Hacker Group Activities and Cyber Security Concerns | First Semester 2023
A Security Operation Center (SOC) is a service where the customer is an active participant. Establishing a good relationship with the customer is an important requirement for handling security incidents more efficiently. Our SOC analysts produce and deliver several reports, most of them on a monthly basis. They are usually presented to clients during a monthly meeting, where information about the operations performed by our SOC is discussed, such as alerts and tickets handled, new detection rules implemented, and more. Within the primary SOC report there is a focus on cyber security concerns, with a list of ransomware attacks carried out, a list of new zero-day vulnerabilities, general vulnerability trends, security bulletins and news. In this blog post I’ll summarize these items to give you some insight into some of the most relevant activities that took place in the cyber landscape in the first half of this year.
January 2023
Security software company Avast released a free decryptor for the Bianlian ransomware. BianLian is a relatively new group that emerged in August 2022. Their ransomware, written in Go, has been decrypted thanks to the binaries left behind. Avast has released a decryptor that can help victims recover their files if they were encrypted with a known version of the ransomware. Of course, those hackers are now using a new version of the malware that researchers have not yet identified.
Also in January the notorious ransomware group Hive was taken down by the FBI. Federal agents ‘hacked the hackers’ by gaining access to their network last July. They recovered hundreds of encryption keys and helped victims unlock their data without paying ransom to Hive. An estimated $130 million was saved. After several months of work with German and Dutch officials, the FBI shut down Hive’s servers and websites at the end of January.

ESET researchers also uncovered an espionage campaign run by the StrongPity group targeting Android users. They exploited a modified version of Telegram with injected Trojans, tricking users into downloading it by passing it off as an official version of Shangle (a platform for random video chats). After installation, the app functions as a backdoor, allowing criminals to collect SMS messages, record voice calls, read notifications and exfiltrate communications.
February 2023
A threat group called SiegedSec announced that they had hacked into the software of Atlassian and exfiltrated sensitive data. The group leaked the company’s floor plans and information on about 13,000 employees. SiegedSec is a group of hacktivists and doesn’t try to sell stolen data or make a profit from it. After several investigations, Atlassian confirmed that the valid credentials used by the hackers to access the systems were obtained from a public repository which they had mistakenly been posted to.
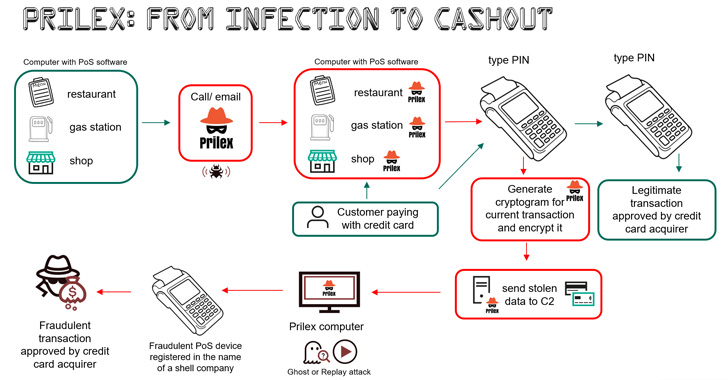
Prilex is a well-known threat actor that has gradually changed its attack methods from malware targeting Automated Teller Machines (ATMs) to modular malware for Point of Sale terminals (POS). Kaspersky researchers have discovered three new variants of Prilex malware capable of blocking contactless near-field communication (NFC) transactions on infected devices in order to steal money. The goal of these malicious actors is to force the victim to use their physical card by inserting it into the PIN pad reader, so that the malware can capture data from the transaction.
During the month of February some vulnerabilities present in VMware ESXi were exploited by a ransomware gang who attacked thousands of systems worldwide with the ESXIArgs ransomware. Our SOC produced an informative report about the situation that was made available under the “Informative Report” section in each customer’s Confluence space.
March 2023
The ransomware group CLOP announced in February that it had managed to steal the data of more than 130 companies by exploiting a zero-day vulnerability in Fortra’s GoAnywhere MFT secure file sharing solution (CVE-2023-0669). CLOP’s claims could not be confirmed at the time, but they appear to be true because the gang added 98 companies to its Tor leak website this month. Fortra released an emergency patch in software version 7.1.2, but many companies did not update their systems in time and suffered breaches.
The Russian hacktivist group NoName057(16) has been conducting multiple DDoS attacks against NATO countries. In March, many Italian websites were targeted, including those of the government, the Chamber of Deputies, the Ministries of Defense, Foreign Affairs and Transport, the Transport Regulatory Authority of Milan and Rome, and Bologna Airport. Other countries targeted were Estonia, Lithuania, Norway, Poland and Finland, and the list goes on. Having protection against volumetric attacks or a WAF (Web Application Firewall) helps prevent and limit the impact of these DDoS attacks.

ChatGPT, arguably today’s most popular user-facing Al system, has been at the center of a phishing campaign targeting its users. Scammers began sending fake e-mails about an OpenAl token which doesn’t actually exist. The phishing e-mail copies the standard format used by OpenAl for official emails, and induces users to click on a malicious link that redirects them to a fake version of the ChatGPT website. The scammers’ goal was to steal the cryptocurrency wallets of users who had clicked on the link. Twitter was also used as an attack vector, with scam accounts promoting the OpenAl token.
The 3CX Desktop App was compromised by threat actors, who were able to deliver a trojanized version using the company’s official channels. The attack begins when the MSI installer is downloaded from 3CX’s website or when an update is sent to an existing desktop application. The attack was named Smooth Operator and included hands-on keyboard activities and info stealing behaviors on infected systems. This situation can cause serious harm to the affected organizations and put their data and privacy at risk.
April 2023
Genesis Market, one of the most notorious marketplaces for stolen credentials, was seized by the FBI earlier this month. The operation, dubbed Operation Cookie Monster, led to numerous arrests globally. There are other marketplaces, such as Russian and 2Easy, that are actively monitored by our CTI platform SATAYO, but Genesis’ unique feature was that it offered its customers “fresh” access to the victim’s machine at all times, as the installed malware stealer was constantly sending new data. It was also possible, with a custom plugin developed by Genesis, to emulate the victim’s session and access restricted pages without having to enter any credentials.
Rorschach is the name of a new sophisticated ransomware that was detected by Checkpoint researchers. This ransomware doesn’t have any branding and contains unique features rarely observed in other ransomware. It employs a highly effective cryptography scheme, making it one of the fastest ransomware binaries observed. Rorschach appears to have taken some of the “best” features from some of the leading ransomware leaked online, and integrated them all together. The operators behind it remain unknown.

The cybercrime group FIN7 is suspected of attacks against internet-facing servers running Veeam Backup & Replication software. The malicious code was found to be POWERTRASH, an obfuscated loader written in PowerShell used to execute different scripts attributed to FIN7 in the past. The group exploited the vulnerability CVE-2023-27532 to obtain initial access to the machine and execute the malicious payload. The attack was mitigated by WithSecure EDR before it fully materialized, so no damage was done, but the purpose of the attack remains unclear.
May 2023
Netcraft, an internet services company based in the United Kingdom, keeps a list of the top 50 TLDs with the highest cybercrime-incidents-to-active-sites ratio. Netcraft explores the internet every month, sending an HTTP request to each site and determining their activity levels. The complete results are available at the link https://trends.netcraft.com/cybercrime/tids, and according to the list the domain which is most often used for illicit activities is cyou.
The ransomware group CLOP took responsibility for a massive zero-day attack used to steal data from several organizations. This is the same CLOP from the March report above, where it was the protagonist of a large-scale attack exploiting the zero-day vulnerability in the Fortra GoAnywhere MFT that affected 130 major companies worldwide. This time they are behind a mass exploitation of another zero-day (CVE-2023-34362) affecting another file transfer software, MOVEit Transfer. The attack on the service is believed to have started on May 27, during the long Memorial Day holiday in the United States, when there were fewer staff engaged in monitoring systems than usual.
The flaw is a SQL injection vulnerability that leads to remote code execution (RCE). The attackers placed a web shell on the infected machines that allowed them to extract a list of files stored on the servers, steal the credentials and settings for the configured Azure Blob storage containers, and download files from the server. On its darknet site CLOP published the instructions that companies should follow to avoid publication of their data.
In early May, Google Registry, an organization that maintains administrative data for one or more top-level or lower-level domains, launched eight new TLDs (Top Level Domains). Google Registry works with several domain registrars (such as Google Domains, GoDaddy, Namecheap and many others) that allow users to register a domain. It’s normal for Google to release new TLDs, but unlike previous times, security researchers raised concerns about the potential dangers of two TLDs in particular: .zip and .mov. The risks associated with these domain names were covered in a previous blog post, if you’re interested check it out!
June 2023
The pro-Russian hacker group Killnet, together with REvil and Anonymous Sudan, announced plans for a destructive cyber attack against European banks and financial system in general. Killnet is known for its powerful distributed denial of service (DDoS) attacks that have targeted several European countries and companies in recent months. The European Investment Bank (EIB) confirmed on June 19th an outage of its two main websites, which was attributable to the previously announced cyberattack. Apart from the availability issues caused by the DDOS, no other damaging action took place. The European Banking System wasn’t affected at all.



Threat actor Blacktail is behind the Buhti ransomware, first detected in February 2023 by Palo Alto, which targets both Windows and Linux devices. This ransowmare is a repurposed version of the LockBit and Babuk code, leaked in recent years by disgruntled employees. It exploits critical CVEs to penetrate into vulnerable devices and encrypts files adding the .buhti extension. The Buhti ransomware operation is a perfect example of how easy it is for aspiring criminals to get into the action using publicly available and effective malware tools, and cause significant damage.
A threat actor with the username Spyboy is selling in a Russian hacking forum a program called Terminator that claims to be an AV/EDR/XDR killer. This program is supposed to be able of terminating 24 different endpoint protection software systems, such as Windows Defender, Kaspersky, Cortex, TrendMicro and many others. Spyboy sells this software at prices ranging from $300 for a single bypass, to $3,000 for a complete bypass.
The Terminator tool exploits legitimate but vulnerable Windows drivers belonging to the Zemana anti-malware tool to execute arbitrary code in the Windows kernel. The exploitation of vulnerable drivers to achieve privileged code execution is called a BYOVD (Bring Your Own Vulnerable Driver) attack. In this type of attack, legitimate drivers signed with valid certificates and capable of running with kernel privileges are installed onto victim devices to disable security solutions and take control of the system.
An attempt to emulate the malware was made by user ZeroMemoryEx on Github, who published a program that mimics Spyboy’s Terminator function. This is not the first time attackers have leveraged BYOVD attacks. Just a couple of months ago, ransomware gangs used the AuKill malware to disable Endpoint Detection & Response (EDR) software on target systems before deploying backdoors and ransomware. The attack mechanism is similar to Terminator: a vulnerable driver is inserted into the system and disables the security software through kernel-level commands.
Several versions of Aukill have been observed in the wild since the beginning of the year. The advantage of having an SOC (Security Operation Center) is that behavior like that mentioned above is detectable within the logs collected via sysmon from the monitored hosts.
These Solutions are Engineered by Humans
Did you learn from this article? Perhaps you’re already familiar with some of the techniques above? If you find security issues interesting, maybe you could start in a cybersecurity or similar position here at Würth Phoenix.







