
0-day vulnerabilities are predicted to grow more and more, posing new threats for the cybersecurity. It’s hard to predict them and when their exploit occurs, since developers and vendors are unaware of the flaw until they are actually exploited. Hence, there is no ready patch available for a 0-day vulnerability.
MOVEit Transfer 0-day
On May 31, 2023 Progress Software published an advisory warning of an SQL injection vulnerability in the MOVEit Transfer web application that allowed remote and unauthenticated attackers to gain access to MOVEit Transfer’s database.
MOVEit Transfer is a Managed File Transfer (MFT) solution that allows Enterprises to securely transfer files between business partners and customers using SFTP, SCP, and HTTP-based uploads.
In the published advisory, remediations and security best practices are reported along with a list of IOCs (Indicators of Compromise) identified so far, which is a great help for incident response activities.
The MOVEit Transfer vulnerability became the second 0-day disclosed in an MFT solution in 2023 (the first was a 0-day affecting the GoAnywhere MFT in February 2023).
Luckily, once a new 0-day is discovered, security enthusiasts, teams and security companies invest time in researching IOCs and POCs (Proofs of Concept), reproducing the exploit and the steps of the hacking activities to gather as much data as possible about the threat actors and 0-day exploits.
To date, the exploit for the MOVEit Transfer vulnerability has been made available to the community by sfewer-r7 and horizon3ai on GitHub as well as a detection rule to uncover the exploitation by looking for files created with unexpected extensions in the root folder (“C:\MOVEit Transfer\wwwroot\“) of the MOVEit Transfer service.
Related to the MOVEit Transfer hacking campaign, Curated Intelligence maintains a repository for tracking events and new breakthroughs, representing a valuable source of information to learn about this vulnerability that was assigned as CVE-2023-34362 on June 2, 2023. On the same date, the Microsoft Threat Intelligence team attributed attacks exploiting the MOVEit Transfer vulnerability to the ransomware gang called CL0P (aka Lace Tempest, FIN11 and TA505).
One of the reasons for this attribution is the use of similar vulnerabilities in the past to steal data and extort victims (CL0P was responsible for data-theft attacks using a GoAnywhere MFT 0-day in January 2023 and a 0-day affecting Accellion FTA servers in 2020). The confirmation arrived when the CL0P ransomware gang claims responsibility for the MOVEit extortion attacks, having stolen data from hundreds of companies that will be published starting from June 14, 2023 if a ransom is not paid.
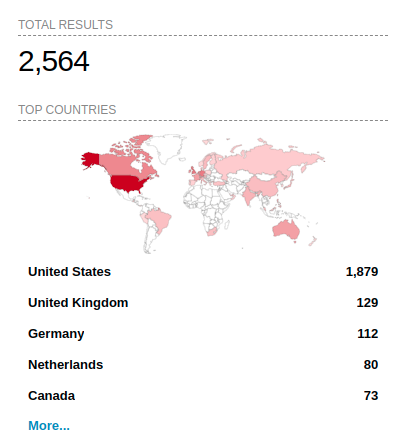
According to Shodan, there are over 2,500 exposed MOVEit Transfer servers on the Internet, most located in the US.
CL0P claims to have begun the attacks on May 27, 2023 during the US Memorial Day holiday, a common tactic that has also been used in the past by the ransomware gang. On holidays, few people are at work, so the attack has a greater chance to be successful and to go unnoticed.
However, threat intelligence by several companies indicated that the MOVEit Transfer 0-day was exploited further back than initially thought (i.e., before May 27, 2023):
Conclusion
Progress Software has released a patch for the MOVEit Transfer vulnerability. Even though updating to a fixed version will help protect against future exploitation, it’s not enough to address potential threat actor access to systems that have already been compromised. Hence, regardless of whether any IOCs are found, customers should perform emergency incident response activities to remove any access or backdoors created in a previous exploitation.
0-day exploits have a significant impact on companies, employees and customers. We as the Cybersecurity team of Würth Phoenix always monitor and keep up-to-date with new vulnerabilities and cybersecurity topics, developing and integrating new detection rules in our SOC to keep our customers safe.
“One single vulnerability is all an attacker needs”
Window Snyder
These Solutions are Engineered by Humans
Did you learn from this article? Perhaps you’re already familiar with some of the techniques above? If you find security issues interesting, maybe you could start in a cybersecurity position here at Würth Phoenix.







