Hacker Group Activities and Cyber Security Concerns | Second Semester 2023
A Security Operation Center (SOC) is a service where the customer is an active participant. Establishing a good relationship with the customer is an important requirement for handling security incidents more efficiently. Our SOC analysts produce and deliver several reports, most of them on a monthly basis. They are usually presented to clients during a monthly meeting, where we discuss information about the operations performed by our SOC, such as alerts and tickets handled, new detection rules implemented, and more.
Within the primary SOC report, there is a focus on cyber security concerns, with a list of ransomware attacks carried out, a list of new zero-day vulnerabilities, general vulnerability trends, security bulletins and news. In this blog post I’ll summarize these items to give you some insight into some of the most relevant activities that took place in the cyber landscape in the second half of this year.
July 2023
Citrix Systems announced in mid-July a security bulletin concerning three vulnerabilities affecting two of their products: CitrixADC and CitrixGateway. The critical vulnerability CVE-2023-3519 is already being exploited by threat actors, allowing them to drop a webshell on infected hosts in order to collect and exfiltrate the contents of the victim’s Active Directory (AD). There are thousands of vulnerable devices connected to the Internet and it’s recommended to patch them as soon as possible. Our SOC produced an informative report about the vulnerability, including analysis on the attack surface and what to do in the event of an attack.
Ivanti’s Endpoint Manager Mobile (EPMM) was targeted by threat actors who exploited highly critical bugs to bypass the authentication controls of administrative users and, without the use of credentials, gain access to a large amount of sensitive information on publicly exposed EPMM servers. The exploited vulnerabilities are CVE-2023-35078 and CVE-2023-35081.

These flaws have been the focus of media attention as hundreds of large organizations, including government agencies and critical infrastructures, make use of EPMM. Our SOC produced an informative report about these vulnerability as well. The report includes a POC of the exploit and the list of IOCs involved in the malicious activity.
August 2023
LinkedIn accounts were massively targeted during this month, resulting in several accounts being blocked for security reasons and others being hijacked by attackers. Threat actors began exploiting leaked or stolen credentials and brute forcing attempts to gain access to LinkedIn members’ accounts. Affected users have tried to recover their accounts by contacting LinkedIn support, but with little success.
Customer service was then overwhelmed by the high volume of support requests and didn’t respond for weeks, with the result that people became increasingly frustrated because they didn’t receive any help. We recommended that all LinkedIn users change their password to a strong one and activate 2FA to avoid being easily compromised.

Anonfiles, an anonymous file-sharing site that allows people to share files anonymously, was shut down by its owners. The idea behind the website was to safeguard users’ privacy, which is why it became one of the most popular file-sharing services used by threat actors.
A massive amount of abusive material was uploaded to the site every day, from stolen credentials to copyrighted files. The site was also injected with a script used to distribute malware. The files downloaded from Anonfiles actually came from other shady websites, and users ended up installing various malware, including multiple log stealers.
September 2023
Researchers from the cybersecurity firm Mandiant observed an increasing number of attacks using infected USB drives to steal confidential information. At the root of these attacks was the Chinese UNC53 group, which managed to hack at least 29 organizations worldwide since the beginning of the year. According to Mandiant, most of the infections occured in African countries, including Egypt, Zimbabwe, Tanzania, Kenya, Ghana and Madagascar. The virus, known as Sogu, was in some cases spread via public computers in Internet cafes and print shops. USB sticks as a malware vehicle was thought to be a thing of the past, but this method proved surprisingly effective, especially in developing countries where these sticks are still widely used.
The Sogu USB malware uses a number of simple but clever tricks to infect machines and steal their data. It’s able to infect air-gapped computers that don’t have an Internet connection. Once installed on a system, the malware establishes a connection to a remote server, where stolen data is sent. The method allows criminal hackers to create a vast network of infected systems from which to select the most valuable victims. Researchers noted that the hackers must have a good number of human resources to process the stolen information, which suggests that the organization behind the Sogu malware is large and well-defined.
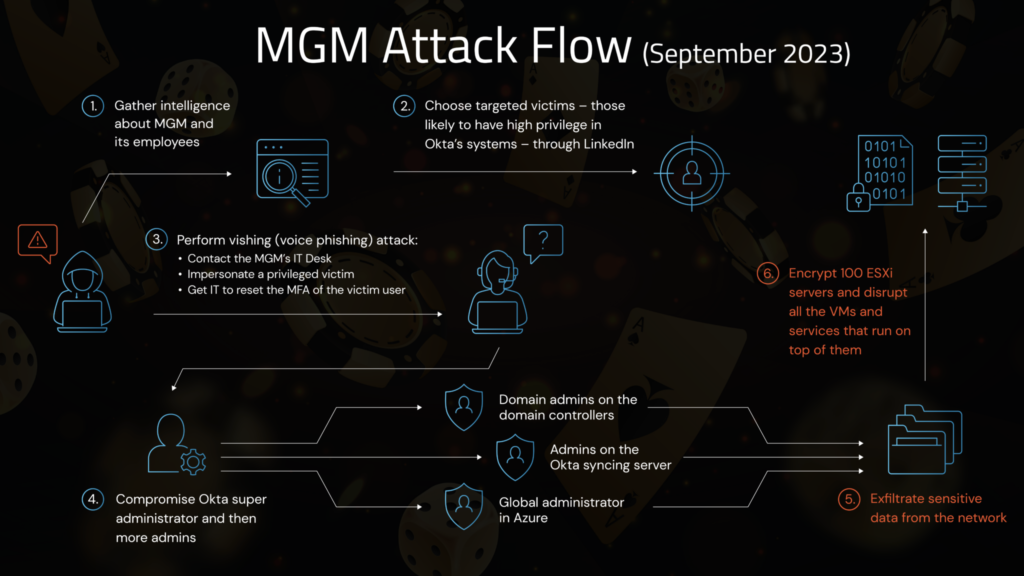
MGM Resorts International, a US entertainment company that owns more than two dozen hotels, resorts and casinos, was attacked in mid-September and many of its systems were disabled for several days. The criminal gang behind the attack is believed to be Scattered Spider. The threat actors began with a social engineering attack, impersonating an employee who had lost his credentials and calling MGM’s IT help desk to regain access. The attackers gained access to Okta, the identity and access management, and the Azure cloud environment. They exfiltrated terabytes of data and then deployed the BlackCat/ALPHV ransomware, encrypting several hundred of MGM’s ESXi servers. At this point all services were out of order, hotel room keys no longer worked, dinner reservation systems were down, point-of-sale systems were unable to accept payments, guests could not check in or check out, and slot machines were completely unavailable, causing losses of millions of euros per day.
October 2023
On 10 October 2023, Google Cloud, Amazon AWS and Cloudflare mitigated the largest Distributed Denial of Service (DDoS) attack in history. The attack peaked at 398 million requests per second (rps), 7.5 times larger than the previous record of ‘only’ 46 million reached by a DDoS attack last year. To give you an idea of the size, the attack (which lasted only two minutes) generated more requests than the total number of article views reported by Wikipedia during the entire month of September 2023.
Such a massive attack was possible thanks to the exploitation of a vulnerability on the HTTP/2 protocol, used to generate hypervolumetric DDoS attacks. The attack was named HTTP/2 Rapid Reset and the vulnerability exploited was identified as CVE-2023-44487, which was classified as high severity, receiving a CVSS score of 7.5 out of 10. A report on this vulnerability was made available to our SOC customers.
On Monday, October 16, 2023 Cisco reported that a critical zero-day vulnerability had been exploited to create backdoors in devices running Cisco IOS XE software exposed over the Internet. This vulnerability, tracked with the ID CVE-2023-20198 and classified as critical with a CVSS score of 10/10, allows an unauthenticated remote attacker to create an account with elevated privileges on the vulnerable system and use it to take control of it.
The vulnerability affected both physical and virtual devices with the HTTP or HTTPS web interface enabled. Some verification activities of the potential attack surface identified about 30,000 devices that have already been successfully attacked. A report on this vulnerability was made available to our SOC customers, along with a IOC list.
November 2023
The CL0P ransomware gang struck again, exploiting a zero-day vulnerability targeting SysAid, an IT service management company. The zero-day, identified as CVE-2023-47246, is a path traversal used by attackers to load a malicious webshell and execute malicious code. The vulnerability resides in the company’s management software to access corporate servers.
The company released an updated version (23.3.36), which includes a patch that renders the attack ineffective. All customers are strongly advised to install the update. CL0P frequently exploits new zero-day vulnerabilities to carry out its attacks. Some of these attacks, such as the MOVEit attack in May, have already been covered in our previous post.
Okta, an American identity and access management company, was the victim of an attack. The security incident affected the customer support management system (Okta Help Center) and allowed threat actors to download a report containing the data of all users of Okta’s customer support system. Fortunately, the report does not include user credentials or sensitive personal data, but can be used to target Okta’s customers through phishing or social engineering attacks.
Okta stated that the most likely route for the attackers to expose credentials was to compromise the employee’s personal Google account or personal device. It would thus appear that an Okta employee logged in with his personal Google account to the company PC, synchronized the saved password with Google, and then ended up installing a stealer on his personal device that exfiltrated all credentials. Considering this, it’s vital to monitor the presence of compromised accounts for sale on darknet marketplaces to reduce the attack surface. Our SATAYO product monitors credentials stolen by malware stealers on a daily basis, to help you identify potential security exposures in time.
December 2023
On December 19th, the US Department of Justice announced a disruption campaign against the ALPHV/Blackcat ransomware group, seizing the gang’s onion website.
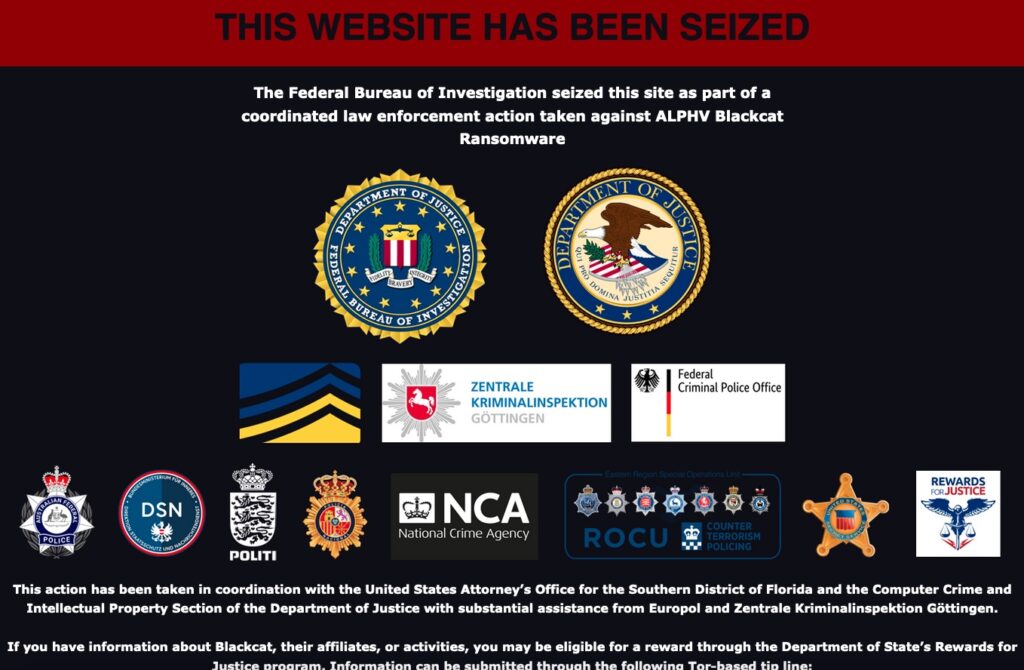
The FBI also managed to steal decryption keys that allowed 500 affected victims to restore their systems and save $68 million in ransom demands.
Law enforcement was able to identify and collect 946 public/private key pairs from ALPHV/Blackcat that the ransomware group used to operate its various onion services, including affiliate boards, leak sites, and victim communications sites.
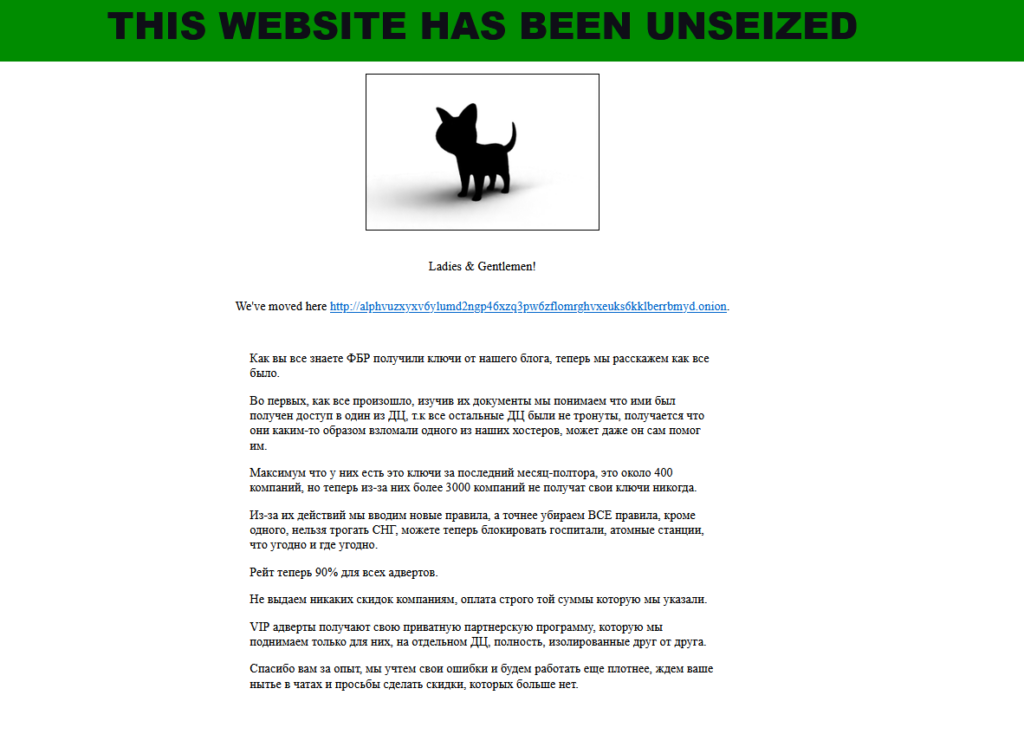
However, ALPHV members were able to publish an update on the onion page, claiming to have taken back the control of the site. They didn’t actually regain access to the seized infrastructure, but both the ransomware group and the FBI were in possession of the private key to control these services.
Using these keys, the gang was able to create a new site using the same .onion address with a new server. Onion sites work differently from normal sites, and whoever makes the most recent changes to the underlying configuration will be able to display the most recent message. This triggered a fight for the latest update between the gang and the FBI.
In the message, the ALPHV/Blackcat group informs everyone that they are removing restrictions on ransomware, allowing affiliates to attack even sensitive targets such as hospitals and nuclear power plants. They have also increased the fee given to partners in an attempt to keep their affiliates and convince them to stay with them rather than switch to competitors like Lockbit.
These Solutions are Engineered by Humans
Did you learn from this article? Perhaps you’re already familiar with some of the problems above? If you find cybersecurity issues interesting, maybe you could start in a cybersecurity or similar position here at Würth Phoenix.







