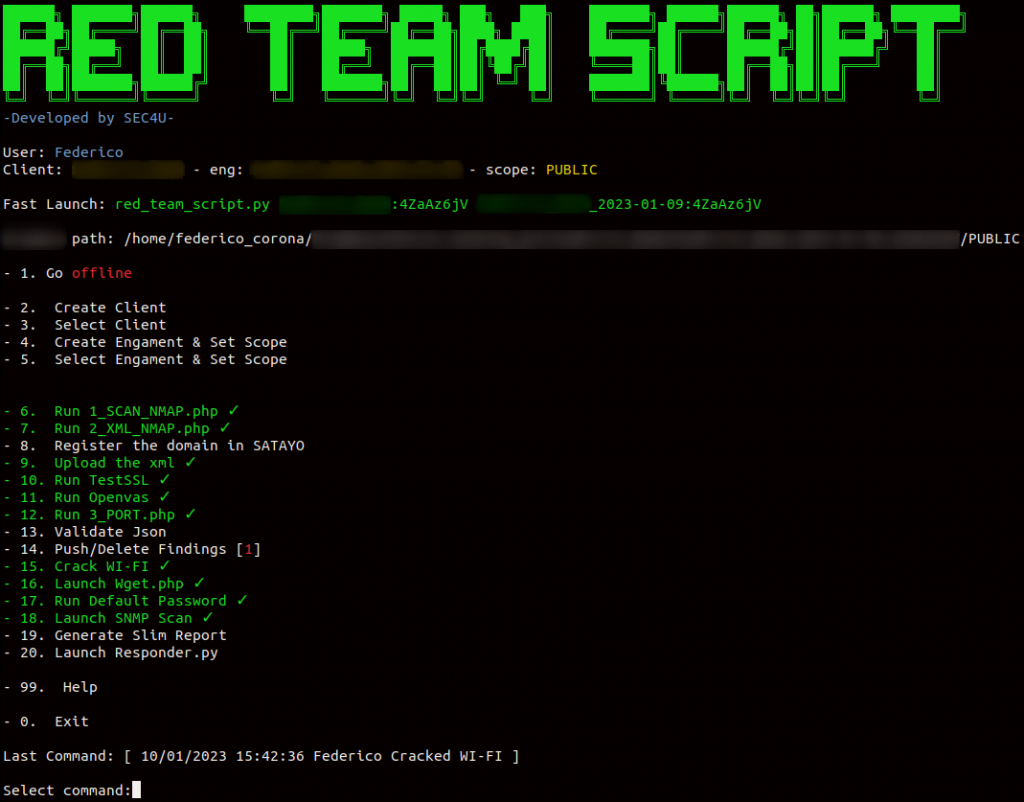
Red_Team_Script allows a team to work in parallel on the same task, with continuous updates on what is being done by other colleagues and the ability to use the data they obtain immediately. To make this possible, we created a customized and optimized Cloud space template to manage the data collected during the task’s various activities.
Here’s a small example:
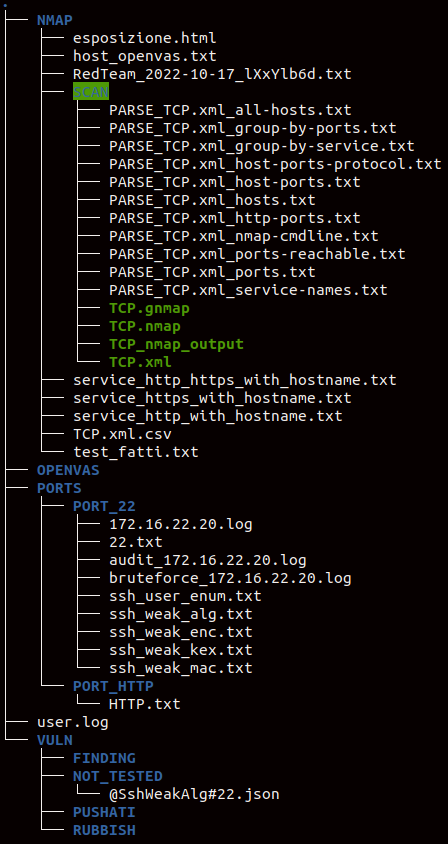
Finally, the collected data is uploaded to pentest.ws, a service that will render this data for you in a convenient and functional graphical version.
It also gives us the possibility to manage the entire reporting part at significantly reduced time through the use of templates, and an automated findings creation process with the help of APIs.
This was a brief overview, but if you are interested in delving deeper into cyber security and the penetration test part in detail, don’t miss my upcoming blogs where I’ll talk in a more in-depth and technical way about the wide array of functionalities of Red_Team_Script.
If you spend more on coffee than on IT security, you will be hacked. What’s more, you deserve to be hacked.
Richard Clarke
These Solutions are Engineered by Humans
Did you learn from this article? Perhaps you’re already familiar with some of the techniques above? If you find security issues interesting, maybe you could start in a cybersecurity or similar position here at Würth Phoenix.







