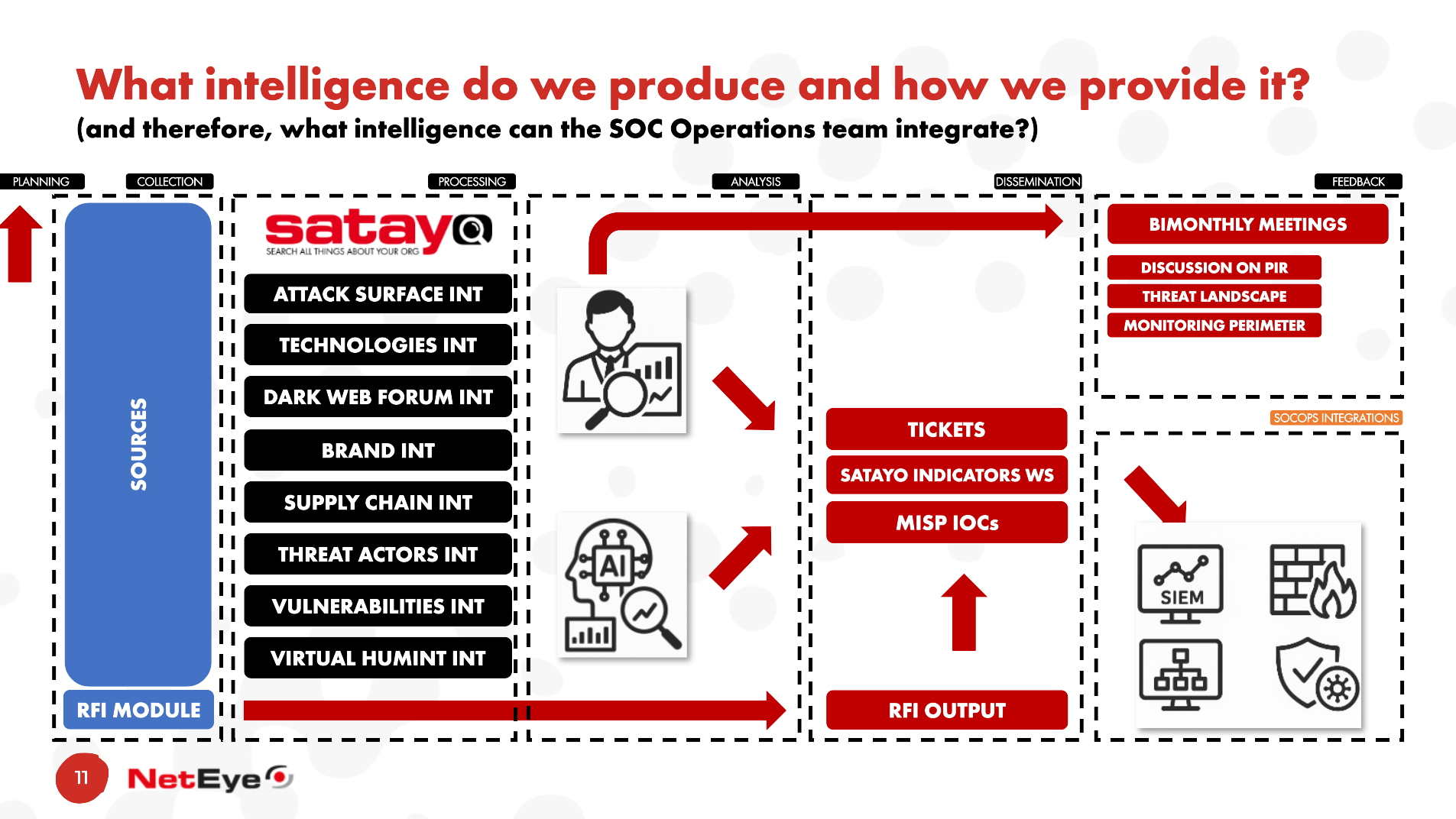
Meet The CDC! Our Innovative Concept For A Modern SOC
Introduction If you work in the Cyber Security field, you probably know how a traditional Security Operations Center (SOC) operates. It is often characterized by a demanding workload, extensive night shifts, and high personnel turnover. These factors can lead to alert fatigue among analysts and a lower morale. The stressful nature of such environments can…
Read More