
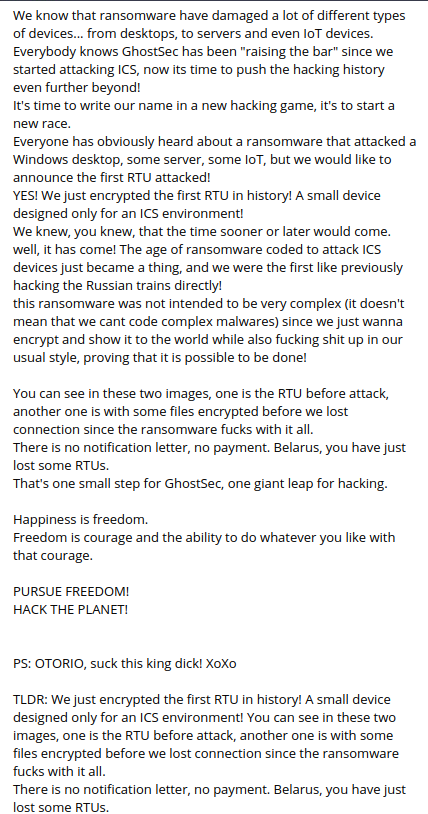
The Initial Message
The last few days have been quite hectic with regard to cyber security in the industrial systems sector. The frenzy of these days began on January 11 with this message that appeared on the Telegram channel (https://t.me/GhostSecc) of the GhostSec group:
The message was accompanied by a couple of screenshots:
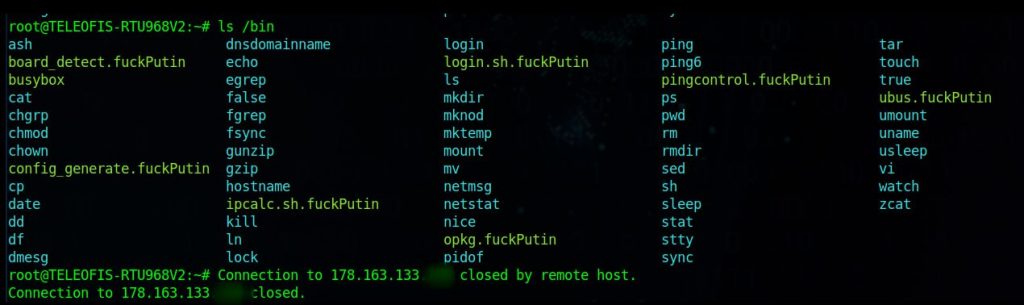
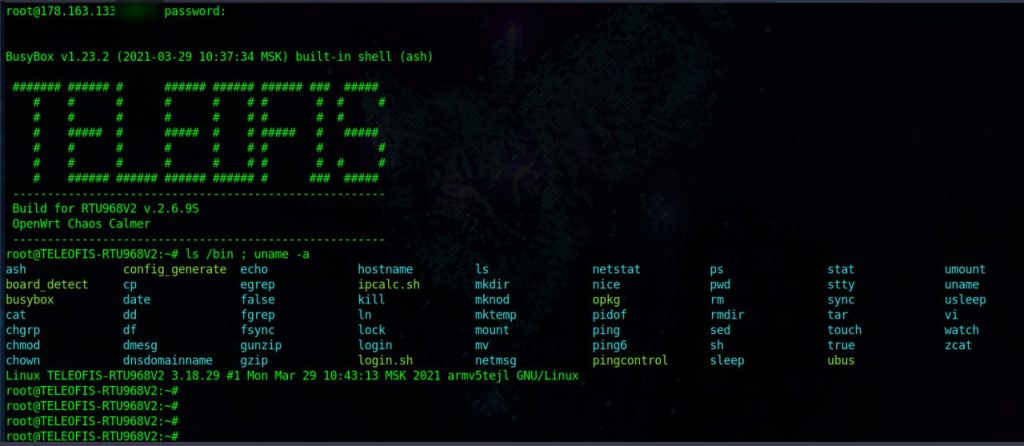
So are we really talking, as GhostSec claims, about the first ransomware-type attack against an RTU-type device? In recent days there has been plenty of discussion of this attack and there are those who have criticized the GhostSec group quite harshly, stating that it was only looking for visibility, and that the device was not a real RTU, but just a simple Linux-based modem.
Some Considerations on the OT World
First of all, let’s try to understand what an RTU is. A Remote Terminal Unit is a device used within ICS systems (Industrial Control System) and its main task is to control and acquire data from equipment present in a remote location, and then transfer this data to a central station (for example the SCADA server). If we take this definition literally, we can without any doubt say that the device attacked by the GhostSec group is absolutely an RTU.
In fact, if we check the details of the device in question directly on the manufacturer’s website (Teleofis – https://teleofis.ru/production/3g-4g-routeri/3g-router-teleofis-rtu968-v2/), we see that it is a 3G router with an integrated interface capable of translating the signal from Modbus RTU/ASCII to Modbus TCP. Another feature of the Teleofis device is the fact that it is based on the OpenWrt operating system. Another element used by those who criticized GhostSec is the fact that an RTU is a device based on a proprietary operating system (and therefore cannot be a device based on a Linux distribution).
From my point of view these criticisms are a bit of an end in themselves. The ICS world has evolved a lot over the years and the convergence between the OT (Operational Technology) and IT (Information Technology) worlds has also led to the evolution of the technologies used, and devices such as the one produced by Teleofis are increasingly widespread.
But this is not the important element of this matter. I personally don’t really care if GhostSec is the first group to actually attack an RTU device with ransomware. This is not the element that makes the difference. What does matter instead is that the interest of Threat Actors is also increasingly converging towards the OT world. And this should really be the element of interest also for those who should take care of making these environments safe.
Do we really want to start a discussion about whether or not an RTU can be based on OpenWrt or any other OS or on the fact that the typical function of an RTU must be present in a “monolithic” device and cannot be part, under certain conditions, of a different device? Would this be a discussion that could bring value to the general discourse?
Let’s Go Deep into the Substance
Since we generally wanted to dig deeper into this matter, we wanted to contact the GhostSec group to get some more information about the attack. We contacted the group through their Breached forum account. GhostSec within Breached has posted various other threads relating to the different attacks it has carried out over time.
We asked them how they handled this specific attack on Belarusian RTUs. They replied that the initial access was accomplished with a brute force attack on the SSH service (ref. Mitre Att@ck T1078) exposed by the RTU. The group also claimed to have developed ransomware specifically for this attack.
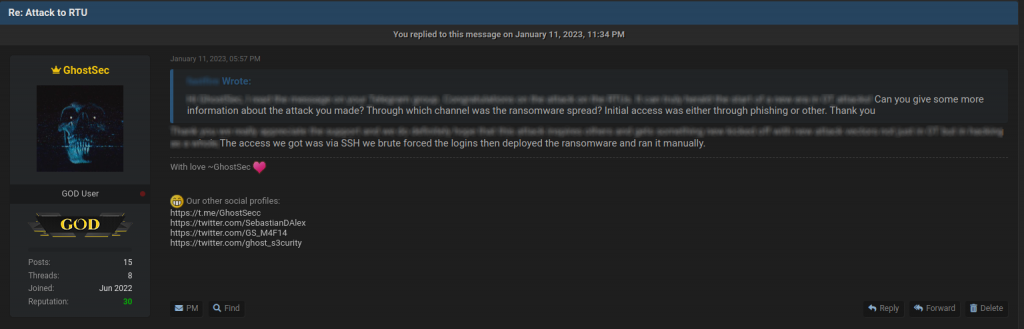
No further activities were carried out within the violated infrastructure, as the only purpose (as they indeed already reported on their Telegram channel) was purely demonstrative.
An analysis of the screenshots shared by GhostSec on the Telegram channel has also allowed us to identify one of the devices that was attacked.
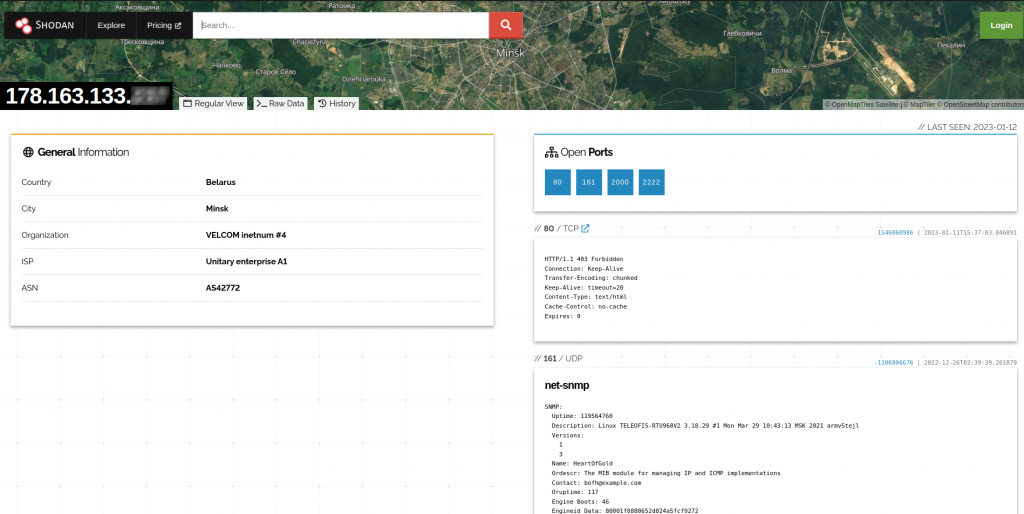
We asked the GhostSec group to share a sample of the malware used to carry out the attack. The sample was made available to us and we were able to carry out an analysis of the executable, developed in Go. The malware is very simple, it accepts a parameter as input (the key used to carry out the encryption) and encrypts the contents of the directory /bin and part of the directory /boot, effectively making the system unusable.
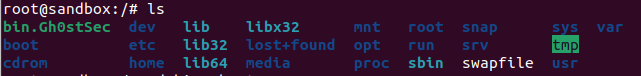
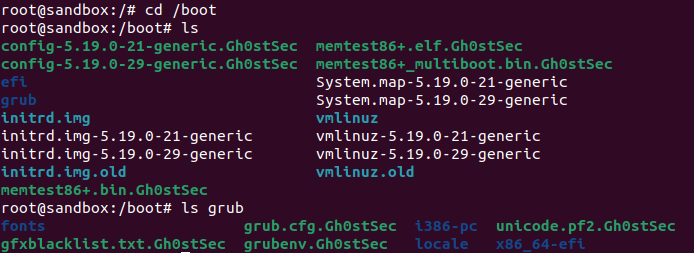
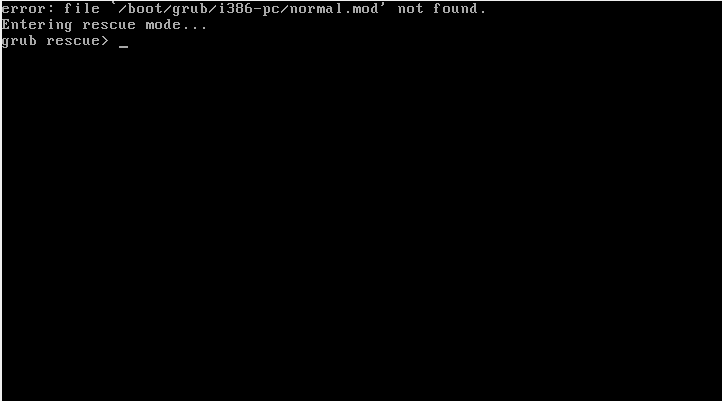
The malware performs no other actions: it doesn’t contact a command & control, it doesn’t create a note with a ransom demand and it has the sole objective of rendering the system unusable.
After this brief analysis, we had a few questions for Sebastian Dante Alexander, one of the founders of the GhostSec group, whom we contacted on Telegram.
The Interview
fastfire Q: When did you start your group? How many were you in the beginning?
Sebastian Dante Alexander A: Late 2013 is our first appearance under a different name and it originally consisted of me and someone else “Ghost3301”. uptil a point when the charlie hebdo attack happened where we became ghostsec and started hunting ISIS (2015)
fastfire Q: How many members are you now within the GhostSec group?
Sebastian Dante Alexander A: I wont answer for opsec reasons but I can say it is more than 10
fastfire Q: Which nationality or nationalities are you?
Sebastian Dante Alexander A: I dont ask my members about their nationalities we are all from mixed places around the world but we never ask nor know each others nationalities directly
fastfire Q: Ok, can you tell what nationality you are?
Sebastian Dante Alexander A: I can’t tell you for opsec reasons
fastfire Q: Why do you have this great interest in the Industrial Control System world? Did these systems meet your targets right from the start?
Sebastian Dante Alexander A: We constantly keep expanding and learning as we move forward current OT and ICS is in our sights and hopefully we will continue to learn more and understand about them better. It does meet our targets to know various different fields and to apply different styles to our attacks.
fastfire Q: What are the main targets of your attacks? Politics or business?
Sebastian Dante Alexander A: Neither. Hacking is an art to us and the attacks that we pull could have various reasons to it. Sometimes it’s for the people, sometimes it’s due to corruption, maybe drugs. But always it will be because of our passion towards hacking and the freedom that comes with doing what we do.
fastfire Q: During your attacks, apart from the specific one against Belarusian RTUs, do you normally ask the victim for a ransom?
Sebastian Dante Alexander A: We don’t normally do that it is very occasional depending on the target, and keep in mind in this case also we did not ask for money. Extortion for data or selling data happens occasionally when we see it fit but almost always what we do will be non profit and free purely for the sake of it xD
fastfire Q: Can you give an example of what you ask as a ransom?
Sebastian Dante Alexander A: We have sold data a few times on our telegram or on our breached account, but that is about it for now.
fastfire Q: Do you always use brute force attacks on ssh as during the attack in Belarus or do you also use other techniques such as Phishing, Spear Phishing, exploiting 0 day vulnerabilities, Social Engineering?
Sebastian Dante Alexander A: We have many different techniques you can search us up and see our previous attacks. Some are phishing campaigns, 0days, unpatched exploits, misconfigs, etc
fastfire Q: Which countries do you prefer to attack? What are the nations that you think are least defended from a cyber point of view at the moment?
Sebastian Dante Alexander A: 😂 there is no specific countries that we prefer to attack, though right now we noticed different countries having weak defense for example Iran,Russia and there are some countries in Europe and even some in the middle east.
fastfire Q: Are you trying to write malware also for proprietary devices of the ICS world and not just Linux-based devices? Can you give an example of this?
Sebastian Dante Alexander A: Yes though we cannot give any direct examples now but we are looking into different possibilities, meanwhile yes the target we hit for the RTU was x64 linux though another common setup is linux ARM which we are also prepared for.
fastfire Q: Have you participated in attacks together with other groups?
Sebastian Dante Alexander A: Yes.
fastfire Q: Can you give an example?
Sebastian Dante Alexander A: Would rather not disclose the details.
fastfire Ok, thanks a lot for your patience!
Conclusions
In conclusion, in the coming months we must certainly expect an important evolution in what will be the attacks that will target OT systems. As indicated by Sebastian Dante Alexander, the GhostSec group with their attack on the Belarusian targets has in fact only probed the ground using a very simple malware, but it was not their goal to build something refined at this moment. Other groups are working on this as well, and therefore this work will certainly lead to results. Let’s not be caught unprepared.
These Solutions are Engineered by Humans
Did you learn from this article? Perhaps you’re already familiar with some of the techniques above? If you find security issues interesting, maybe you could start in a cybersecurity or similar position here at Würth Phoenix.







