Favicon Intelligence – Detecting Clones Of Official Web Services
In this article, I want to introduce an important new development we have introduced within the SATAYO Threat Intelligence Platform (TIP).
Our experience has shown that favicons, those seemingly innocuous icons used in browser tabs and bookmarks, can be a rich and often overlooked source of intelligence. By systematically analyzing these artifacts, we’ve established a process that enables pivoting from known infrastructure associated with a monitored organization to third-party services or suspicious assets reusing the same icons. This capability has proven critical in brand protection, helping detect early signs of impersonation, phishing infrastructure, or unapproved brand usage.
Let’s walk through how this process fits into each phase of the Threat Intelligence Lifecycle, reinforcing the broader value of favicon-based intelligence:
What are favicons?
Favicons (short for “favorite icons”) are small, square images associated with a specific website or web page. They are typically displayed in:
- The browser tab, next to the page title
- Bookmarks or favorites lists
- Browser history entries
- Mobile browser tiles or shortcuts
Technical Details
- Size: Common sizes are 16×16, 32×32, or 48×48 pixels
- File formats: .ico, .png, .svg, and .gif
- Defined in HTML: Usually linked in the section of a webpage like this:
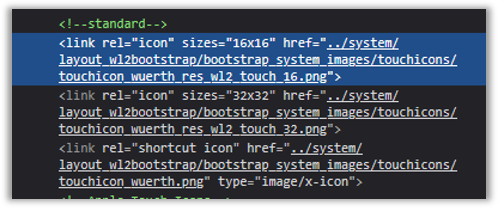
Purpose
- Improves user experience by making websites easily recognizable
- Enhances branding and professionalism
- Helps with navigation among multiple open tabs or saved pages
Favicon-related intelligence process
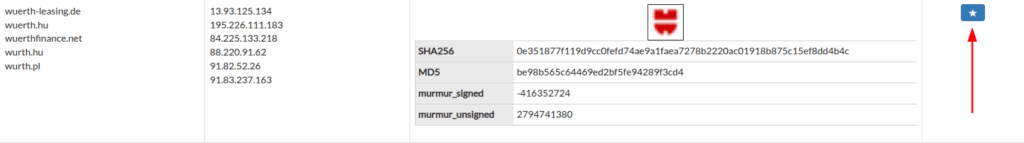
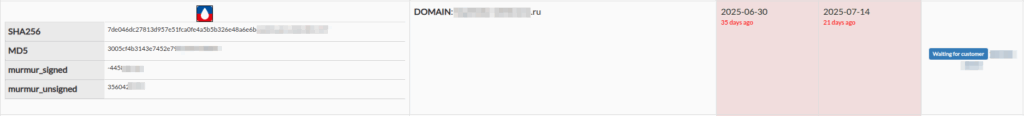
The hash (SHA256, MD5, etc.) of these icons can be used to pivot to other URLs exposing webpages with the same favicon.
Census of technologies in SATAYO
The first step (COLLECTION phase) in obtaining intelligence from favicons involves obtaining the favicons associated with the services managed directly by the organization being monitored.
Favicons can be collected using third-party services, such as the Shodan and Validin platforms, or using in-house scrapers that analyze the HTML code of pages to identify favicons.
The favicons thus collected are then displayed within the Technologies section of SATAYO, for each service related to the IP/hostname of the monitored organization.

The collected favicons are then manually checked and filtered (PROCESSING phase). This is to ensure only favicons related to a customer’s brand are actually used for pivoting, discarding favicons related to Firewalls, Control Panels and similar. In SATAYO a Setup page has been specifically developed to manage this configuration step.
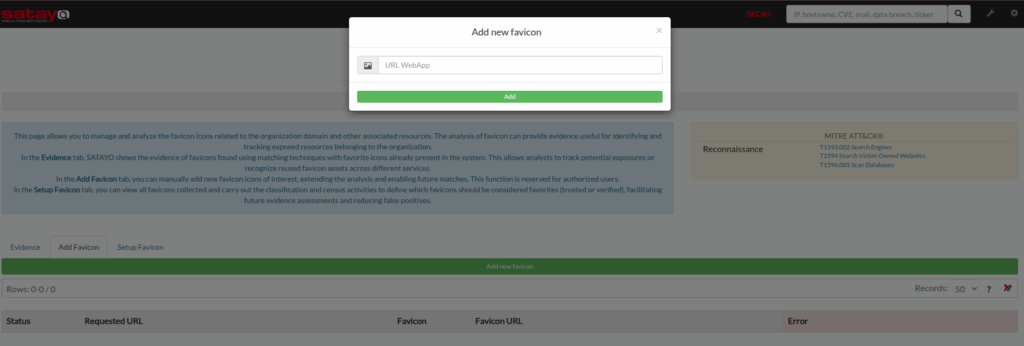
In addition to this, the SATAYO user also has the ability to upload new favicons that may be used by their organization.
From Favicon to Threat – Pivoting in Action
The next step in the favicon-related intelligence process is to pivot from the hashes calculated for a specific favicon to see if it is also used by other web services not directly managed by the monitored organization.
For this step, you can also use the third-party platforms mentioned above or a scraper you developed yourself.
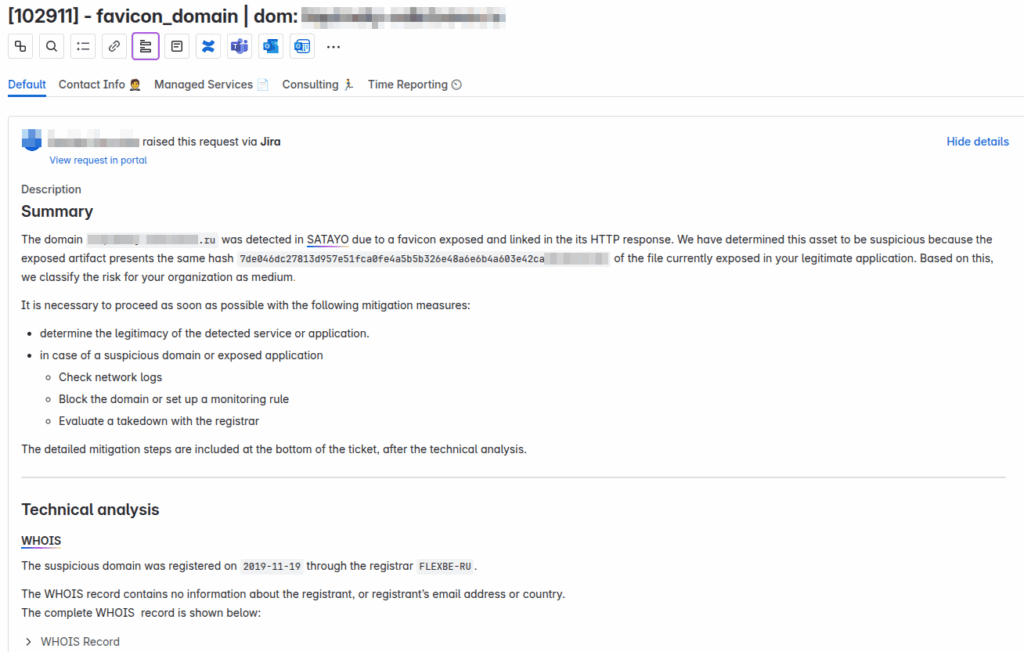
The collected, potentially suspicious favicons are then thoroughly analyzed (ANALYSIS phase) by our team of Threat Intelligence Analysts. The web service associated with the collected favicon is verified through a series of analysis steps that allow us to flag the web service as potentially malicious or a false positive.
Analysis output
The analysis results are then made available in a ticket (DISSEMINATION phase) generated from a specially developed template. The ticket’s goal is to provide evidence to our contact points within the monitored organizations, while also providing remediation activities that may also lead to the decision to initiate a resource takedown request.
While favicons may appear trivial at first glance, they serve as visual and technical anchors for brand identity online. Malicious actors often copy these elements to lend legitimacy to their campaigns—because users subconsciously trust familiar visuals.
Our favicon intelligence process enables:
- Early detection of impersonation infrastructure before weaponization
- Clustering of malicious domains that share infrastructure traits
- Attribution opportunities, especially when favicon hashes overlap with past phishing campaigns
- Enforcement and response acceleration through better prioritization
In the broader context of Threat Intelligence, favicon analysis is a powerful pivoting technique—one that complements DNS, SSL, and content-based approaches. In SATAYO, it has become a core tactic in protecting digital brand assets and mitigating abuse at scale.
By embracing this unconventional yet effective approach, organizations can stay ahead of threats, reduce the risk of brand damage, and safeguard customer trust in an increasingly deceptive digital world.







