In this article, we’re going to explore an example of the process used to perform the initial steps of creating ad hoc detection rules based on specific events that mark the world of cyber security. Specifically, starting from a real case, we’ll see the study and analysis carried out to create a rule to monitor possible data exfiltration through a particular technique used by the Akira ransomware gang. Obviously, we’ll start off with an overview of the Threat Actor group so we can understand the context in which they operate, and show how this knowledge helps construct a correct and efficient detection rule.
Who is the Akira Ransomware group?
Reports indicate that Akira is a Threat Actor group that has been in the spotlight since March 2023. To date, estimates suggest this group has carried out more than 250 attacks. Their scope is very wide, as evidenced by the number of attacks claimed in just a year and a half. Several Italian companies have also become their target.
Some analyses of the TTPs (tactics, techniques and procedures) used by this group show that initially, the preferred targets were Windows systems, but attack variants for Linux targets were quickly discovered. The next section will discuss some of the main attack methods and the relevant TTPs used, but for now, let’s concentrate on the online footprint of this group.
A common feature of the various attacks claimed by this group is the absence of a ransom note or instructions for payment after the compromise of systems. In fact, this information is only provided once the victim of the attack gets in touch with the ransomware gang. Nevertheless, it’s currently estimated that the Akira group has earned more than $40 million through these criminal activities. As one can imagine, payments are typically made through the use of Bitcoin to cryptocurrency wallets provided by these threat actors.
The pressure on the victim to force him to pay and re-obtain access to the data is increased by the use of the double extortion technique. Briefly, this technique consists of threatening to publish the data, of which the attacker has gained possession, via his own Data Leak Site. In this way, “double damage” is created, because in addition to the interruption of service caused by the encryption of files, a number of files containing sensitive or private data will be leaked and thus be publicly accessible.
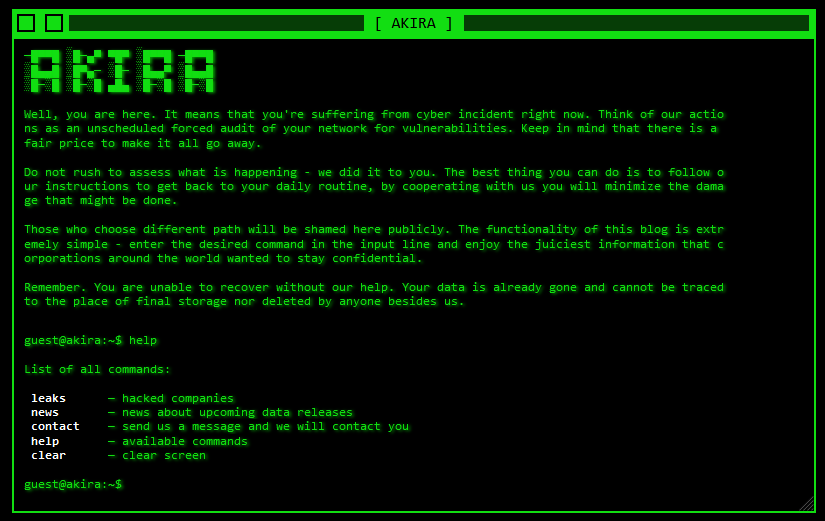
The Data Leak Site of this group has some very retro graphics. Its particularity is its navigation mode: in fact it acts just like a real console, in which it’s possible to execute certain commands. Specifically, there is a command to display a list of attacked companies for which file sharing has already taken place, and a command to open a list containing the “latest news” concerning attacked targets and the group’s next victims and their exfiltrated data. Of course, the command to get in touch with the gang is not missing. At the time of writing this article, the latest news shared is dated May 30th, 2024.
Here’s a screenshot of the group’s home page:
What techniques does Akira use?
Once we have confirmed the online presence of this group of Threat Actors, we can move on to analyze the main TTPs used. Obviously, it’s impossible to explore and discover all or even most of the techniques used, so I’ll give you a general overview of the information reported by MITRE ATT&CK as our aim is to build detection rules that cover certain techniques.
For the Discovery phase, two tools are mainly used with the aim of identifying remote hosts within the victim’s networks, and consequently, exploiting public facing services or applications. These tools are Advanced IP Scanner and MASSCAN.
For the Credential Access phase, the group exploits failures in multi-factor authentication (MFA) and some known vulnerabilities in VPN software. Specifically, the main vulnerabilities exploited in this phase are CVE-2020-3259 and CVE-2023-20269,which are used to breach VPN services that do not have active two-factor authentication.
To maintain control over hosts, AnyDesk or PuTTy are typically used, which are also software tools typically used by system administrators themselves, thus making it difficult to detect their being used for malicious purposes, and at the same time allowing direct access to compromised hosts and carrying out Lateral Movement or Privilege Escalation.
Taking a look at the main exfiltration tools used, we can mention the well-known FileZilla and RClone, but also the CloudFlare tunnels, which I will analyze in this article in order to show you how they work and then to create a rule to detect their use.
Finally, once the data has been exfiltrated, the files are also encrypted in place in order to create further problems for the victim.
This table briefly summarizes the techniques and tools used:
| MITRE ATT&CK Tactic | MITRE ATT&CK Techniques | Tools |
| Discovery | Remote System Discovery (T1018) | Advanced IP Scanner |
| MASSCAN | ||
| Credential Access | Valid Accounts (T1078) | – |
| External Remote Services (T1133) | ||
| Command and Control (C2) | Remote Access Software (T1219) | AnyDesk |
| PuTTy | ||
| Exfiltration | Exfiltration Over Web Service: Exfiltration to Cloud Storage (T1567) | Rclone |
| FileZilla | ||
| Tunnel CloudFlare |
CloudFlare Tunnel analysis
Cloudflare tunnels provide a secure way to connect resources to the Cloudflare network without needing a routable public IP address. The official CloudFlare documentation specifies that with these tunnels, traffic is not sent to an external IP, but instead a lightweight daemon (cloudflared) creates outbound connections exclusively to Cloudflare’s global network. Cloudflare’s tunnels can connect HTTP web servers, SSH servers, remote desktops and other protocols securely to Cloudflare.
There are various methods for creating one of these tunnels. Without going into too much detail on the systemic aspects that distinguish them, the following are some examples to start thinking about how to construct a detection rule that can detect these operations.
<binary>.exe tunnel run <TUNNEL_NAME> -token <TOKEN>
<binary>.exe tunnel run <TUNNEL_NAME> --credentials-contents '{<JSON_DATA>}'
<binary>.exe tunnel run <TUNNEL_NAME> --config /home/user/.cloudflared/config.yml
<binary>.exe tunnel run <TUNNEL_NAME> -credentials-file /home/user/.cloudflared/<TUNNEL_NAME>.json
As can be seen in all four of these example commands, it’s necessary to launch the executable followed by the “tunnel run” argument. The name of the executable would originally be connected in some way to CloudFlare, but as it’s easily customizable, it doesn’t provide any useful information for detection purposes. Instead the above-mentioned argument must always be present in that format. At this point we know that we need to detect a command line that makes use of the keywords “tunnel” and “run”.
Since we want to detect these tunnels at the moment of creation, we can refine the list of arguments we are looking for by also adding the flags -token, –credentials-contents, –config and -credentials-file. Unlike “tunnel run”, these do not have to appear in the command all at once, but the presence of one of them is enough.
At this point, the detection rule that can be written in EQL should look like the following:
"process where (event.category : "process" and process.command_line : "* tunnel *" and process.command_line : "* run *" and process.command_line : ("*-token *", "*-credentials-contents *", "*-config *", "*-credentials-file *", ))"These Solutions are Engineered by Humans
Did you learn from this article? Perhaps you’re already familiar with some of the techniques above? If you find cybersecurity issues interesting, maybe you could start in a cybersecurity or similar position here at Würth Phoenix.






