There’s been a lot of talk in recent days about the seizure of the underground forum RAMP. There’s little to add to this issue, which has already been extensively written about. An excellent summary is available in this BleepingComputer article. What I’d like to highlight in this article, however, is how the main players in the ransomware attack landscape (for which RAMP had become the reference forum in which to advertise their activities and find new affiliates) are moving in the wake of the seizure. These movements concern another well-known underground forum, RehubCom.
The RehubCom forum has emerged as a significant platform within the cybercrime underground, particularly as a successor to high-profile forums like XSS. It serves as a hub for the trade of stolen credentials, malicious software, and unauthorized access to corporate environments.
RehubCom was reportedly launched by a former moderator of the prominent dark web forum XSS (originally known as DaMaGeLaB). The platform’s rise coincided with law enforcement pressure on other major hubs, such as the arrest of XSS administrators and the closure of its domain. As of early 2025, the forum maintained a significant presence with approximately 15,215 members and over 200,000 posts.
On the very day of the seizure (January 28, 2026), a user who couldn’t be described as just any user signed up to the RehubCom forum. DragonForce signed up.

DragonForce is a well-known and important name in the ransomware gang landscape, a prominent ransomware threat actor that emerged in August 2023. While it originated as a Malaysian-based hacktivist group with pro-Palestinian sentiments, it has since evolved into a highly organized and profit-driven ransomware-as-a-service (RaaS) cartel. The group is characterized by its hybrid nature, blending political motivations with sophisticated financial extortion tactics.
Initially known for hacktivist activities like DDoS attacks and website defacements, DragonForce transitioned to a classic multi-extortion ransomware model. In early 2025, the group rebranded as a “ransomware cartel,” offering a unique business model that allows affiliates to “white-label” their own ransomware brands while utilizing DragonForce’s robust infrastructure, including administration panels, negotiation tools, and the “RansomBay” leak platform . This model typically provides affiliates with an
80% revenue share.
DragonForce is noted for its aggressive stance toward other cybercriminal groups. It has reportedly targeted and even overtaken the infrastructure of rival ransomware groups like RansomHub and BlackLock. Despite its origins, the group claims to follow a “moral compass,” publicly stating it avoids targeting certain healthcare facilities.
DragonForce’s influence within the RAMP forum was so strong that it even earned its presence in the forum’s official logo.

DragonForce’s first post (published on the exact same day, January 28th) on the RehubCom forum was obviously aimed at advertising its services.
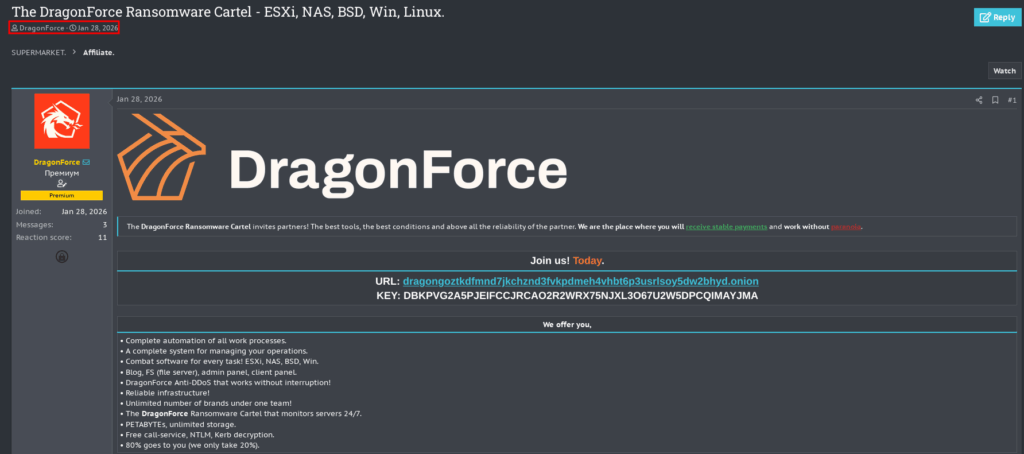
This post was published in the Affiliate section of the forum. Within the same section, another ransomware gang has also started advertising its services. This is the ransomware gang The Gentlemen, who posted on Monday, February 2nd.
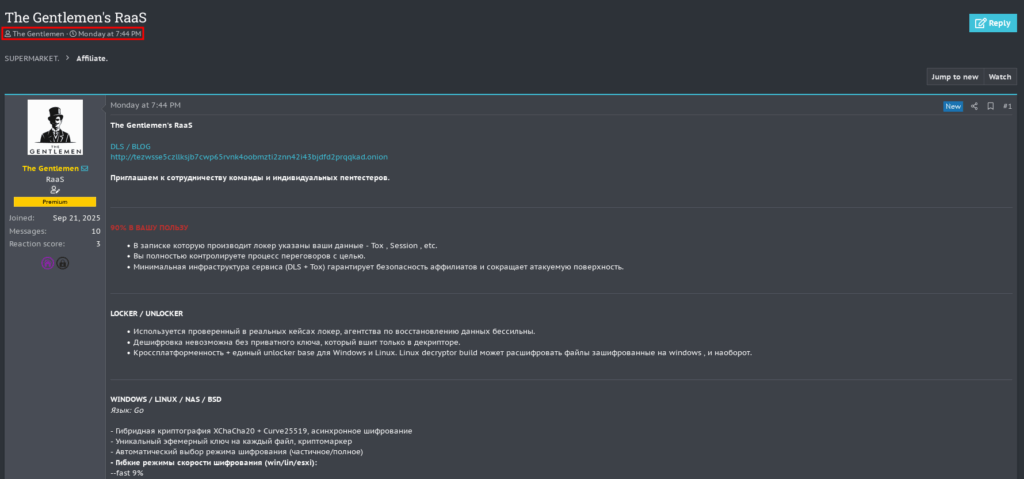
In the past few hours, DragonForce’s current strong influence within the ransomware gang landscape has been confirmed. The RehubCom forum logo has also been modified, incorporating part of the DragonForce logo, just as was done in RAMP.

DragonForce’s activity has certainly been somewhat slow in recent weeks, with only 9 victims reported in January 2026 on its data leak site, compared to, for example, 34 victims reported during the month of December 2025. We’ll see in the coming weeks if these DragonForce sponsorship activities bring visible results.
Other ransomware actors are also active within the RehubCom forum. These include Anubis, Nova (who was banned from the forum, however), Lockbit, and DevMan.







