Embedding Threat Intelligence into Your Security Operations
Producing actionable intelligence must be the mindset that every Threat Intelligence analyst must set as their primary objective.
The problem of properly integrating Threat Intelligence into Security Operations processes is a recurring one. In this article, I aim to describe the integration process we, at Würth IT, have implemented, which allows us to produce actionable and consumable intelligence on a daily basis across our organization and those of our clients.

Many organizations subscribe to intelligence feeds or intelligence platforms driven by the general market perception that up-to-date intelligence is essential to defend against threats. However, feeds alone and access to a Threat Intelligence Platform (TIP) are not enough if the intelligence remains within those channels without being properly utilized and leveraged.
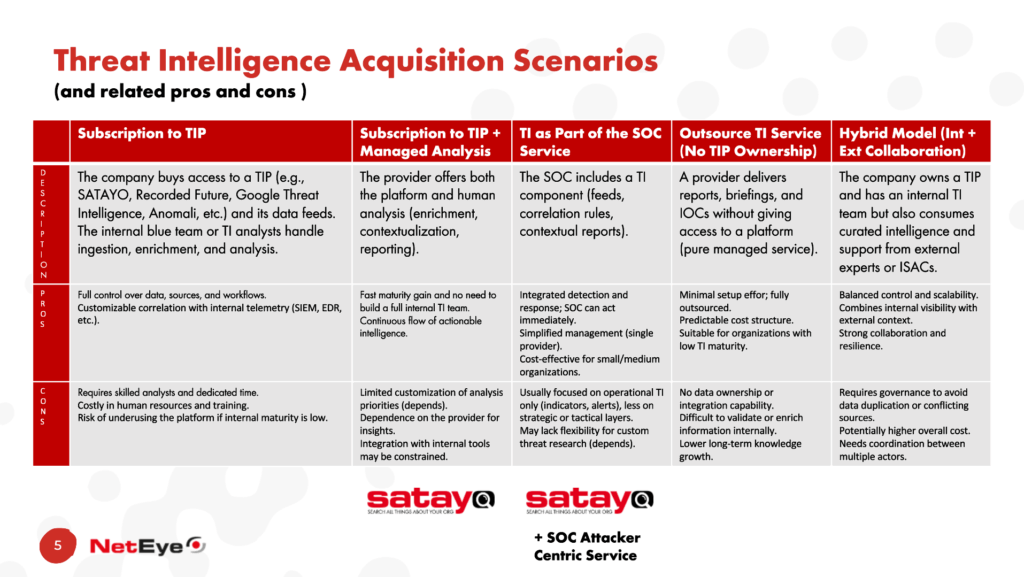
Let’s start with a list of scenarios that provide us with the opportunity to acquire Threat Intelligence within an organization, listing the possible advantages and disadvantages for each scenario:
- Subscription to TIP
- Subscription to TIP + Managed Analysis
- TI as Part of the SOC Service
- Outsource TI Service (No TIP Ownership)
- Hybrid Model (Internal + External Collaboration)
Once we’ve met the first requirement of acquiring potentially actionable and consumable Threat Intelligence, we now need to build a consistent process that allows us to integrate Threat Intelligence into our Security Operations processes.
The approach we propose must be aligned with the Threat Intelligence Lifecycle. We must use this as a cornerstone, a lifeline with which to build a journey that will ensure the efficiency of our processes.
The first activity to be carried out along our journey is to record the PIRs (Priority Intelligence Requirements). This activity is carried out in the PLANNING phase.
A Priority Intelligence Requirement (PIR) is a specific, high-level question or information need that guides the collection, analysis, and dissemination activities of a Threat Intelligence (TI) program. PIRs represent the most important intelligence priorities of an organization – the ones that directly support decision-making, risk management, and operational readiness.
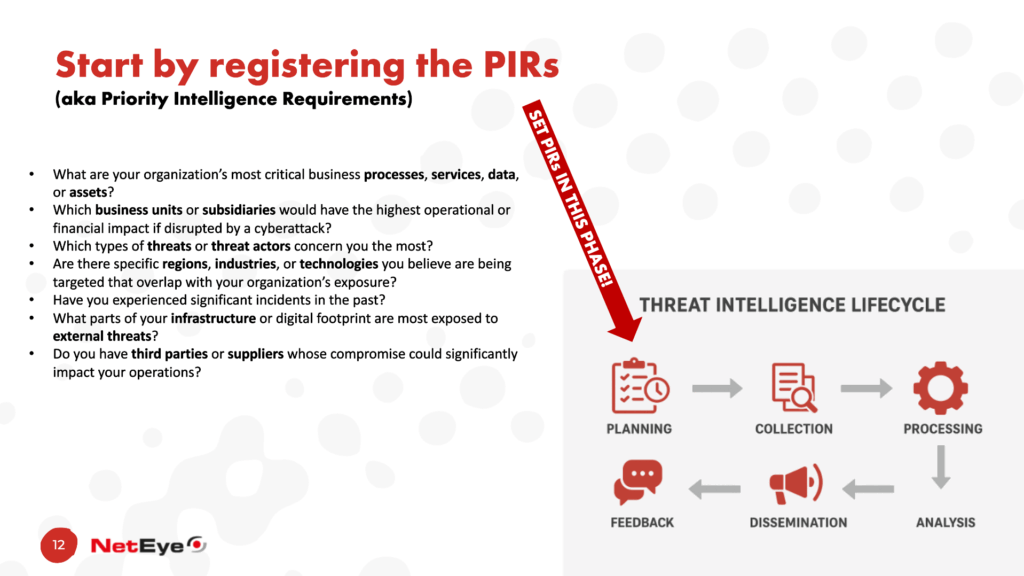
Once the PIRs have been defined (which will still need to be monitored and updated periodically), we can continue our journey with the subsequent phases.
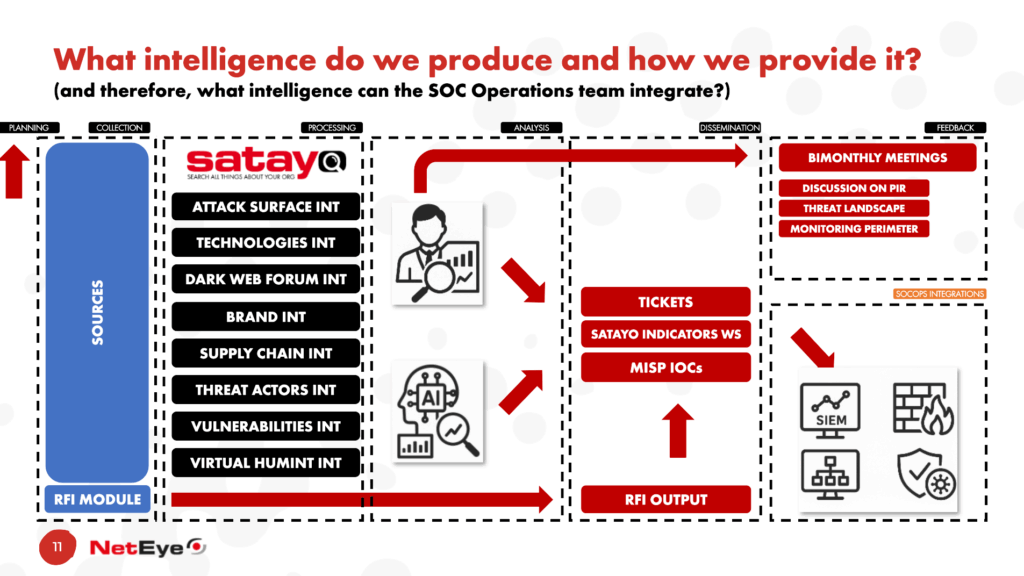
Within the Threat Intelligence processes, we’ll have information available to use as input. This information constitutes the sources, which are collected in the COLLECTION phase of the Threat Intelligence Lifecycle.
The primary goal of the PROCESSING phase is to transform raw data into a usable, standardized, and accessible format for analysis.
Raw data, such as logs, IoCs, malware samples, dark web posts, or social media chatter, often arrives in multiple formats and levels of reliability. The PROCESSING phase ensures this data is:
- Cleaned (removing noise and duplicates)
- Normalized (converted to a consistent schema)
- Enriched (correlated with context and metadata)
- Stored (indexed and made searchable for analysts and automated systems)
What types of intelligence can a threat intelligence team produce? While I don’t claim to have a definitive list, I’ll provide a series of types that we manage on a daily basis within our team.
- Attack Surface Intelligence: the continuous discovery and monitoring of an organization’s exposed assets – such as domains, IPs, applications, and cloud services – to identify vulnerabilities and potential entry points before adversaries can exploit them
- Technologies Intelligence: the collection and analysis of information on technologies used across the organization or its sector (e.g., software stacks, CMS, cloud services) to assess exposure, detect outdated systems, and anticipate threats exploiting specific technologies
- Dark Web Forum Intelligence: the monitoring and analysis of discussions, advertisements, and leaked data across underground forums and marketplaces to identify emerging threats, data breaches, or threat actors targeting the organization or its industry
- Brand Intelligence: the detection of misuse of an organization’s brand – such as fake websites, phishing domains, fraudulent social media profiles, or logo abuse – to prevent reputation damage and fraud
- Supply Chain Intelligence: the assessment of cyber risks within third-party vendors, partners, and suppliers by tracking their exposure to breaches, vulnerabilities, or threat actor activity that could indirectly impact the organization
- Threat Actors Intelligence: the profiling and tracking of threat groups and individuals – including their motivations, capabilities, infrastructure, and tactics – to anticipate their actions and enhance defensive readiness
- Vulnerabilities Intelligence: the identification, prioritization, and contextualization of security vulnerabilities by correlating technical data with real-world exploitation trends, enabling focused patching and risk mitigation
- Virtual Humint Intelligence: the collection of information through human-driven engagement in digital environments – such as dark web communities or closed chat groups – to gain insights into threat actors’ intentions, plans, and emerging operations
The ANALYSIS phase can be performed by human analysts or, for repetitive tickets where human evaluation is not necessary, by AI systems.
After the ANALYSIS phase comes the DISSEMINATION phase. Our current process involves disseminating the intelligence we generate across various channels.
The largest portion is undoubtedly managed through tickets, which provide a detailed analysis of the evidence. Tickets may contain indicators of compromise and/or attack (e.g., IP addresses, host names, hashes, domains, URLs, email accounts, etc.), which are then made available in raw format through a specific web service or in enriched format through the MISP platform.
The ability to make indicators available in raw format allows them to be consumed through tailored configurations. A concrete example is the use of IP indicators as input by a firewall device to automatically use them as elements to block within a traffic deny rule.
Another concrete example is the use of an email account indicator, which can result in the resetting of the account’s login credentials if it has been identified as an indicator as part of a data breach or as part of an analysis of an infostealer log.
The same indicators made available, enriched and correlated with analysis, within MISP also allow them to be consumed, for example, within a SIEM, with a series of active threat hunting rules that can continuously check whether events related to these indicators are being collected.
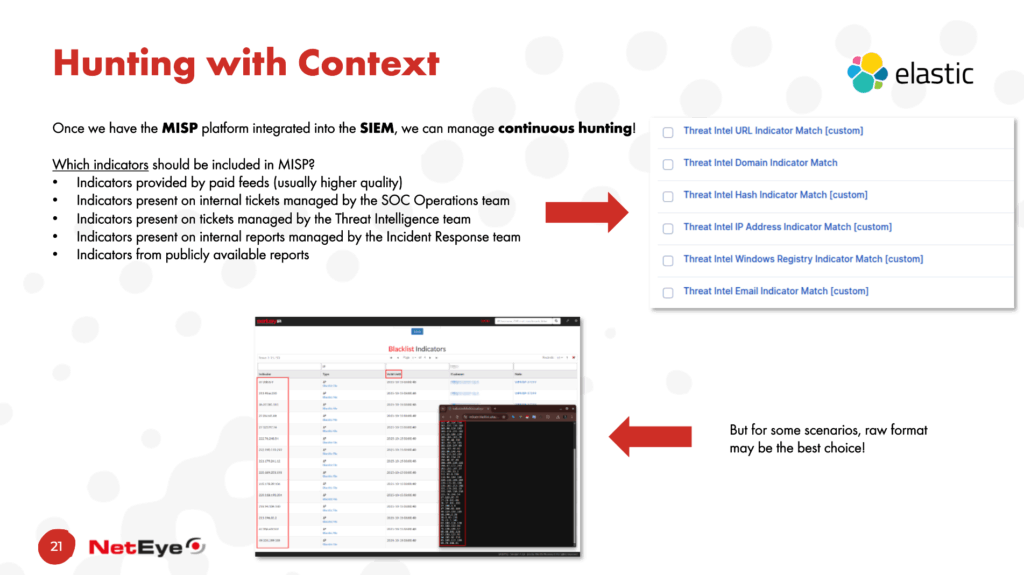
The FEEDBACK phase of the Threat Intelligence Lifecycle is sometimes overlooked. This phase is crucial for periodically verifying that the intelligence being generated is being used effectively.
For our team, the FEEDBACK phase coincides with a bimonthly meeting we organize with our clients. During this meeting, the PIRs are reviewed, the client organization’s threat landscape (e.g., sector and country) is described, and the monitored perimeter is double-checked to ensure its consistency. Organizational perimeters are often fluid, as a result of the acquisition of new companies and the use of new technologies.
Another element that, in our opinion, facilitates the easier integration of Threat Intelligence into Security Operations processes is the provision of a Request For Information (RFI) module. This tool can be used by different teams to manage analysis requests, on different topics, addressed to the IT team. These requests help build trust between different teams and highlight the value of Threat Intelligence within daily processes.
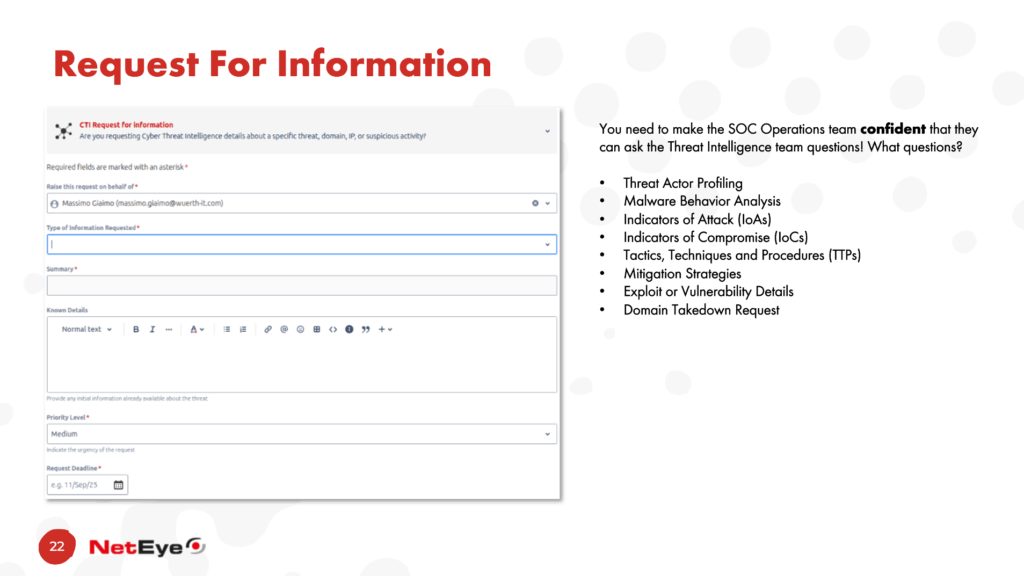
So, if you as an organization are on Day One of your journey to integrate Threat Intelligence into your Security Operations processes, what should you do?
Start with one assumption: Threat Intelligence within SOC Operations is necessary.
- Start by setting up PIRs
- If your TI provider doesn’t know what PIRs are, change providers
- There will always be someone who will question the usefulness of TI: measure it (but that’s another topic, another post is needed…) so you can disprove those who claim it
- Acquire TI from those who are accustomed to producing TI, not from those who are merely consumers
- The more you consume IT, the more convinced you will be of its usefulness
- Threat intelligence must be actionable. This means it must be consumable through the channels used by SOC Operations.
Want to know more?
If you want to learn more about our Threat Intelligence Platform SATAYO and about the Security Operations processes we can implement within your organization, consult the online guide or request a demo of the platform.







