Integration of Centreon Plugins into NetEye Extension Packs
With the end of 2021 we’ve release the first version of the NetEye Extension Packs project that helps customers and consultants on their monitoring implementations and more (see Introducing NetEye Extension Packs | www.neteye-blog.com for details).
Now our focus is to extend the ouf of box infrastructure coverage of our monitoring plugins.
With this target in mind we looked at the open source project of our friends from Centreon. They built an exiting open source project to manage Nagios compliant monitoring plugins (see GitHub – centreon/centreon-plugins).

Cool, so how we can integrate and contribute in a smart way the Centreon open source monitoring plugins?
We analyzed a sample of plugins and we found some common items.
Basic Command Templates
Many plugins on Centreon use the same arguments on command calling. So why not define a common template? We can use the concept of Command Templates implemented on Icinga Director which helps define a common set of parameters across many similar command definitions.
We created three main families of Plugins based on the technology used on monitoring checks:
- nx-c-centreon-plugins-snmp for monitoring based on SNMP protocol using arguments like community, and for the new SNMPv3 authentication phrase/protocol
- nx-c-centreon-plugins-restapi for monitoring based on RestAPI methods, using the latest applications and Cloud monitoring
- nx-c-centreon-plugins-ssh for monitoring based on the Secure SHell (SSH) protocol, useful for agentless monitoring and blackbox appliances
Each template can be used by multiple plugins without rewriting all common arguments, but just adding any special arguments for that one specific check.
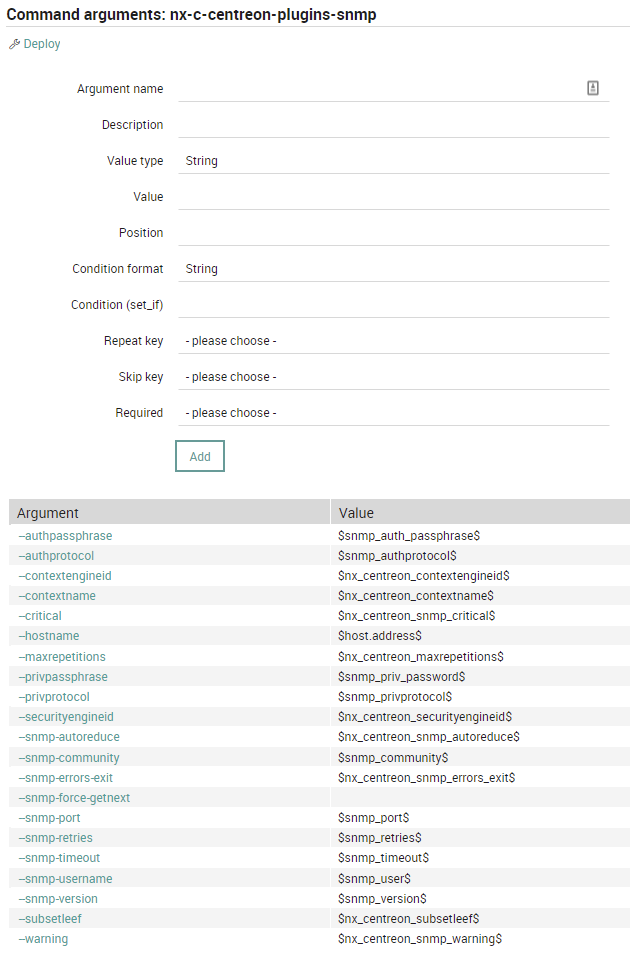
Common Datafields
We noticed that other “general” fields are used on more or less all plugins, so we decided to add a common datafield to Icinga Director.
These fields are:
- Hostname the target host to which the execution command will be sent, this usually corresponds to the host.address variable on NetEye
- Mode this is the common field list of modes available for specific plugins – we created a drop-down list from which the user can choose the mode (ex. cpu-load)
- Component strictly related to mode, this represents the component that you want to check with a specific mode (ex. battery, PSU, drive)
- Warning/Critical a warning or critical threshold for the execution of check – sometimes this field is follow by a word (like usage or health) to set multiple thresholds.
- Statefile Directory a directory on some filesystem that will be used for one or more checks to store statefiles. We decided to use
/neteye/shared/icinga2/data/lib/centreon-plugins. This directory should have icinga user access, and thus it’s created automatically during NEP installation.
Final considerations
So we’re releasing a new pack named NEP Centreon Plugins Base that allows for an easy way to integrate into NetEye all monitoring plugins provided by the Centreon Community.
In this way we can also reduce the possibility of typos as well as the effort when starting from scratch whenever you want like to integrate a new Centron Plugin.
The current available integrations on NetEye 4.24 are:
- Network Dell Switch — NetEye User Guide
- Network Kemp Load Balancer — NetEye User Guide
- Network Palo Alto Fireall — NetEye User Guide
- Storage IBM — NetEye User Guide
- Storage NetApp — NetEye User Guide
Other new integration are on the roadmap for upcoming releases. We’ll keep it up-to-date on the dashboard project (NetEye Extension Packs – Issues – JIRA (atlassian.net)).
Do you need a plugin that’s not already nep-implemented? Check if it’s available in the Centreon Plugin Packs Catalog and contact us through our official ways sales, consultants, support team. We are quite happy collect your feedbacks and prioritize our work based on that.
These Solutions are Engineered by Humans
Did you find this article interesting? Does it match your skill set? Our customers often present us with problems that need customized solutions. In fact, we’re currently hiring for roles just like this and others here at Würth Phoenix.







