Monitoring Windows Systems through Icinga Powershell Plugins
During migrations from NetEye 3 to NetEye 4, I often run into really outdated monitoring checks in the Windows world, where the last update was more than 10 years ago… and whose logic is therefore now completely obsolete!
The time for change is now!!!
In the last year Icinga released a really interesting project that provides a wide range of check plugins for the new Icinga 2 Agent on Windows Systems: the Icinga Powershell Plugins.
All these plugins require the Icinga PowerShell Framework as a core framework for executing checks and providing Icinga formatted output. This PowerShell module will allow plugins to fetch data from Windows hosts and use them for inventory and monitoring solutions. Together with the Icinga Web 2 module, a detailed overview of Windows infrastructure is then provided.
The available plugins in the latest release (1.5.0) will include:
- Invoke-IcingaCheckBiosSerial
- Invoke-IcingaCheckCertificate
- Invoke-IcingaCheckCheckSum
- Invoke-IcingaCheckCPU
- Invoke-IcingaCheckDirectory
- Invoke-IcingaCheckDiskHealth
- Invoke-IcingaCheckEventlog
- Invoke-IcingaCheckFirewall
- Invoke-IcingaCheckHTTPStatus
- Invoke-IcingaCheckICMP
- Invoke-IcingaCheckMemory
- Invoke-IcingaCheckMPIO
- Invoke-IcingaCheckNetworkInterface
- Invoke-IcingaCheckNLA
- Invoke-IcingaCheckPerfcounter
- Invoke-IcingaCheckProcessCount
- Invoke-IcingaCheckScheduledTask
- Invoke-IcingaCheckService
- Invoke-IcingaCheckStoragePool
- Invoke-IcingaCheckTCP
- Invoke-IcingaCheckTimeSync
- Invoke-IcingaCheckUNCPath
- Invoke-IcingaCheckUpdates
- Invoke-IcingaCheckUptime
- Invoke-IcingaCheckUsedPartitionSpace
- Invoke-IcingaCheckUsers
A basic example?
GOAL: monitoring a Windows folder: file count, size of files, and age
Before:
- We could use 2 different check plugins from Nagios world (check_file_count, check_file_age), with all the limitations about change younger than, or we could need to install
NSClient++viacheck_nrpe. - We need to create the Service Template and Command definitions under Director
Now:
- Single check with IcingaCheckDirectory
- The Command definitions can be automatically imported from a Basket provided by Icinga
Configuration on Windows Host
First of all, we need to install the icinga-powershell-plugins from PowerShell Gallery (instructions can be found at the Icinga Git project)
TIPS:
- For some checks, older versions of PowerShell not work correctly. We suggest installing/updating PowerShell 5.1 on Windows hosts. For Windows Server 2008 R2 (end-of-support) we suggest following this guide: https://www.rootusers.com/install-powershell-5-windows-server-2008-r2/
- If you have set the restriction policy on your system, please enable the RemoteSigned for LocalMachine scope.
Using the Get-IcingaCheckCommandConfig command we can export the configuration basket.
Get-IcingaCheckCommandConfig -CheckName Invoke-IcingaCheckDirectory -OutDirectory 'C:\Users\myuser\Documents\'
Configuration on NetEye Director
Now you can navigate to your Icinga Director Basket menu and import the generated file. Afterwards all specified check commands will be available and ready to use.
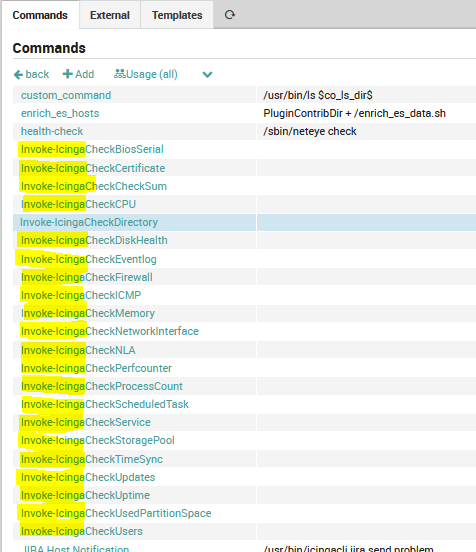
After that we can create the related Service Template and add the monitoring service on the host.
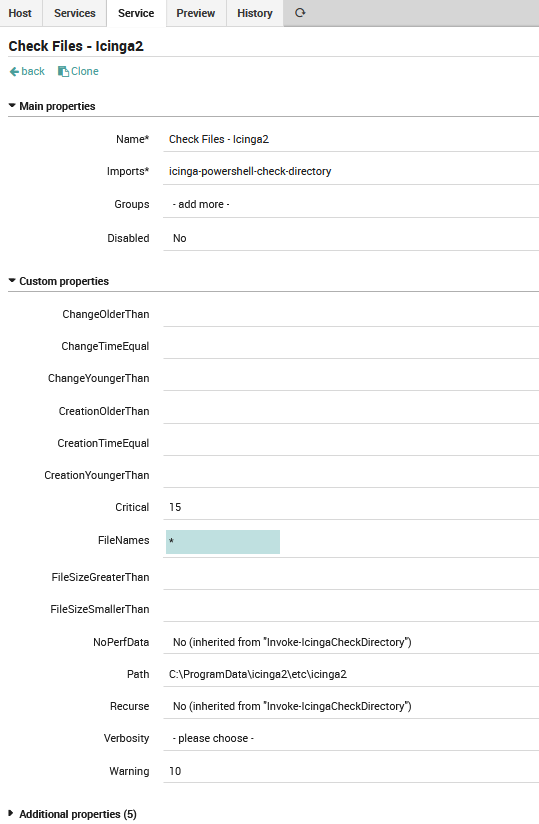
This check monitors that in a Windows folder (path) there are files (filtered by the FileNames field) that match specified criteria (size, creation, change). These checks can also be recursive on the sub-folder (with the recurse flag).
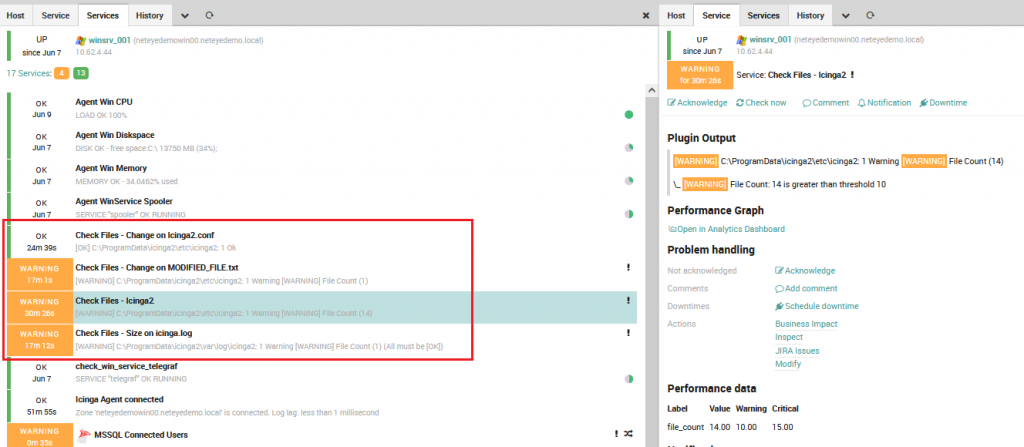
That’s all! You can add as many checks on files and directories as you want. The checks that you can do with this command are very useful, below is an example of what we implemented on our NetEye Demo Online.
References:







