In this second post on the Exposure Assessment topic we’ll start from the end!
We’ve just put into production, within our OSINT & Cyber Threat Intelligence SATAYO platform, an internal search engine that aims to simplify the search for evidence within the platform itself. This is a development that has been particularly requested by those organizations which are monitored within the platform and which manage a large number of internet domains.
SATAYO aims to search for information relating to an organization, within the Surface, Deep & Dark Web, starting from these input elements: the organization’s internet domains and some keywords (typically names of services and products, names of top management figures in the organization, and so on).
The phrase that best describes the goal of our platform is:
Discover the attack surface, keep it monitored, and manage the exposed data over time. React proactively in order to avoid exploits.
These are some of the objects that the SATAYO platform allows you to discover:
- host names
- IP addresses
- details of the IP blocks available to the organization
- email accounts
- similar domains
- related domains
- top-level domains
- vulnerabilities
- exposed web services
- active HTTP methods
- presence of IP and host names within the blacklists
- presence of evidence within paste-like sites
- correct configuration of mail servers
- correct configuration of SSL / TLS
- evidence in hacking forums
- evidence in Telegram channels
- evidence in WhatsApp groups
- evidence in various social networks
- evidence in ransomware gang sites
- evidence in Bug Bounty portals
- presence of compromised credentials (within an ever-expanding database of over 27 billion accounts!)
- presence of hard-coded credentials in GitHub projects
- exposure of interesting metadata in files indexed by search engines
- and so on!
Surely this allows us to recover, for any domain, an impressive amount of information!
So we decided to simplify the activities of those who, within an SOC (Security Operation Center) or directly within individual organizations, have the goal of implementing the mitigations or remedies that are suggested within SATAYO.
As mentioned at the beginning of this post we have developed an internal search engine, which allows at this time to search through, within all the evidence discovered by SATAYO for all the domains of an organization, for the following elements: IP address, host name, email account, CVE (Common Vulnerabilities and Exposures), and name of a data breach.
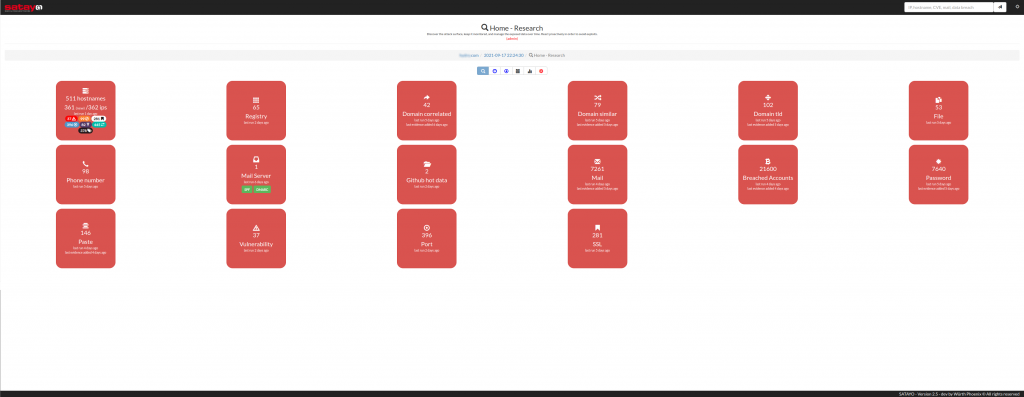
The search bar has been positioned at the top right and suggests searchable items.
For example, if you want to check if any of the services exposed by your organization have a specific vulnerability, you can search for the specific CVE (in the format CVE-yyyy-xxxxx). In fact, it may be worth just knowing the remote vulnerabilities most exploited by cyber attackers in recent months (source: https://us-cert.cisa.gov/ncas/alerts/aa21-209a):
| Vendor | CVE | Type |
|---|---|---|
| Citrix | CVE-2019-19781 | arbitrary code execution |
| Pulse | CVE 2019-11510 | arbitrary file reading |
| Fortinet | CVE 2018-13379 | path traversal |
| F5- Big IP | CVE 2020-5902 | remote code execution (RCE) |
| MobileIron | CVE 2020-15505 | RCE |
| Microsoft | CVE-2017-11882 | RCE |
| Atlassian | CVE-2019-11580 | RCE |
| Drupal | CVE-2018-7600 | RCE |
| Telerik | CVE 2019-18935 | RCE |
| Microsoft | CVE-2019-0604 | RCE |
| Microsoft | CVE-2020-0787 | elevation of privilege |
| Microsoft | CVE-2020-1472 | elevation of privilege |
If, on the other hand, you want to know whether any of the email accounts in your organization are exposed within a specific data breach, simply type the name of the same in the search box. Here you can see an example of a search for a famous data breach, that of the Canva service:
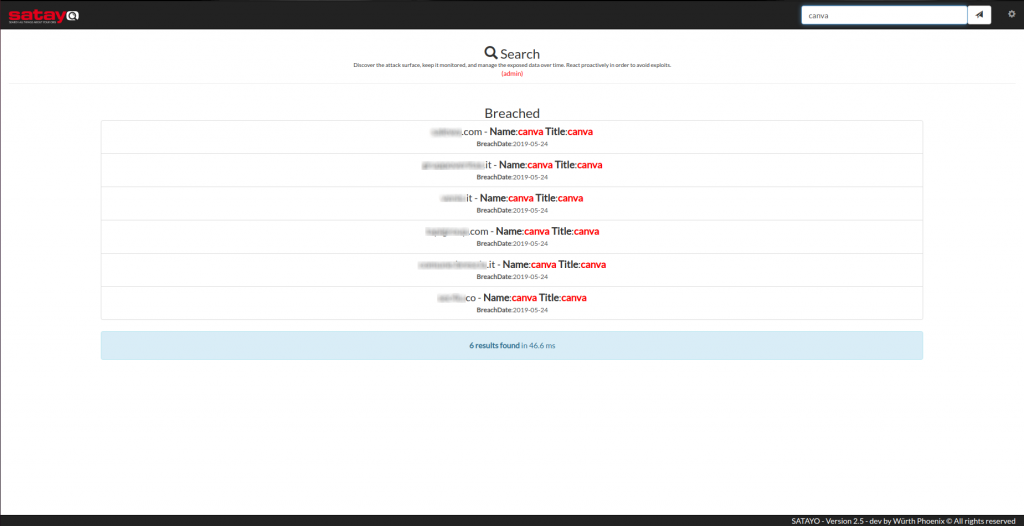
In the coming weeks we’ll index additional types of data, with the aim of making this activity increasingly easier for our users!







