NetEye 4.24 Release Notes
Welcome to version 4.24 of our NetEye v4 Unified Monitoring Solution.
In this release, NetEye hiked over the Seceda mountain, placed in Val Gardena/Grödental, to admire a wonderful view of the Fermeda pinnacles at sunrise. The Fermeda pinnacles, the southernmost ridge of the Odle group, offers an ideal environment to climbers, especially for ascents on the southern sides, thanks to good solid rocks and intermediate level climbing routes.
General
Request Header Authentication
In corporate environments, Single Sign On (SSO) is rapidly becoming a standard requirement for, modern centrally managed security policies. With SSO, users have fewer credentials to manage, and corporate policies, such as MFA or strong password requirements, can be managed in few or even one central points for an entire company.
In this release a new authentication backend, the Request Header Authentication, was added to NetEye. With this backend, users can be logged into NetEye by passing their traffic through external authentication providers and securely forwarding information about the user to be authenticated to NetEye.
Each external authentication backend must enrich the HTTP requests of the user to be authenticated with an HTTP header containing information about the user to be logged in. To ensure the authenticity of this data, each external authentication backend is required to present a client certificate to NetEye, which must be signed by one of the Certificate Authorities trusted by Apache on NetEye. For more information about the new authentication backend, please refer to the dedicated section in the NetEye User Guide.
User Guide
Setting up a NetEye cluster, or any multi node environment, can be a quite complex topic. In order to make the installation procedure more understandable, and easier to follow, we rewrote the User Guide section about cluster installation documentation and system requirements.
ISO EFI support
Starting from NetEye 4.24 all available ISO images will fully support EFI boot when installing NetEye Nodes.
Monitoring – Detection
VMD
NetEye is used to monitor very large VMware environments. For these needs we ship the VMD module, upgraded to version 1.4 in this NetEye release. This important upgrade introduces two new and very interesting features: Monitoring and ITOA integrations.
Monitoring Integration
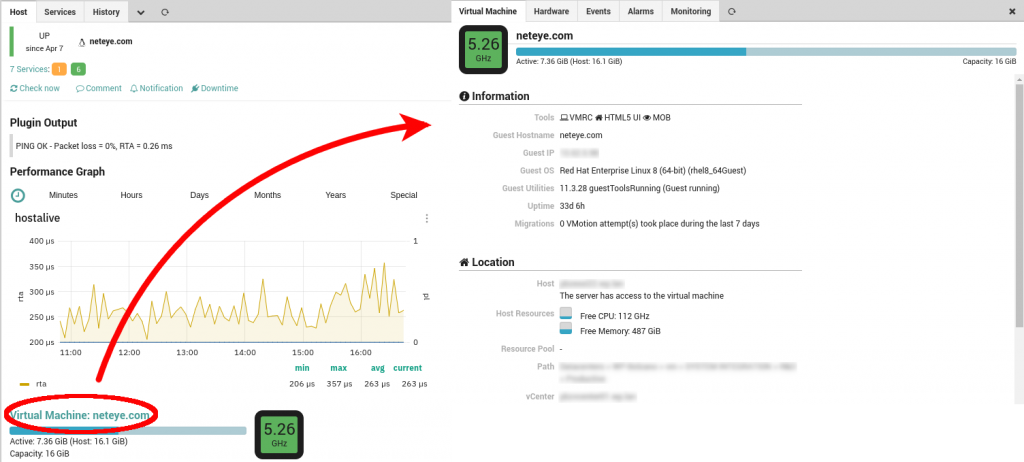
Whenever a monitored VMware host or VM is experiencing an incident, we need to take action as fast as possible. The NetEye VMD module exposes real time data about VMware objects, which helps to find the root cause and lead to a possible solution. Navigating from an object in the Monitoring module to the VMD module and, once there, identifying and opening the same object is time-consuming and a possible source for human error. To avoid these shortcomings, we developed the VMD monitoring integration.
Now every monitored VMware host or VM can display a summary of its current state directly in the Monitoring module, it includes the amount of used CPU and file system along with a link to jump directly to its details in the VMD module. The Monitoring feature needs to be enabled manually: the procedure can be found in the NetEye User Guide.
ITOA Integration
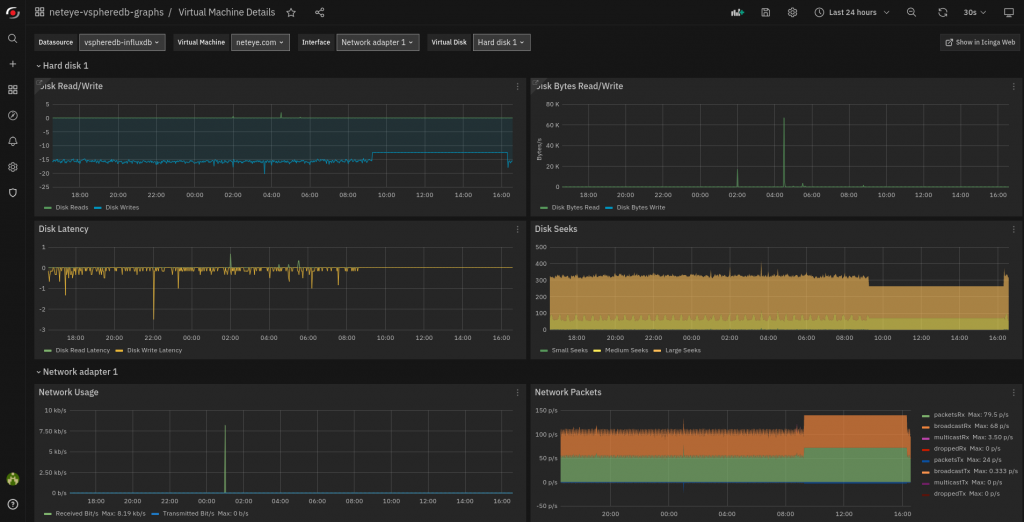
Having an overview of the VMware environment performance can be priceless when trying to understand if everything is working properly or if some action is required. For this purpose, the ITOA module provides two brand-new Grafana dashboards out-of-the-box based on the data collected by VMD. Indeed, the VMD module now tracks performance counters from VMware and stores them in InfluxDB. The new Grafana Dashboards are then generated based on the history of the VMD live data. As this feature can be quite data-heavy, it needs to be enabled manually for each individual VMware environment you want to analyze. To learn more, you can refer to the section in the NetEye User Guide.
Service Management – Incident Response
Command Orchestrator UI
Users of the CMDO module are often required to make quick decisions and react to time-critical situations. This kind of work requires that the UI can be used with confidence, eliminating any possible doubts and minimizing chances for human error. To reach this goal, we have improved the UX for the Command Orchestrator in this release.
From now on, comments can be added to both commands and command parameters, in addition to the already present description for command groups.
Larger sets of command groups can now be navigated more easily, as the full path to each command group is prominently listed in the first column. Additionally, groups now are sorted by default based on their full path. Furthermore, when searching for a group, now also the children of matching command groups will be listed.
Personalized labels for command parameters, allow you to separate the underlying technical implementation of a command from the parameter names displayed to the user. They make it possible to overwrite the text displayed next to each parameter when running commands.
SIEM – Log Management
Improved Elastic Stack configuration management
Squeezing the last bit of performance out of the Elastic Stack components requires a tailor made solution for each specific environment and its particular use cases. Accordingly, NetEye allows the customization of the more generic default configuration, and render them easy to manage and maintain.
Therefore, in release 4.24, NetEye brings the following enhancements to the configuration management of Elastic Stack components:
- Persistent, targeted override of the Elasticsearch JVM options via
jvm.options.ddirectory - Persistent customization of the files composing default Logstash pipelines
- Ability to disable the Filebeat NetFlow module
All customizations follow now the standard for handling diverging configuration by generating .rpmnew and .rpmsave files whenever the default settings are subject to changes.
References
Should you be interested to discover more about NetEye feel free to explore our Online User Guide.







